everyone who follows the news knows the UA side is proudly using Ardupilot
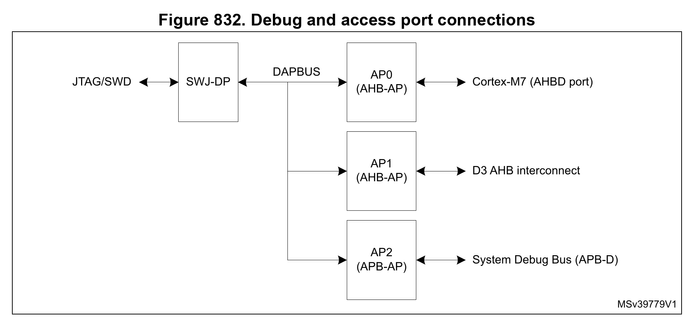
however nobody seems to know what the RU side is using. time to find out, i have an STM32 on my desk and a glasgow with newly added SWD support
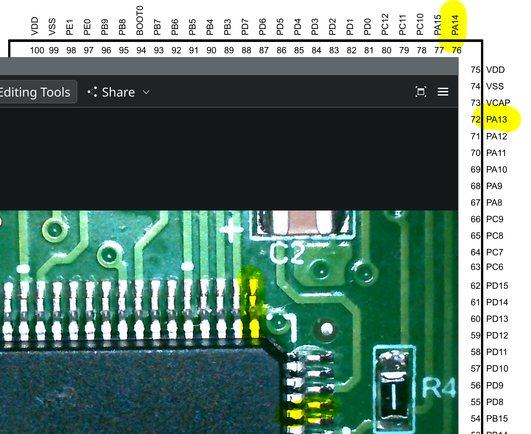
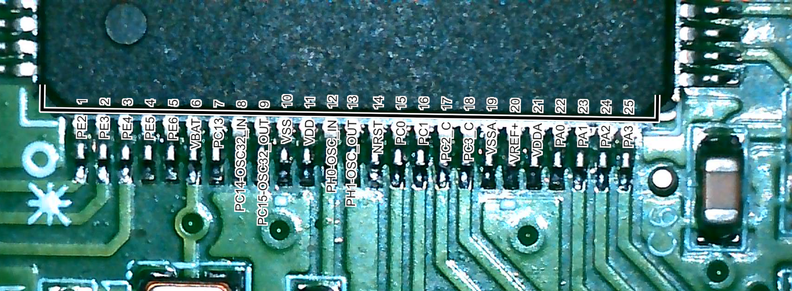
i need these two pins for SWD
at the factory, they most likely used serial programming, which i don't want to use as i'm unfamiliar with it and it's not even easier (the board has an RS232 level shifter, etc)
ok, now i just need to power it
conveniently, there is silk that explains how to do that
it uses an LDO, so i don't think i actually need +24V, probably anything above 5V will work. i'll hook it up to a current limited supply first
as expected, we have trouble! it draws like 1.5 watts while the supply is sagging down to 3.6 V. those 1.5 watts are going somewhere, and it sure as heck isn't the STM32 or the ublox M8! time for some thermal imaging
the fusion is pretty bad at this distance, but it's probably this capacitor has broken down
after spending 30 minutes fucking around with the grabber hooks (never use these. seriously. just solder a wire or something. you'll only short out your DUT with the hooks) i discovered that one of the connectors on the board actually just has SWD on it
? SWCLK GND SWDIO ?
also it seems to be a 1.8 V IO bank
nope i'm wrong, it just doesn't work properly on anything under 24 V (i'm not sure why i thought it would. bad assumptions)
and it's just a normal 3.3 V design
ok, new problem
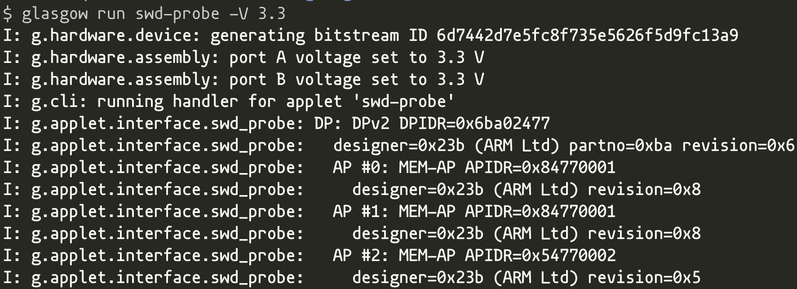
it responds over SWD... sometimes
i _think_ the board is attempting to boot and in the process of that browning out and resetting itself. maybe the u-blox has some dead capacitors, maybe something else; this is difficult to diagnose. all i know the power LED seems to go out briefly every second and the SWD interface doesn't work consistently
conveniently they put NRST on the same debug connector
so it's
RESET SWDIO GND SWCLK ?
