https://youtu.be/B5nxLVKbhKc #Cybersecurity #AIinSecurity #CyberPredictions #FutureOfSecurity #ZeroTrust #AIThreats #CyberDefense #SecurityAutomation #DigitalTrust #IdentitySecurity #CISO #InfoSec #CyberRisk #TechLeadership
https://youtu.be/B5nxLVKbhKc #Cybersecurity #AIinSecurity #CyberPredictions #FutureOfSecurity #ZeroTrust #AIThreats #CyberDefense #SecurityAutomation #DigitalTrust #IdentitySecurity #CISO #InfoSec #CyberRisk #TechLeadership
100 idées de workflows cybersécurité avec n8n, et c’est open source, prêt à l’emploi ⬇️
Le dépôt GitHub de CyberSecurityUP liste 100 idées de blueprints d’automatisation pour n8n, couvrant l’offensive (Red Team), la défense (Blue Team/SOC), l’AppSec/DevSecOps et la sécurité plateforme. Chaque workflow est décrit avec :
- Un objectif simple (ex: détection de beaconing, rotation de certifs TLS)
- Les intégrations nécessaires (APIs, outils comme Shodan, MISP, Semgrep, etc.)
- Un schéma de flux type (nœuds HTTP Request, IF/Switch, Cron, etc.)
⚔️ Pour les Red Teams (30 workflows) :
- Hub de recon de sous-domaines (Subfinder + Shodan)
- Détection de changements de surface d’attaque (Nmap/Naabu)
- Orchestration de campagnes GoPhish ou tests d’évasion AV/EDR
- Gestion d’infra C2 (création, hygiène, extinction planifiée)
🛡️ Pour les Blue Teams/SOC (35 workflows) :
- Ingestion & normalisation de feeds TI (OTX, MISP, VirusTotal)
- Micro-SOAR pour enrichir les IOC à la demande
- Détection de tunneling DNS
- Automatisation de blocages via Slack + génération de briefings quotidiens
♻️ Pour l’AppSec/DevSecOps (25 workflows) :
- SAST à la PR (Semgrep), DAST nocturne (ZAP)
- Analyse de composition logicielle (Trivy/Grype + SBOM)
- Scanning IaC (Checkov), détection de secrets, contrôles CSP/CORS
📜 Sécurité plateforme & gouvernance (10 workflows) :
- Digest de vulnérabilités priorisé (NVD + EPSS/KEV + CMDB)
- Planificateur de rotation de certifs TLS
- Vérificateur d’intégrité des sauvegardes (RPO)
- Purple loop pour boucler exercices Red/Blue Team
⚠️ Bonnes pratiques incluses :
- Utiliser `HTTP Request` pour les APIs, `Execute Command` pour les scanners
- Gérer les credentials n8n proprement + idempotence (clés de déduplication)
📌 Le dépôt : https://github.com/CyberSecurityUP/n8n-CyberSecurity-Workflows
Pourquoi c’est utile ?
- Gagner du temps: pas besoin de réinventer la roue, les schémas sont prêts à adapter.
- Collaboratif: la communauté peut contribuer ou fork le projet.
- Pédagogique: idéal pour comprendre comment enchaîner des outils concrets (ex: comment lier un scan Trivy à une alerte Slack).
Ensuite, adaptez chaque workflow à votre contexte spécifique (outils, API keys, politiques internes), et ajoutez-y vos agents IA si vous le souhaitez
📢les workflows offensifs doivent rester dans un périmètre autorisées et encadré
💡 Un workflow qui vous manque ? Le dépôt est open source: proposez vos idées ou améliorations via les issues.
#Cybersec #Automatisation #n8n #RedTeam #BlueTeam #DevSecOps #SOC #OpenSource #SecurityAutomation #PurpleTeam #AppSec #DFIR #ThreatIntel #Workflows #GitHub
Zero Trust Security Model Explained: Is It Right for Your Organization?
1,135 words, 6 minutes read time.
When I first walked into a SOC that proudly claimed it had “implemented Zero Trust,” I expected to see a modern, frictionless security environment. What I found instead was a network still anchored to perimeter defenses, VPNs, and a false sense of invincibility. That’s the brutal truth about Zero Trust: it isn’t a single product or an off-the-shelf solution. It’s a philosophy, a mindset, a commitment to questioning every assumption about trust in your organization. For those of us in the trenches—SOC analysts, incident responders, and CISOs alike—the question isn’t whether Zero Trust is a buzzword. The real question is whether your organization has the discipline, visibility, and operational maturity to adopt it effectively.
