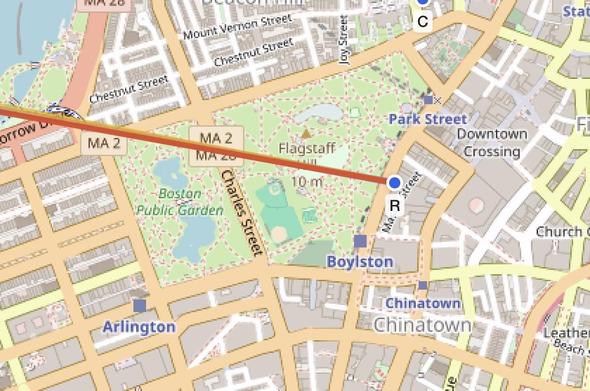
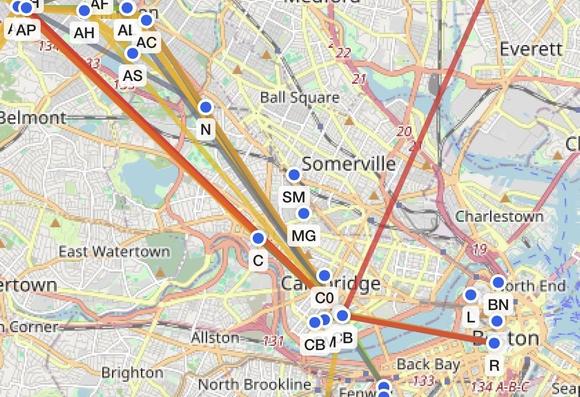
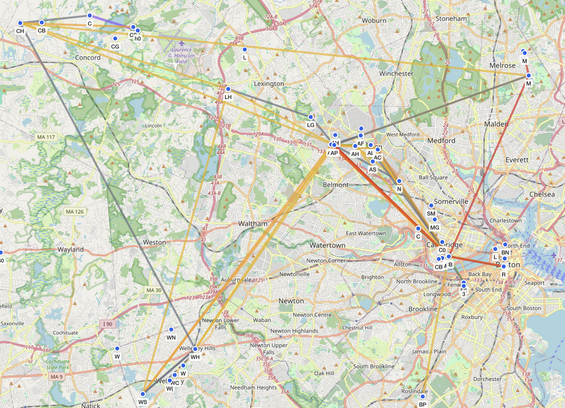
Seeing an increase in #MeshCore traffic around the downtown #Boston area today. Glad to see folks out using it during #NoKings.
This is an example of community-run, #decentralized, off-the-grid #mesh networking #infrastructure playing an important role in society.
Folks are reporting that cell phones are essentially unusable due to the volume of people but MeshCore and Meshtastic are both functioning.