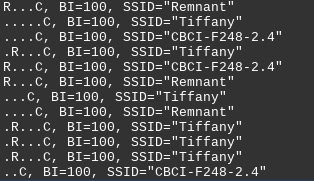
#opsec moment. Never use your name for devices that you carry around. Even if it is just your first name. There was only one woman in this car shop this morning and I'm guessing her name was Tiffany.
That's already enough information to carry out social engineering. While I don't show it here, the phone is a Nokia, so that adds even more ability to confirm and possibly tailor a conversation to win the trust and take advantage of a target.
Think like an attacker. Don't use your name for your devices. Protect yourself.
Humanity is running on fumes. The Earth won’t crash - it disconnects. Read the collapse runbook.
#DeadSwitch #CollapseProtocol #OPSEC #TheLastExtraction
Spy-catcher saw “stupid” tech errors others made. #FBI says he then made his own.
Cops in #Germany Claim They’ve ID’d the Mysterious #Trickbot #Ransomware Kingpin
https://www.wired.com/story/stern-trickbot-identified-germany-bka/
Я к тебе ещё вернусь мой сладкий ягод