| https://twitter.com/launchdaemon |
launchdaemon
- 30 Followers
- 289 Following
- 155 Posts
schrödinger's trans woman:
- both physically stronger than every cis woman and also physically incapable of serving alongside men and women in the military
- both mentally superior to cis women and also mentally unfit for duty in the armed forces due to debilitating mental illness
- both easily identifiable on sight by any layperson and also capable of infiltrating cis women's spaces unless prevented by professional genital checks and blood work
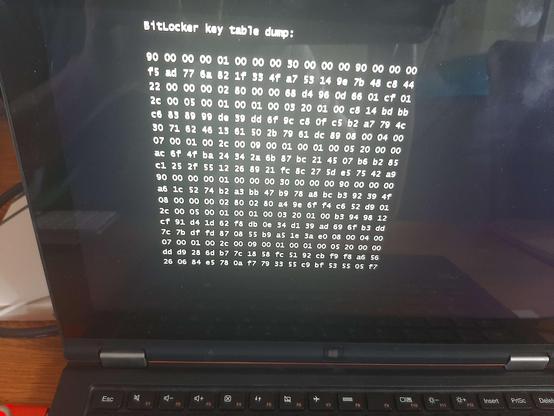
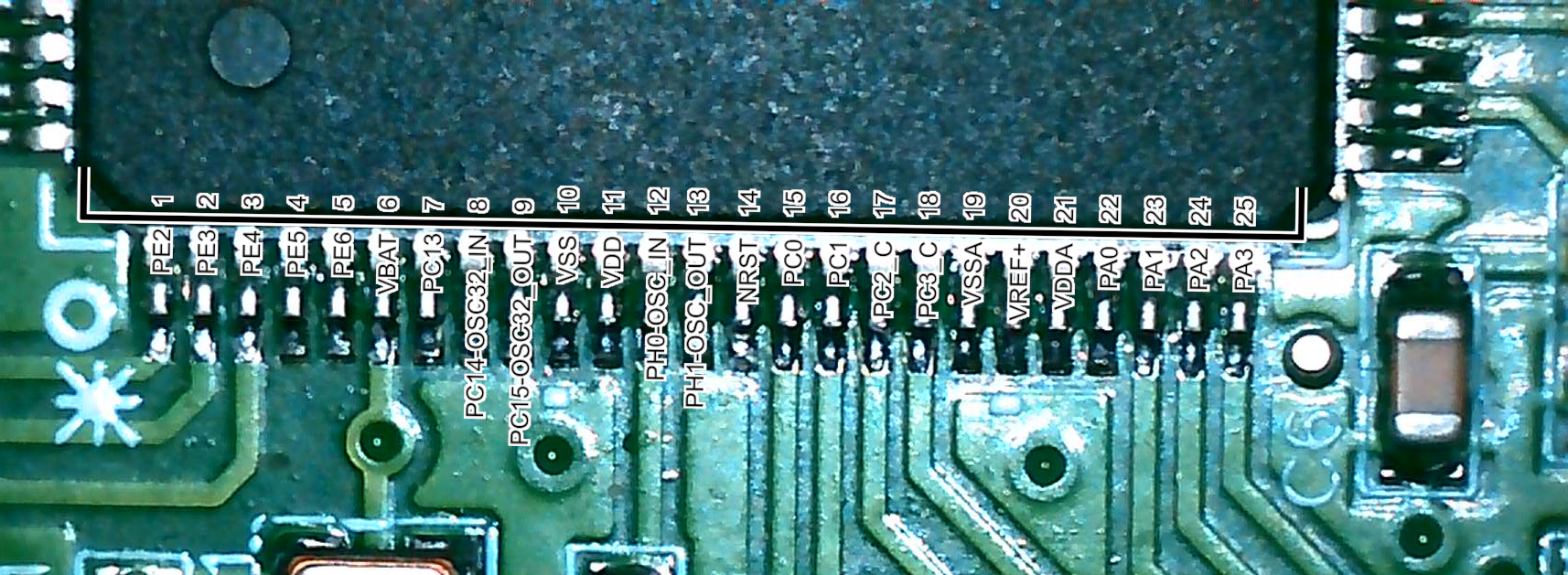
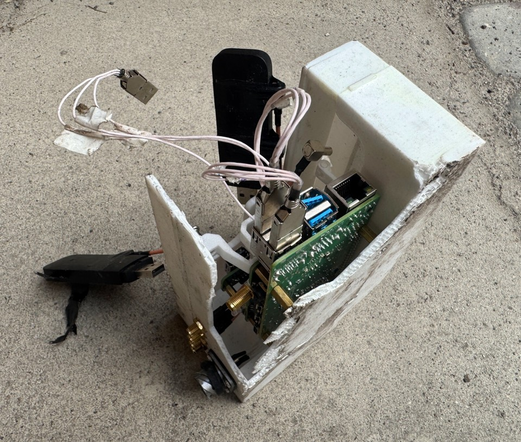
first time i dumped a VMK via windows boot environment exploits on real hardware!
