Phishing campaign impersonates Booking.com, delivers a suite of credential-stealing malware
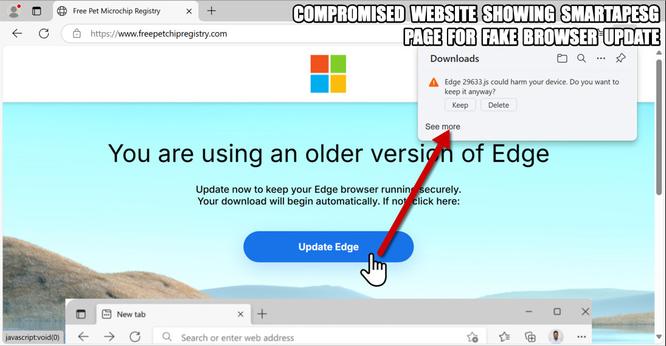
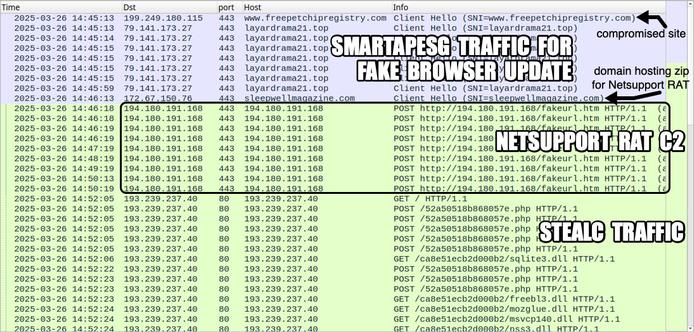
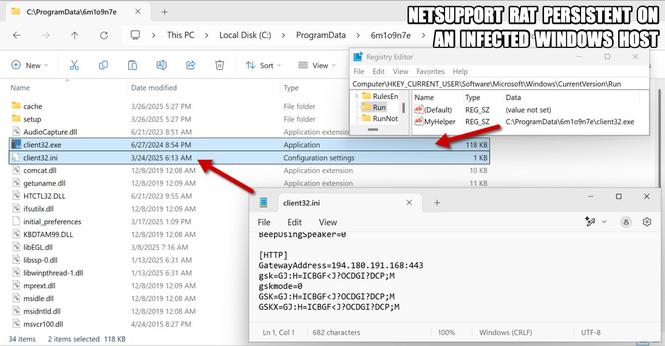
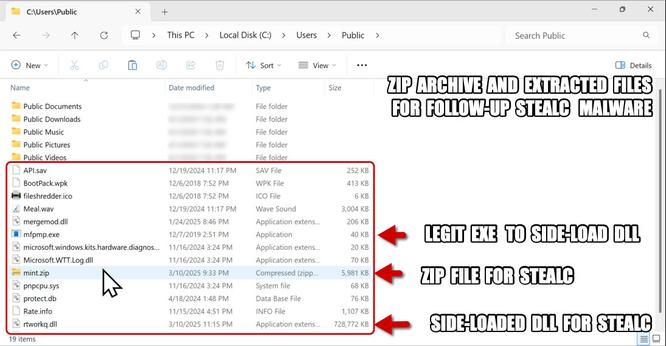
A phishing campaign targeting organizations in the hospitality industry has been identified, impersonating Booking.com and using the ClickFix social engineering technique to deliver multiple credential-stealing malware. The campaign, tracked as Storm-1865, targets individuals likely to work with Booking.com in North America, Oceania, Asia, and Europe. The attack uses fake emails and webpages to trick users into executing malicious commands, leading to the download of various malware families including XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT. The campaign aims to steal financial data and credentials for fraudulent use, showing an evolution in the threat actor's tactics to bypass conventional security measures.
Pulse ID: 67fb93e8ebc93d6ded395f39
Pulse Link: https://otx.alienvault.com/pulse/67fb93e8ebc93d6ded395f39
Pulse Author: AlienVault
Created: 2025-04-13 10:37:28
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Asia #AsyncRAT #CyberSecurity #DanaBot #Email #Europe #FinancialData #Hospital #ICS #InfoSec #LummaStealer #Malware #NetSupport #NetSupportRAT #NorthAmerica #OTX #OpenThreatExchange #Phishing #RAT #SocialEngineering #Venom #Worm #XWorm #bot #AlienVault