NEOPASS/HARBOR - Harpo Roeder Discusses a New Verification App
https://peertube.futo.org/videos/watch/ecb1f70e-e42f-429f-b536-cbfe4490339e

NEOPASS/HARBOR - Harpo Roeder Discusses a New Verification App
https://peertube.futo.org/videos/watch/ecb1f70e-e42f-429f-b536-cbfe4490339e

E2EE P2P Messaging App
I recently introduced [metered.ca](http://metered.ca) for the STUN/TURN servers and the stability has hugely improved and so i'd like to ask for your feedback if you'd like to try it out.
Data isnt persisted (yet), so each page refresh will clear all keys.
(IMPORTANT: For testing and demo purposes only. This is a work-in-progress and far from finished. It has not been reviewed or audited. Do not use it for sensitive data.)
#P2P #WebRTC #PeerJS #ZeroData #EphemeralData #Encryption #Encrypted #infosec #cryptography #E2EE #BrowserToBrowser #NoInstall #Privacy #Security #Decentralized #Messaging #VideoCall #NoTracking #PrivateMessaging #Prototype #Demo #WorkInProgress #WebDev #TechDevelopment #ChatApp #javascript #InstantMessaging
#FHE #SQL: Fully #Homomorphic #Encrypted #SQL #Database
FHE-SQL is a privacy-preserving database system that enables secure query processing on encrypted data using Fully Homomorphic Encryption (FHE), providing privacy guaranties where an untrusted server can execute encrypted queries without learning either the query contents or the underlying data.