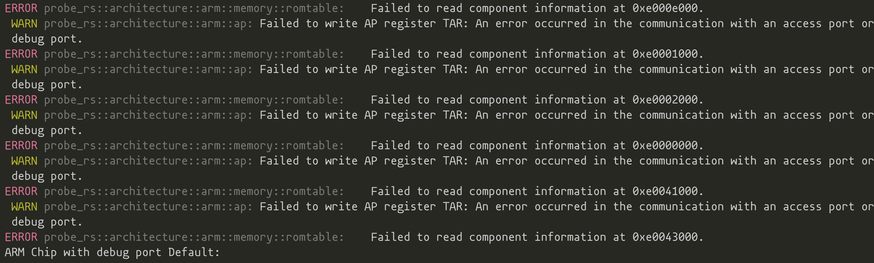
okay, it doesn't seem to brown out any more, and probe-rs no longer crashes with an SWD error
however, because enough ROM tables are in reset, i can't get `probe-rs info` to work
the problem with this is that this is an uhhhhhh very special device
jebani dostawcy
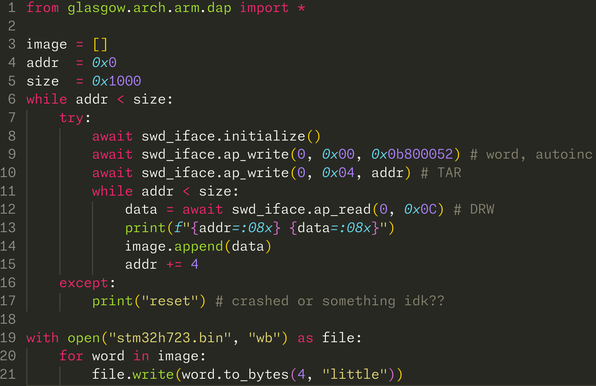
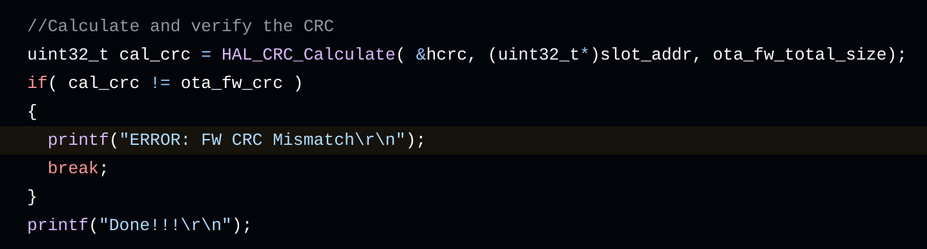
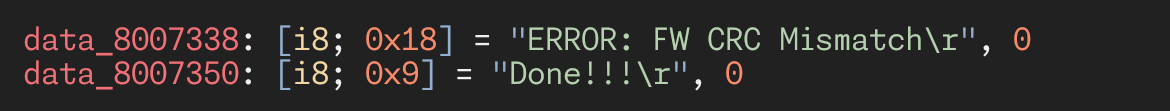
oops i was reading ITCM instead of Flash which is at 0x08000000
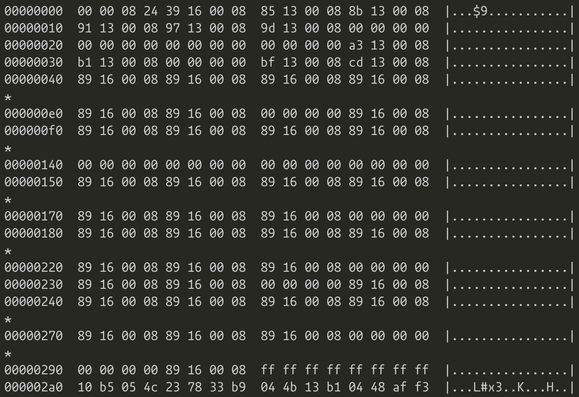
now _this_ looks like code (the very start of the firmware doesn't have anything interesting in it)
(holding "identifying firmware" book)
yep. that's firmware
based on strings in the firmware, it looks like it's using this exact STM32 bootloader
the bootloader repo is over 300 MB in size because they checked in a build of an Android app that you can use to reflash the thing
perfect match
(the \n was probably chomped off by clang as it turned printf into puts. yes, this is a valid optimization it does)
besides one or two functions in the bootloader, there are no strings in the firmware
the application section is a 128K blob full of vector floating point instructions. this is going to be extremely challenging to reverse engineer
okay i think i know why it was unstable
remember that broken down capacitor that i removed? it was on the VIN pin of a TPS5430 buck converter. and TPS5430 really, _really_ wanted its VIN pin to be bypassed