Zero Trust starts with a principle that sounds simple but is often the hardest to implement: never trust, always verify. Every access request, every data transaction, and every network connection is treated as untrusted until explicitly validated. Identity is the new perimeter, and every user, device, and service must prove its legitimacy continuously. This approach is grounded in lessons learned from incidents like the SolarWinds supply chain compromise, where attackers leveraged trusted internal credentials to breach multiple organizations, or the Colonial Pipeline attack, which exploited a single VPN credential. In a Zero Trust environment, those scenarios would have been mitigated by enforcing strict access policies, continuous monitoring, and segmented network architecture. Zero Trust is less about walls and more about a web of checks and validations that constantly challenge assumptions about trust.
Identity and Access Management: The First Line of Defense
Identity and access management (IAM) is where Zero Trust begins its work, and it’s arguably the most important pillar for any organization. Multi-factor authentication, adaptive access controls, and strict adherence to least-privilege principles aren’t optional—they’re foundational. I’ve spent countless nights in incident response chasing lateral movement across networks where MFA was inconsistently applied, watching attackers move as if the organization had handed them the keys. Beyond authentication, modern IAM frameworks incorporate behavioral analytics to detect anomalies in real time, flagging suspicious logins, unusual access patterns, or attempts to elevate privileges. In practice, this means treating every login attempt as a potential threat, continuously evaluating risk, and denying implicit trust even to high-ranking executives. Identity management in Zero Trust isn’t just about logging in securely; it’s about embedding vigilance into the culture of your organization.
Implementing IAM effectively goes beyond deploying technology—it requires integrating identity controls with real operational processes. Automated workflows, incident triggers, and granular policy enforcement are all part of the ecosystem. I’ve advised organizations that initially underestimated the complexity of this pillar, only to discover months later that a single misconfigured policy left sensitive systems exposed. Zero Trust forces organizations to reimagine how users and machines interact with critical assets. It’s not convenient, and it’s certainly not fast, but it’s the difference between containing a breach at the door or chasing it across the network like a shadowy game of cat and mouse.
Device Security: Closing the Endpoint Gap
The next pillar, device security, is where Zero Trust really earns its reputation as a relentless defender. In a world where employees connect from laptops, mobile devices, and IoT sensors, every endpoint is a potential vector for compromise. I’ve seen attackers exploit a single unmanaged device to pivot through an entire network, bypassing perimeter defenses entirely. Zero Trust counters this by continuously evaluating device posture, enforcing compliance checks, and integrating endpoint detection and response (EDR) solutions into the access chain. A device that fails a health check is denied access, and its behavior is logged for forensic analysis.
Device security in a Zero Trust model isn’t just reactive—it’s proactive. Threat intelligence feeds, real-time monitoring, and automated responses allow organizations to identify compromised endpoints before they become a gateway for further exploitation. In my experience, organizations that ignore endpoint rigor often suffer from lateral movement and data exfiltration that could have been prevented. Zero Trust doesn’t assume that being inside the network makes a device safe; it enforces continuous verification and ensures that trust is earned and maintained at every stage. This approach dramatically reduces the likelihood of stealthy intrusions and gives security teams actionable intelligence to respond quickly.
Micro-Segmentation and Continuous Monitoring: Containing Threats Before They Spread
Finally, Zero Trust relies on micro-segmentation and continuous monitoring to limit the blast radius of any potential compromise. Networks can no longer be treated as monolithic entities where attackers move laterally with ease. By segmenting traffic into isolated zones and applying strict access policies between them, organizations create friction that slows or stops attackers in their tracks. I’ve seen environments where a single compromised credential could have spread malware across the network, but segmentation contained the incident to a single zone, giving the SOC time to respond without a full-scale outage.
Continuous monitoring complements segmentation by providing visibility into every action and transaction. Behavioral analytics, SIEM integration, and proactive threat hunting are essential for detecting anomalies that might indicate a breach. In practice, this means SOC teams aren’t just reacting to alerts—they’re anticipating threats, understanding patterns, and applying context-driven controls. Micro-segmentation and monitoring together transform Zero Trust from a static set of rules into a living, adaptive security posture. Organizations that master this pillar not only protect themselves from known threats but gain resilience against unknown attacks, effectively turning uncertainty into an operational advantage.
