CodingPanic
- 83 Followers
- 244 Following
- 49 Posts
Wow! This is the most beautiful #Cyberdeck I've ever seen. 😍

DIY Dual-Screen Cyberdeck: Sleek Design, Ultimate Functionality
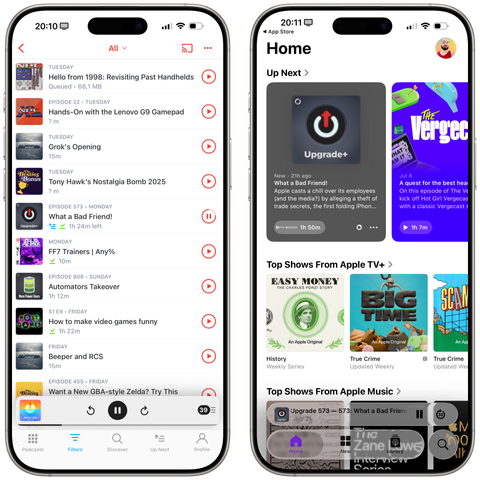
Pocket Casts for iOS 18 on the left, Apple Podcasts for iOS 26 on the right.
Between the illegible glass and the tab bar that disappears on scroll, I honestly have no idea who can take a look at this and say "Yes, that'll do it. That's good."
Liquid Glass is a mess so far, *especially* on iOS. Actually pushing me to use apps without Liquid Glass.
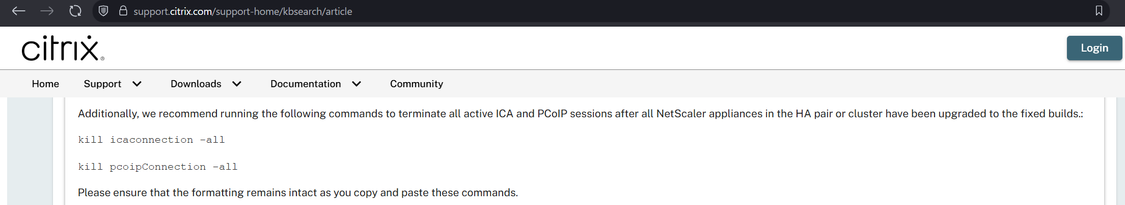
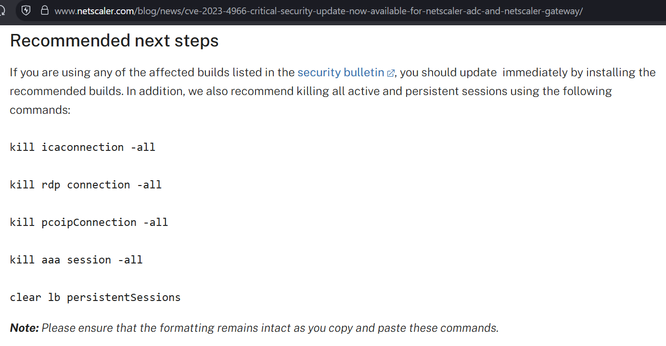
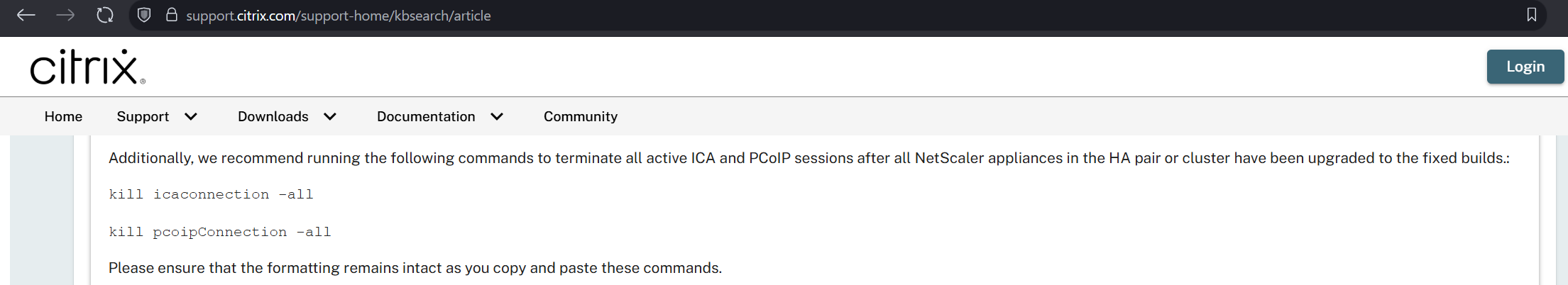
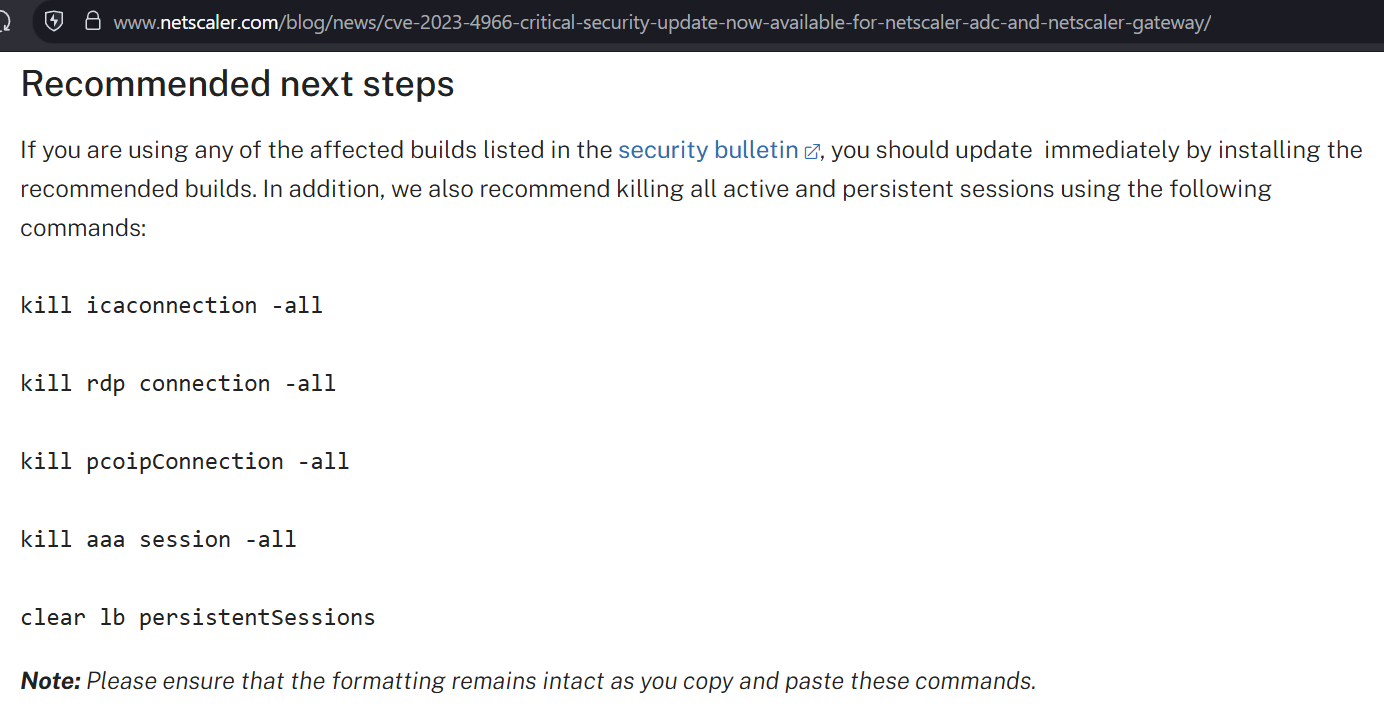
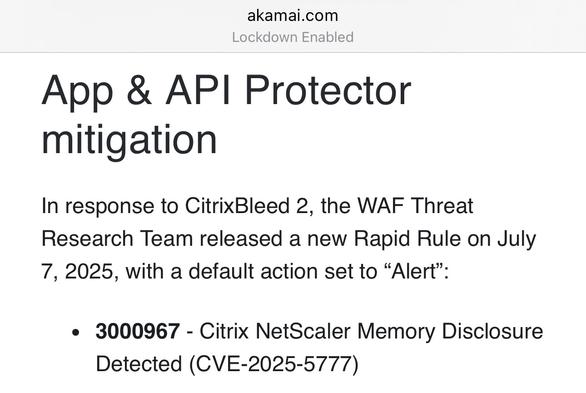