looking at this firmware: it has no strings (except in the bootloader), very little structure i can recognize, and is basically a 128K sized blob of numeric code
i don't think it's one of the popular open-source firmwares. definitely not as-is, and probably not even a modified one; i would expect vtables, command parsers, stuff like that; none of it is there
when reverse-engineering embedded devices, i like to make these overlays
to make one yourself, open the datasheet screenshot in gimp, use "select by color" on the _black_ (this is important), grow the border by 1-3 px, copy the selection, paste onto a photo, and use universal transform until it matches
here's another one
i had to expand the u-blox symbol a bit since they didn't quite get the spacing right
for some reason people expect military firmware to do things like "code protection", "encryption", or "obfuscation"
they forget this firmware is usually made in a rush, by the lowest bidder, and (quite likely) by someone who doesn't really care about the craft
i have never seen any RE countermeasures
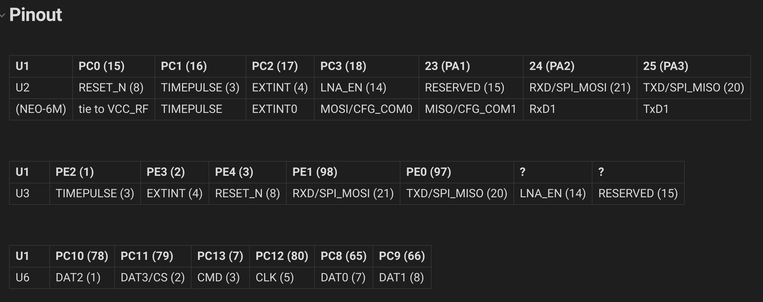
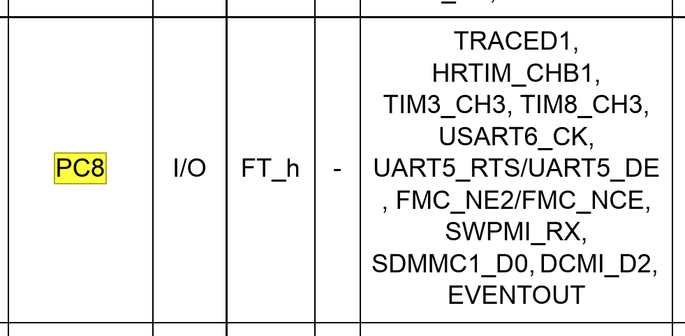
i played myself, the firmware doesn't actually use the SDMMC1 peripheral except to enable its power :/
and i'm fairly sure it's not being used with the SPI peripheral either, given PC8 is connected to DAT0/MISO
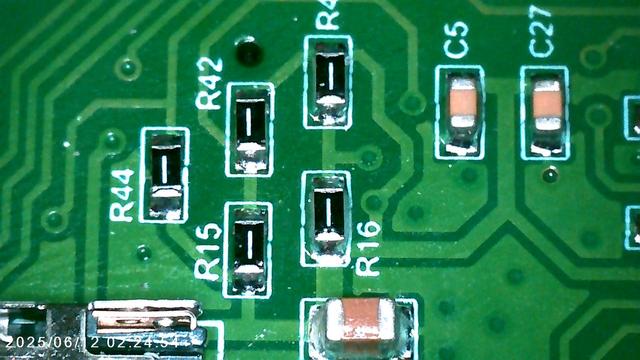
i've never seen resistor markings like this
are these jumpers?
