BBC good reporting on the ground impact
In theory it should be minimal but in practice airlines have automated many jobs so we’ll see.
BBC good reporting on the ground impact
In theory it should be minimal but in practice airlines have automated many jobs so we’ll see.
If any journalists want a list of top impacted airports to check: https://infosec.exchange/@nieldk/115237394885804514
BBC have Dublin and Cork added.
@cirriustech @GossiTheDog@cyberplace.social here are the “top ten” airports using vMUSE. See any you recognize in Europe as listed in current incident ;) 1. London Heathrow (LHR) 2. Glasgow Airport (GLA) 3. Berlin Schönefeld (SXF) 4. Dublin Airport (DUB) 5. Cork Airport (ORK) 6. Cologne Bonn Airport (CGN) 7. Mazatlán International Airport (Mexico) 8. Zihuatanejo International Airport (Mexico) 9. Monterrey International Airport (Mexico) 10. Velana International Airport (Maldiverne)
ARINC are flying engineers out to airports to try to fix terminals.
Brussels airport, EBBR, have issued this NOTAM: “AD LTD DUE TO AN IT SYSTEM DISRUPTION. AIRLINES ARE TO CANCEL 50
PERCENT OF THEIR DEPARTING PASSENGER FLIGHTS IN THIS TIMEFRAME”
The ARINC incident continues https://www.bbc.co.uk/news/articles/cwy88857llno
Also for anybody interested, ARINC is where the cyber incident is.
ARINC were basically the OG airport network provider, from 1929. ARNIC were sold to Carlyle Group (private equity) in 2007, who sold them to Rockwell Collins in 2013, who sold to United Technologies in 2018, who merged to form Collins Aerospace. Their network looks a mess of US corporate shenanigans… webmail doesn’t even require https yet 😅
Worth noting that airplanes are incredibly safe and resilient after extensive regulation and open and transparent investigations of every air incident…
when you land on the ground, however, air travel is caught in the same cybersecurity bullshit every other industry is caught up in.
After ARINC restored domain controllers from backup, the threat actor got back in and started trashing more stuff. 🫡
The whole thing is a mess, they probably want to pause, take a breathe, and think about flushing out attacker before rebuilding things.
Berlin Airport ran at 70% delays yesterday
I’ve confirmed today that Heathrow, Berlin and Dublin all still have no Muse terminals restored. I haven’t checked other airports. It’s even more complicated because Muse both processes and stores biometrics of passengers.
"Before we reconnect our system, we must be 100% sure that there are no malware programmes left," the BER spokesman said.
The Europe airlines ransomware situation is a variant of Hardbit ransomware, which doesn’t have a portal and is incredibly basic.
They’ve had to restart recovery again as the devices keep getting reinfected. I’ve never seen an incident like it. Somebody like the NCSC needs to go in and help them with IR.
Look at Dublin airport, reporters starting to realise it never actually got fixed 😅
https://www.thejournal.ie/dublin-airport-issues-timeline-fix-6824817-Sep2025/
Flight delays today:
Heathrow 78%
Brussels 79%
Dublin 68%
Berlin 86%
All are vMuse. London City isn't on vMuse, they're at 35% as a point of comparison.
NPR and PBS have somehow managed to run a completely bollocks article linking the EU airport thing to AI - the article itself written by an AI cybersecurity vendor. https://www.wgcu.org/science-tech/2025-09-23/detection-expert-says-hackers-likely-used-ai-to-penetrate-airport-system
It's completely false. The payloads used in this one are detected by free Defender AV with a decade old static AV detections. This is not some cyber mega attack by a ransomware group: it's extremely poor security hygiene.
If your board is concerned about the EU ransomware thing - there is no need to be concerned. It is not a wider issue.
It wouldn't surprise me if the person arrested turns out to be an employee trying to do incident response or some such (I'm not saying they're guilty, at all).
It's an extremely unusual incident and essentially involves lax cybersecurity and confused response.
ARINC/Collins have been unable to restore the systems in Brussels airport so they are ripping out and replacing everything.
HT @0xThiebaut
There’s a bit more info here: https://www.aviation24.be/airports/brussels-airport-bru/accelerate-rollout-of-new-check-in-system-after-cyberattack-on-collins-aerospace-software/
They will keep cancelling 10% of flights each day for the foreseeable future.
Flight delays today:
Heathrow 90%
Brussels 89%
Dublin 84%
Berlin 86%
All are vMuse. London City isn't on vMuse, they're at 33% as a point of comparison.
In terms of recovery:
- Heathrow going nowhere, manual workarounds to issue bag tags and boarding passes, airlines have been told to maintain continency measures until w/c October 6th
- Brussels Airport are manual workarounds to issue bag tags and boarding passes, and are ripping out all their vMuse terminals and Muse IT infrastructure and replacing them
- Dublin making progress to starting restoration
- Berlin manual workarounds to issue bag tags and boarding passes
Aer Lingus have got their check in terminals working again at Dublin Airport
Flight delays today:
Heathrow 95%
Brussels 94%
Dublin 76%
Berlin 80%
All are vMuse. London City isn't on vMuse, they're at 33% as a point of comparison.
If you're traveling via Heathrow, Brussels, Dublin or Berlin airport this weekend - flights are running fine but average 90% delays still.
Check in online (rather than at the airport). If you need to baggage drop add about ~30 mins to your usual schedule.