Conclusion: Zero Trust as a Philosophy, Not a Product
Zero Trust is not a checkbox, a software package, or a single deployment. It is a security philosophy that forces organizations to challenge assumptions, scrutinize trust, and adopt a mindset of continuous verification. Identity, devices, and network behavior form the pillars of this approach, each demanding diligence, integration, and cultural buy-in. For organizations willing to embrace these principles, the rewards are tangible: reduced attack surface, limited lateral movement, and a proactive, anticipatory security posture. For those unwilling or unprepared to change, claiming “Zero Trust” is little more than window dressing, a label that offers the illusion of safety while leaving vulnerabilities unchecked. The choice is stark: treat trust as a vulnerability and defend accordingly, or risk becoming the next cautionary tale in an increasingly hostile digital landscape.
Call to Action
If this breakdown helped you think a little clearer about the threats out there, don’t just click away. Subscribe for more no-nonsense security insights, drop a comment with your thoughts or questions, or reach out if there’s a topic you want me to tackle next. Stay sharp out there.
D. Bryan King
Sources
- NIST Special Publication 800-207: Zero Trust Architecture
- CISA Zero Trust Maturity Model
- MITRE ATT&CK® Framework
- CrowdStrike: The Rise of Zero Trust Security
- Mandiant Threat Intelligence Reports
- Schneier on Security Blog
- KrebsOnSecurity
- Verizon Data Breach Investigations Report (DBIR)
- SANS Whitepaper: Zero Trust Security
- Black Hat Briefings: Zero Trust Talks
- DEF CON Conference Talks on Network Security
- Microsoft Security Blog: The Future of Zero Trust
- Palo Alto Networks: What is Zero Trust?
- Gartner Market Guide for Zero Trust Network Access
- IBM Zero Trust Security Resources
Disclaimer:
The views and opinions expressed in this post are solely those of the author. The information provided is based on personal research, experience, and understanding of the subject matter at the time of writing. Readers should consult relevant experts or authorities for specific guidance related to their unique situations.
#accessManagement #adaptiveSecurity #attackSurfaceReduction #behavioralAnalytics #breachPrevention #byodSecurity #ciso #cloudSecurity #cloudFirstSecurity #colonialPipeline #complianceEnforcement #continuousMonitoring #cyberResilience #cybersecurityAwareness #cybersecurityCulture #cybersecurityReadiness #cybersecurityStrategy #deviceSecurity #digitalDefense #edr #endpointSecurity #enterpriseSecurity #iam #identityVerification #incidentResponse #internalThreats #iotSecurity #lateralMovement #leastPrivilege #mfa #microSegmentation #mitreAttck #multiFactorAuthentication #networkSecurity #networkSegmentation #networkVisibility #nistSp800207 #perimeterSecurity #privilegedAccessManagement #proactiveMonitoring #proactiveSecurity #ransomwarePrevention #riskManagement #secureAccess #securityAutomation #securityBestPractices2 #securityFramework #securityMindset #securityOperations #securityPhilosophy #siem #socAnalyst #solarwindsBreach #threatDetection #threatHunting #threatIntelligence #zeroTrust #zeroTrustArchitecture #zeroTrustImplementation #zeroTrustModel #zeroTrustSecurity
Spent the day writing scripts to pull various threat intel feed info from our vendors and sync them with various firewall and WAF technology.Python made this a breeze and it will hopefully result in a reduced ticket count coming out of the SOC.
This comprehensive guide explores how AI and machine learning are revolutionizing vulnerability reconnaissance and security testing methodologies. **AI-Enhanced Recon Framework**: The article demonstrates integration of traditional tools (Amass, Subfinder, httpx, Nuclei) with Large Language Models for automated analysis, summarization, and payload generation. **Key AI Applications**: LLMs assist in rapid analysis of recon data, automated vulnerability prioritization, and generation of test payloads, reducing manual grunt work while preserving human creativity for exploitation logic. **Practical Implementation**: The author provides GitHub-style examples, code snippets, and LLM prompts that can be adapted for legitimate security research, including scripts for automated subdomain analysis and vulnerability scanning workflows. **Human-AI Collaboration**: The framework emphasizes that AI speeds up analysis and data processing but cannot replace human intuition for creative exploitation chaining and sophisticated attack vectors. **Ethical Guidelines**: The article maintains strict focus on authorized testing through proper scope, emphasizing use within bug bounty programs, penetration test engagements, and controlled lab environments. **Tool Integration**: Demonstrates how AI enhances traditional recon pipelines by automating data correlation, pattern recognition in recon results, and intelligent filtering of false positives, making researchers more efficient while maintaining security standards. **Tactical Advantage**: Shows how AI-assisted recon can process vast amounts of data faster, identify subtle patterns humans might miss, and provide researchers with actionable intelligence more rapidly than manual methods. #infosec #BugBounty #Cybersecurity #AIRecognition #SecurityAutomation #PenetrationTesting
https://osintteam.blog/modern-recon-how-hackers-use-ai-to-hunt-vulnerabilities-smarter-5a3cd87c3671?source=rss------bug_bounty-5
Red and blue teams breaking down their silos and working in real time—imagine a cybersecurity defense that evolves with every simulated threat. Curious how continuous purple teaming is rewriting the playbook?
