CodingPanic
- 84 Followers
- 245 Following
- 40 Posts
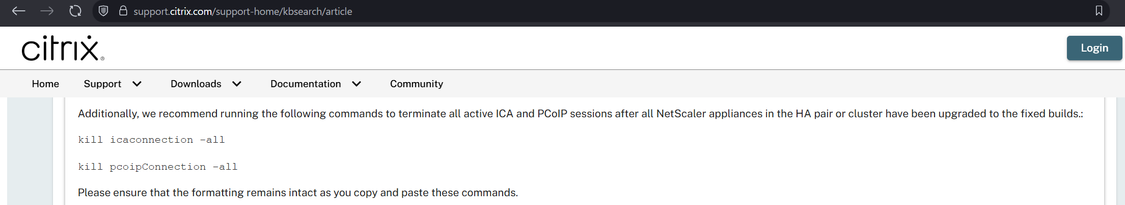
I believe Citrix may have made a mistake in the patching instructions for CitrixBleed2 aka CVE-2025-5777.
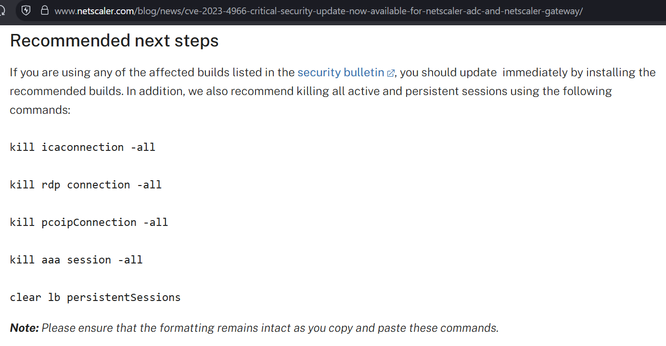
They say to do the instructions on the left, but they appear to have missed other session types (e.g. AAA) which have session cookies that can be stolen and replayed with CitrixBleed2. On the right is the CitrixBleed1 instructions.
The net impact is, if you patched but a threat actor already took system memory, they can still reuse prior sessions.
Tell anybody you know at Citrix.
A free Playdate app to sideload: xkpd, Paul Straw's xkcd reader—check out the latest comic, go to a specific one, or jump around randomly. Cool use of the new networking APIs!
https://daringfireball.net/linked/2025/06/24/sorry-macos-tahoe-b2-finder-icon
📚 A truly incredible 16-page cover feature on Big Walk is now ready for you to read! Get your copy of Edge #412…
• In Apple News+ if you have that: https://apple.news/I5yzL0QgZTMWoTXO7dOt2qw
• As a print or digital issue: https://www.magazinesdirect.com/az-magazines/6936949/edge-magazine-single-issue.thtml
• As a digital issue: https://pocketmags.com/us/edge-magazine
• On British (and EU?) newsstands now!
• At USA Barnes & Noble newsstands in a month.
Our deepest thanks to Edge, and thanks to YOU for supporting games journalism.
"…It may be time for a critical reassessment of what Panic is building here. Slowly, gradually, the Playdate has evolved into something more like a large-scale, collaborative, physical version of UFO 50. It’s an alternate history Game Boy with dozens upon dozens of genuinely great games." 👍
https://www.pushtotalk.gg/p/how-much-game-can-you-fit-in-27-inches