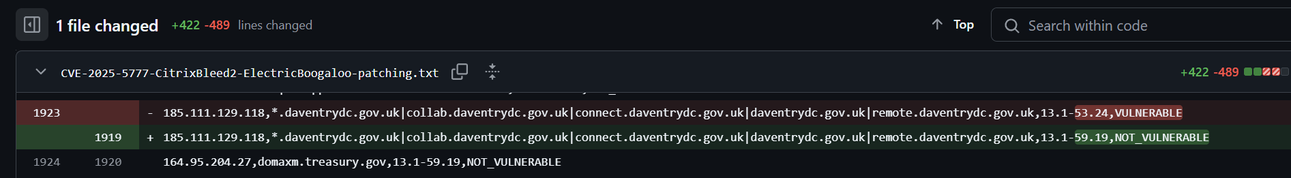
I believe Citrix may have made a mistake in the patching instructions for CitrixBleed2 aka CVE-2025-5777.
They say to do the instructions on the left, but they appear to have missed other session types (e.g. AAA) which have session cookies that can be stolen and replayed with CitrixBleed2. On the right is the CitrixBleed1 instructions.
The net impact is, if you patched but a threat actor already took system memory, they can still reuse prior sessions.
Tell anybody you know at Citrix.
A free Playdate app to sideload: xkpd, Paul Straw's xkcd reader—check out the latest comic, go to a specific one, or jump around randomly. Cool use of the new networking APIs!
https://daringfireball.net/linked/2025/06/24/sorry-macos-tahoe-b2-finder-icon










 🇺🇦
🇺🇦

 🛡️
🛡️ 