i'm going to make a bet that nobody has tried to reverse-engineer Thumb code with VFP instructions in Binary Ninja before
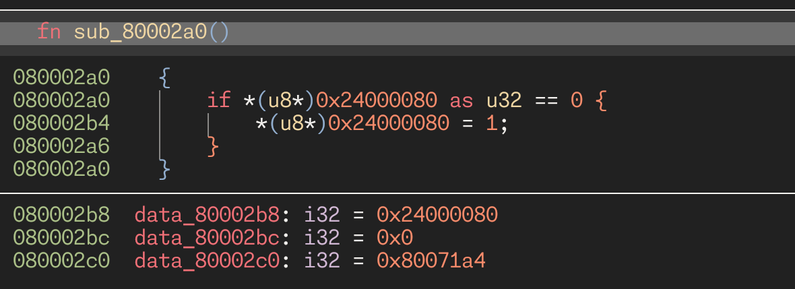
i opened one trivial function and immediately found three bugs, one of which is a show-stopper
https://github.com/Vector35/binaryninja-api/issues/6945
https://github.com/Vector35/binaryninja-api/issues/6946
https://github.com/Vector35/binaryninja-api/issues/6947
implemented a glasgow applet for sniffing conversations over UART with accurate sequencing; this will be used for finding out how the MCU talks to the GPS module
just realized that i can't exactly expect this device to work as intended right now, because it doesn't have its IMU
and it needs an IMU, alongside GPS, to know where it is
of _course_ this device pair is being annoying and switching UART speed at runtime
i didn't implement autobaud in uart-analyzer applet because i thought it 'would not be that important'. agh
adding proper autobaud is fairly tricky for the analyzer, but i did at least add per-channel baud (i.e. you can have different baud rates for RX and TX)
an online ublox protocol decoder (implemented e.g. as a script) could promptly switch baud rates when it observes a command to do so
i've reverse-engineered the entire state machine in the firmware. it only parses three messages! these are:
UBX-NAV-PVT
UBX-NAV-SOL
UBX-NAV-SAT
once again, the firmware is... simple. every part i can understand does exactly one thing, in the most uncomplicated way possible
yeah, it reads data from the GNSS module into a preallocated buffer that has space for about 32 satellites (i'm not clear on how many exactly but definitely not more than that)
the GNSS module has 72 channels
so, after close examination, i think the device currently in my hands isn't an autopilot or the like. its job is solely to grab a stream of radio frequency data from a CRPA, to do some form of processing on it, and to spit it out in form of a rapid (saturating the UART) stream of telemetry somewhere else (after combining with IMU data)
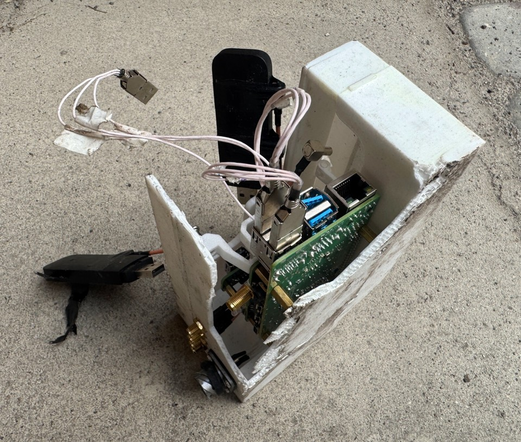
apparently there are raspberry pis involved at one stage
@whitequark @azonenberg oh wow, something about this feels *very* "familiar" and not at all like what we expected a weapon to look like
other than the chonky connectors, it feels like any other bit of standard industrial kit (esp. something about the large ugly fiducials and the pile of "QC passed" stickers)
@whitequark @azonenberg the radio/fpga board feels fairly typical of industrial/professional kit, but that gps+mcu board feels like it could've come from aliexpress
brb re-evaluating our life choices /hj
@whitequark @r interesting they sanded off the ID info from the FPGA.
Looks like Kintex-7 FFG series package at a glance?
@azonenberg @r xc7k325t by idcode, dunno what speed grade
we reverse engineered most of the bitstream too
@whitequark You might have seen this already. I think its the same part you are looking at, plus some more, and there is definitely a Pi-like board there.
https://www.ebay.com/itm/256969053946?
Edit (Pi-like, I think the color of those USB's is a bit off)
@rcombs beats me
but i also would expect the SBU to know basic shit like this already. to the best of my knowledge the devices i have are of little operational interest, Ukrainian electronic warfare is far ahead of what these devices can tolerate
Is it one a few ukrainians might be interested in being tagged into this thread, or are we assuming they are already reading it with interest?
@whitequark Yeah, it's tricky, and hard to know if it is old stuff to the people really working on this in UA.
But on the other hand if there is even a 5% chance that this could be a useful way of disabling hundreds of drones, it would be nice if they got it sooner rather than later.