Expectation is this will last for about another week or two due to the ongoing issues at ARINC/Collins/RTX.
The exceptions are British Airways and Aer Lingus, who are okay now and extra staffed too.
Flight delays today:
Heathrow 81%
Brussels 81%
Dublin 73%
Berlin 77%
I'm probably going to stop tracking this one for now, basically the impacted airports are mostly okay to travel through, check in online basically.
Airports did a really good at being resilient, by falling back to paper and/or using online check in.
Collins, less so.
Okay, there’s an incredible update to the RTX/Collins/ARINC airport ransomware situation
Everest are claiming the incident, saying they exfiltrated a very large amount of data, including passenger data.
They’re really salty and claim it wasn’t ransomware.. what they aren’t aware of (this isn’t in the story) is an in parallel, somebody also tried to deploy ransomware.
Overall the problem is: shite security.
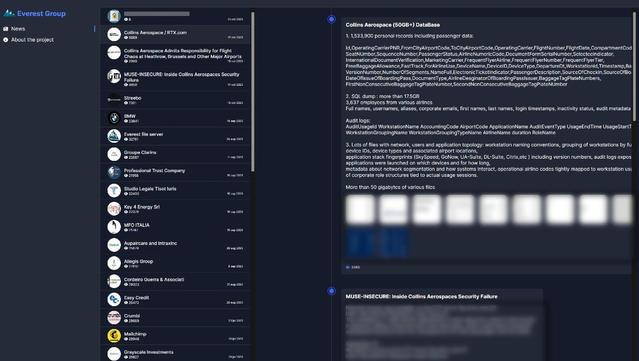
The Everest hacking group is claiming to have the flight data of more than 1.5m passengers and thousands of airline employees; says Collins Aerospace is responsible for airport shutdowns, not ransomware.
Another update on the RTX/Collins/ARINC story https://www.linkedin.com/posts/alon-gal-utb_looks-like-everest-group-targeted-collins-activity-7387117440020844545-5l0X
Alon Gal has confirmed that, yes, the FTP credentials Everest used for their (separate) incident were in a historic infostealer dump from 2022. All they did was FTP in. Check out the screenshots 💀

Looks like Everest group targeted Collins Aerospace on the same week they had the huge ransomware attack leading to shutdowns of major airlines. Everest was allegedly able to exfiltrate a bunch of sensitive data from the FTP of Collins Aerospace by abusing credentials that Hudson Rock traced to a 2022 Redline Infostealer infection that we had years prior to the attack. Full blog (3 minutes read) - https://lnkd.in/dfyXiZGm Everest are claiming that Collins Aerospace purposefully shut down their own systems in order to collect insurance money but that's nonsense, they just weren't aware of another ransomware operator attacking the company roughly at the same time. Interesting story. The images show the TOX communication between Everest and a RTX representative, the attack method, the allegations, and a screenshot from Cavalier of the credentials used for the attack. Stay safe, feel free to ask us for an ethical disclosure to get rid of legacy credentials that will be used in attacks years ahead - https://lnkd.in/dmj9R5xj
I’ve confirmed with one of the airlines they weren’t told about this, and it impacts their passenger data so this will probably get spicy.
ARINC’s network border looks like it was transported from three decades ago, they gotta invest in it.
Dublin Airport have confirmed the RTX/Collins/ARINC incident included passenger data for their airport. HT @metacurity
It actually includes lots more airports.
What am I looking at exactly?
Thanks. The rest of the thread wasn't visible to me when I commented. It is now!
@GossiTheDog I can totally imagine someone doing that at a technical level; but how did they get away with that setup in european airports?
Is there some esoteric reading of the text where fingerprints aren't a data privacy issue; or are we doing don't ask/don't tell compliance now?
@GossiTheDog
I’m suddenly a lot less annoyed the terminal at the Berlin airport refused to help me, forcing me into wandering around looking for my airline counter and discovering I was too early and would have to wait for them to open.
It had a passport-reading slot if I remember correctly but I didn’t get far enough along before being prompted to use it. I’m sure some of my data was stolen (again) but I’ll take the small wins where I can get them.
@GossiTheDog Is there are trustworthy collection of all the known technical detail somewhere?
As in, one that avoids guesses and clickbait assumptions, because it seems like this story has enough material.
Need that to share security awareness.
Totally not to laugh about it.
There still are regular announcements of possible delays and cancellations due to an IT incident at an external service provider, and please check with your air line.
The airline I am flying with today also sent me a text message to avoid checked in luggage and to please check in online and/or print a boarding pass at home.
@GossiTheDog
I'm looking forward how the authorities are looking into these incidents, as Airports are classified as critical Infrastructure and as such for sure fell under the NIS (the original one) and now under NIS II.
They were subject to have Business Continuity Plans, as well as making sure their supply chain has all her ducks in row.
Well, who am I kidding. Nothing will happen to anyone. SADLY. As Management is directly responsible and subject to penalties for failing these obligations.
@GossiTheDog I guess so-called fingerprint'ers (TM) will be the next runner.
Certainly will i hand over my biometric data freely to any government. I have nothing to hide. And what could happen if they get hacked, right?
@GossiTheDog I was recently at a social gathering with someone who used to sell products in the biometrics space, and they asked about how that plays today.
I broke the news gently.