Organisers of the annual Virus Bulletin conference.
Virus Bulletin
- 2.5K Followers
- 57 Following
- 2K Posts
Organisers of the annual Virus Bulletin conference.
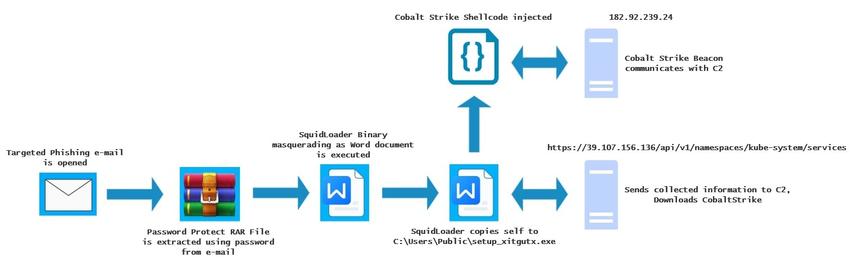
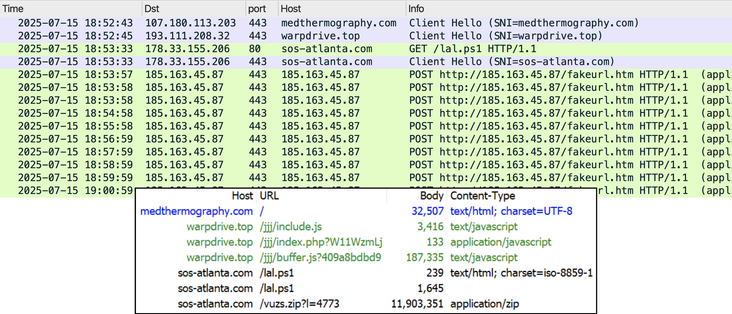
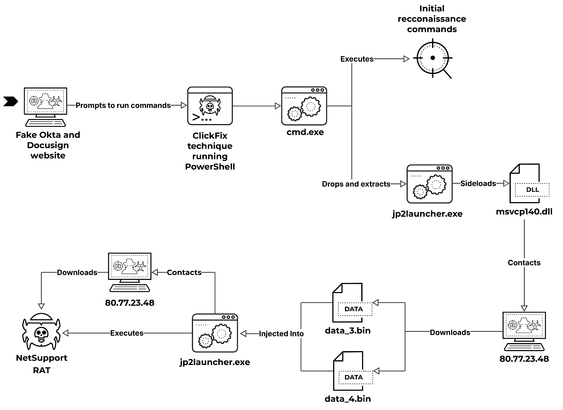
2025-07-15 (Tuesday): Tracking #SmartApeSG
The SmartApeSG script injected into page from compromised website leads to #ClickFix style fake verification page. ClickFix-ing you way through this leads to a #NetSupportRAT infection.
Compromised site (same as yesterday):
- medthermography[.]com
URLs for ClickFix style fake verification page:
- warpdrive[.]top/jjj/include.js
- warpdrive[.]top/jjj/index.php?W11WzmLj
- warpdrive[.]top/jjj/buffer.js?409a8bdbd9
Running the script for NetSupport RAT:
- sos-atlanta[.]com/lal.ps1
- sos-atlanta[.]com/lotu.zip?l=4773
#NetSupport RAT server (same as yesterday):
- 185.163.45[.]87:443
Your research deserves a global stage. The Last-Minute CFP is now open!
We’re excited to open our Call for Last-Minute Papers for hot and emerging topics! Now’s your chance to share new insights, research, or case studies with the global security community.
📅 Don’t wait, submit before 24 August
👾 #Mamba2FA #phishing kit lets attackers bypass MFA and access victims’ Microsoft 365 accounts.
Used against individuals and businesses, it is gaining popularity, with campaigns seen in Europe, North America, and parts of Asia.
🎯 See analysis: https://any.run/malware-trends/mamba/?utm_source=mastodon&utm_medium=post&utm_campaign=mamba&utm_content=tracker&utm_term=140725
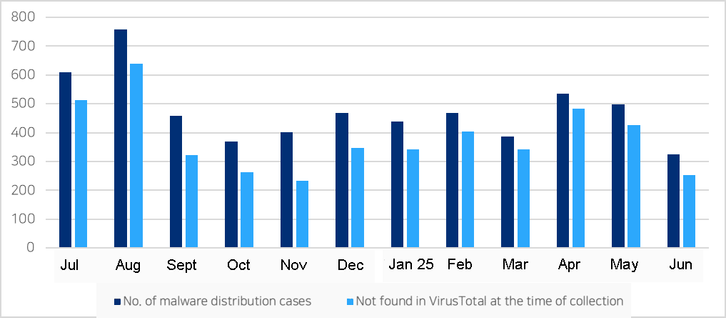
🤖 Jan-Jun 2025 Botnet Threat Update out now!
⬆️ Total of 17,258 botnet C&Cs observed, up by +26%.
⬇️ Botnet C&Cs continue to drop for 🇧🇬 Bulgaria (-40%) and 🇲🇽 Mexico (-25%)
➡️ Pentest frameworks represent 43% of Top 20 malware associated with Botnet C&Cs.
🇺🇲 Meanwhile, three US-based networks suffered significant increases for hosting the most active botnet C&Cs….
Find out which ones in the latest FREE report here👇
https://www.spamhaus.org/resource-hub/botnet-c-c/botnet-threat-update-january-to-june-2025