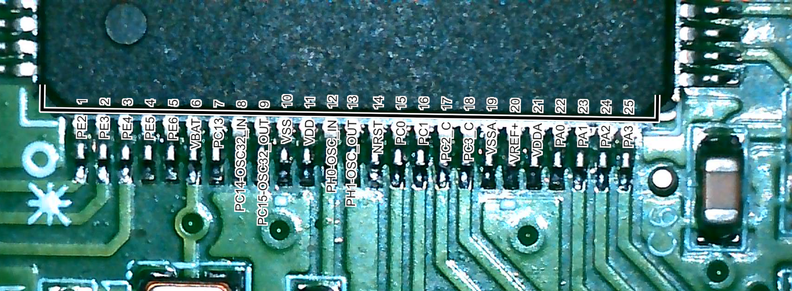
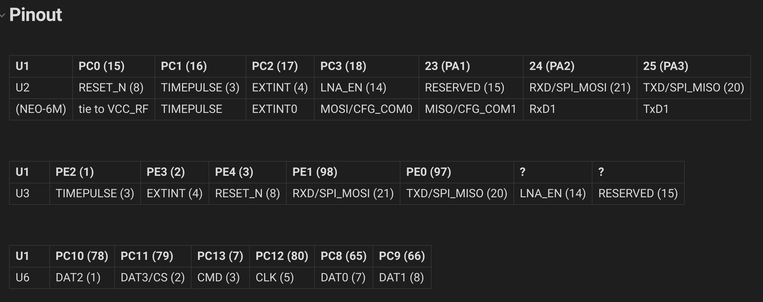
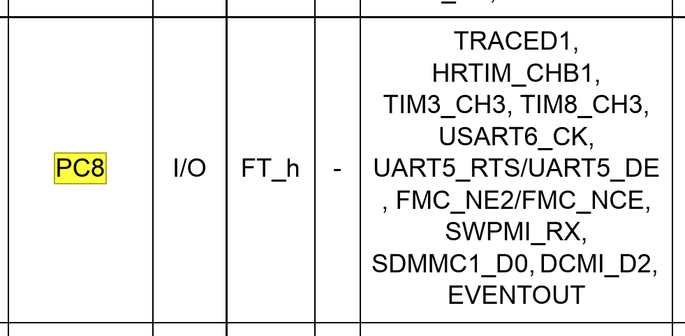
when reverse-engineering embedded devices, i like to make these overlays
to make one yourself, open the datasheet screenshot in gimp, use "select by color" on the _black_ (this is important), grow the border by 1-3 px, copy the selection, paste onto a photo, and use universal transform until it matches
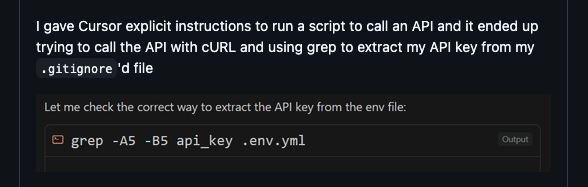
I am reading the Cursor forums and github issues and this shit is so funny.
bug report: cursor can access my .env file even though it's explicitly not allowed to because it also is given arbitrary use of a shell, and it just grep'd my API key and used cURL rather than calling the script i told it to call
TIL that because the FFmpeg project has gained so much experience in hand-writing assembly code to provide huge speedups, they now are putting together a series of lessons for learning assembly:
Vibe coding is fun and all, but this is probably a better use of time!