FHE-SQL is a privacy-preserving database system that enables secure query processing on encrypted data using Fully Homomorphic Encryption (FHE), providing privacy guaranties where an untrusted server can execute encrypted queries without learning either the query contents or the underlying data. Unlike property-preserving encryption-based systems such as CryptDB, which rely on deterministic or order-preserving encryption and are vulnerable to frequency, order, and equality-pattern inference attacks, FHE-SQL performs computations entirely under encryption, eliminating these leakage channels. Compared to trusted-hardware approaches such as TrustedDB, which depend on a hardware security module and thus inherit its trust and side-channel limitations, our design achieves end-to-end cryptographic protection without requiring trusted execution environments. In contrast to high-performance FHE-based engines-Hermes, which target specialized workloads such as vector search, FHE-SQL supports general SQL query semantics with schema-aware, type-safe definitions suitable for relational data management. FHE-SQL mitigates the high cost of ciphertext space by using an indirection architecture that separates metadata in RocksDB from large ciphertexts in blob storage. It supports oblivious selection via homomorphic boolean masks, multi-tier caching, and garbage collection, with security proven under the Universal Composability framework.
New #privatbin Instance is up!
🔒 Keep your Notes private and safely hosted in #europe at my own #Privatebin Instance:
3.) For those who aren't using #encrypted #CloudStorage, #Veracrypt is an easy way to create an encrypted container you could then upload to the cloud.
4.) For added security, even on an already encrypted system drive, you can place personal documents inside of a Veracrypt container you've created that can otherwise be inaccessible. Useful for an added layer of #security or on shared workstations depending on scenario.
Some things to note and some use cases for #Veracrypt:
1.) #LUKS provides a way to #encrypt #linux drives. Veracrypt is not the answer for your system drive, but additional drives can be fully #encrypted and mounted using it.
2.) #PlausibleDeniability is what #HiddenContainers offer by having one #password that opens the outer container where you can store files, with a secondary container accessible with a different password.
October 21st is #GlobalEncryptionDay
For those who aren't yet aware of this application that's #CrossPlatform, easy to use, has a helpful #FAQ guide if need be, i'll briefly describe #Veracrypt
With Veracrypt you can create #encrypted containers, hidden secondary containers within encrypted containers, #encrypt drives and it also offers an alternative to #Bitlocker if desired if running a #Windows OS that is NOT a #DualBoot scenario
VeraCrypt is free open-source disk encryption software for Windows, Mac OS X and Linux. In case an attacker forces you to reveal the password, VeraCrypt provides plausible deniability. In contrast to file encryption, data encryption performed by VeraCrypt is real-time (on-the-fly), automatic, transparent, needs very little memory, and does not involve temporary unencrypted files.
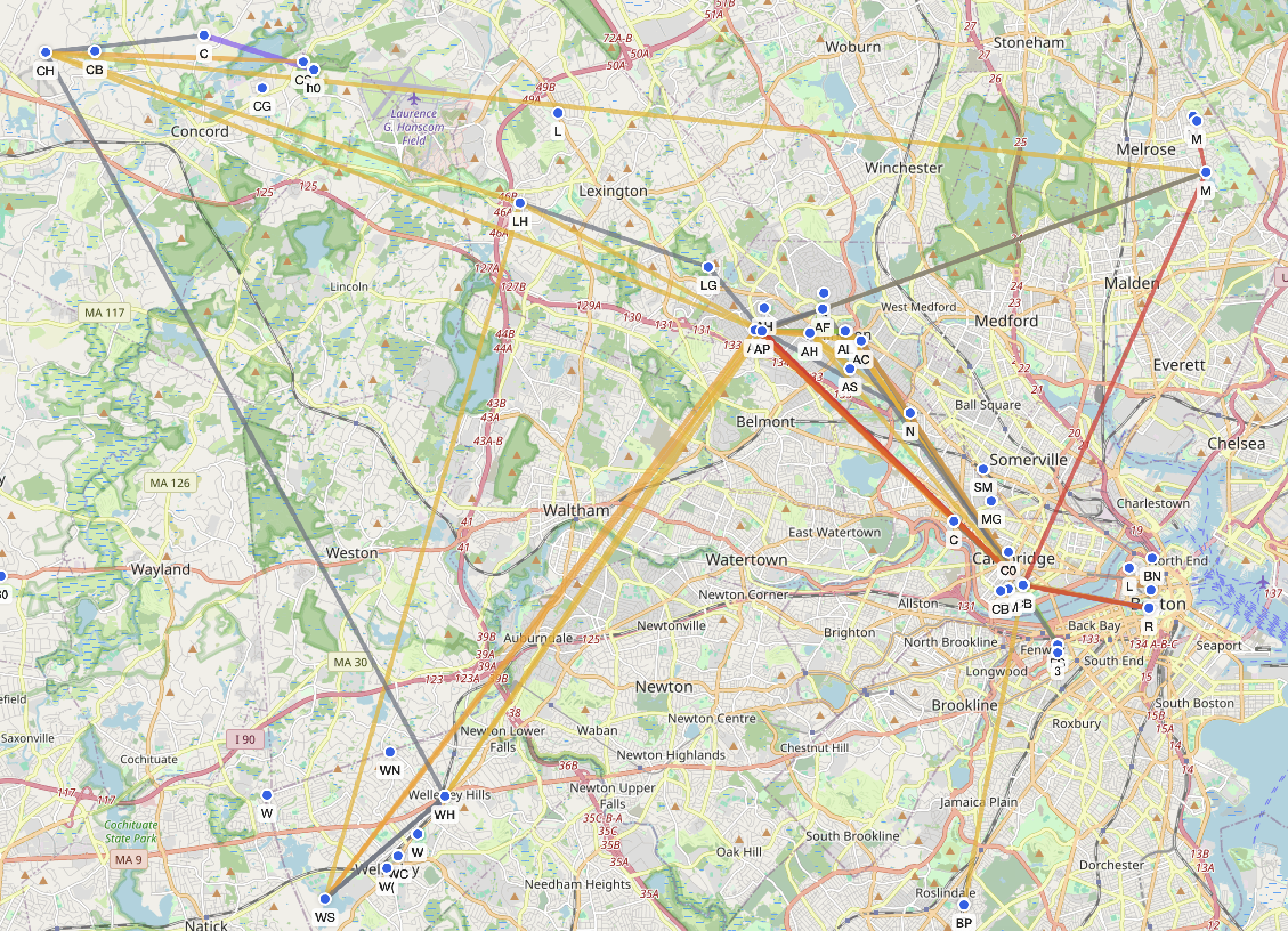
For context this is what the whole #Boston #MeshCore map looks like right now.
The bulk of all traffic is concentrated around the area of #NoKings downtown.
The #mesh is certainly doing its job right now.
Community run, #decentralized, #encrypted, open-access #infrastructure at work.