#purpleteaming
#cyberdefense
#breachandattacksimulation
#mitreattack
#redteam
#blueteam
#securityautomation
#continuousvalidation
#cybersecuritystrategy
💥Automating Cybersecurity Workflows with Callgoose SQIBS
✅ Real-Time Threat Detection
✅ Automated Incident Remediation
✅ Compliance on Autopilot
✅ Event-Driven Workflows
Read More : https://callgoose.com/u/HI
#CallgooseSQIBS #CyberSecurity #AutomateSecurity #IncidentResponse #ThreatDetection #SIEM #Splunk #ElasticSecurity #ComplianceAutomation #SecurityAutomation #NoMoreManual #DevSecOps
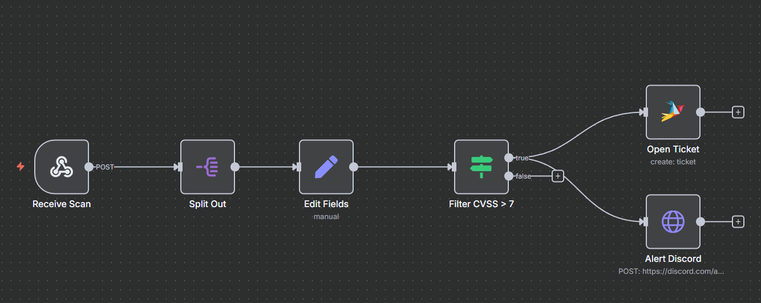
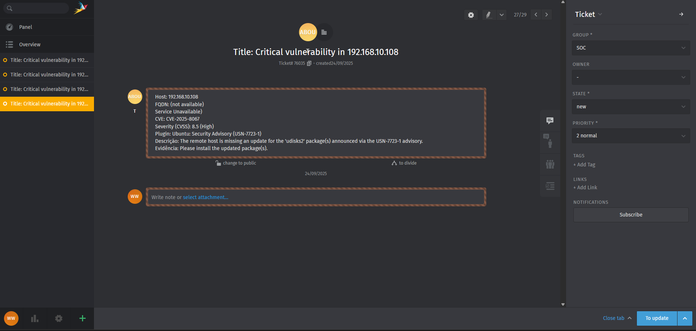
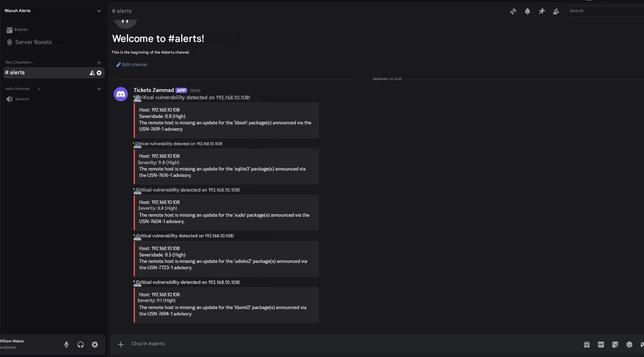
Can you build a complete vulnerability management pipeline using only open source tools?
Our latest blog post features guest author William Weber, an Information Security Professional who built a production-ready vulnerability management system using just these four:
🔍 @greenbone
⚙️ #N8n
🎫 #Zammad
📢 #Discord
👉 Read the full breakdown: https://zammad.com/en/blog/vulnerability-management-process-with-zammad
#OpenSource #CyberSecurity #OpenVAS #SOC #SecurityAutomation
Imagine your network acting like a digital fortress on autopilot—automatically sealing breaches before they even happen. Curious how automated microsegmentation is revolutionizing Zero Trust? Read on to discover more.
#microsegmentation
#zerotrust
#networksecurity
#cybersecurityautomation
#lateralmovement
#identitysecurity
#cloudsecurity
#securityautomation
#infosec