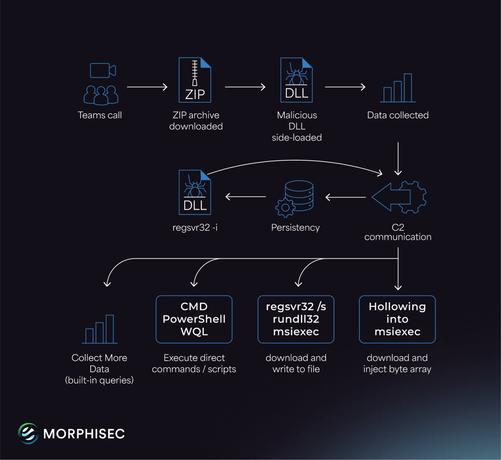
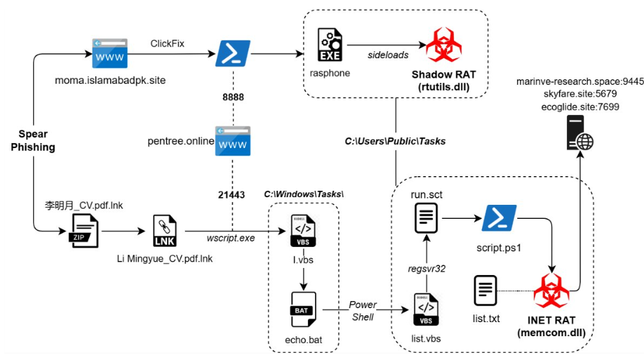
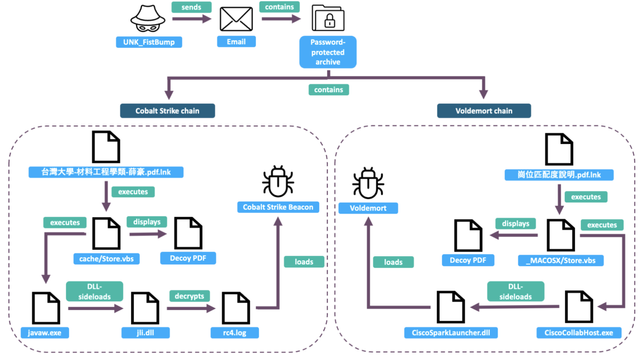
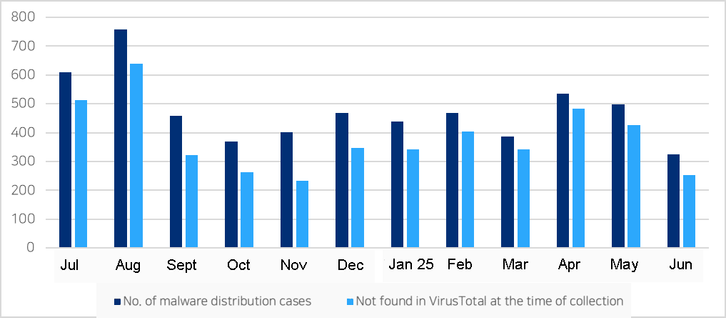
2025-07-15 (Tuesday): Tracking #SmartApeSG
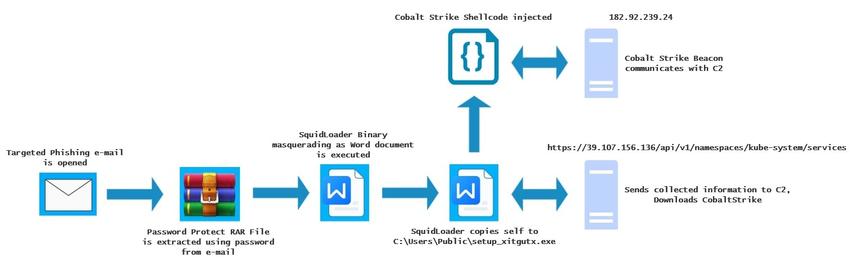
The SmartApeSG script injected into page from compromised website leads to #ClickFix style fake verification page. ClickFix-ing you way through this leads to a #NetSupportRAT infection.
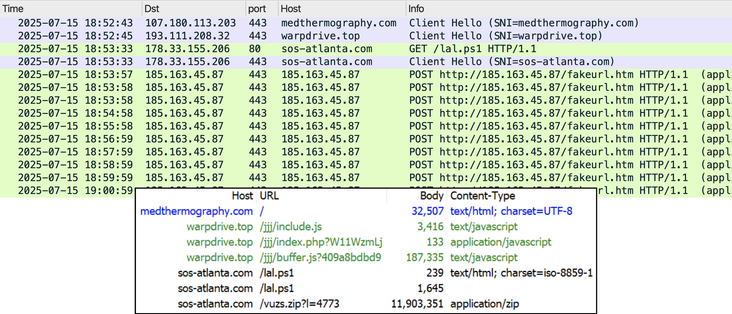
Compromised site (same as yesterday):
- medthermography[.]com
URLs for ClickFix style fake verification page:
- warpdrive[.]top/jjj/include.js
- warpdrive[.]top/jjj/index.php?W11WzmLj
- warpdrive[.]top/jjj/buffer.js?409a8bdbd9
Running the script for NetSupport RAT:
- sos-atlanta[.]com/lal.ps1
- sos-atlanta[.]com/lotu.zip?l=4773
#NetSupport RAT server (same as yesterday):
- 185.163.45[.]87:443