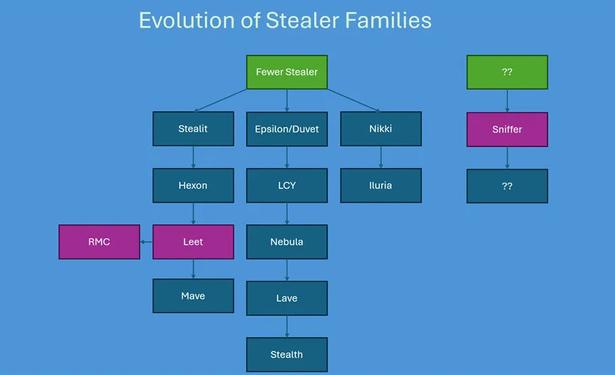
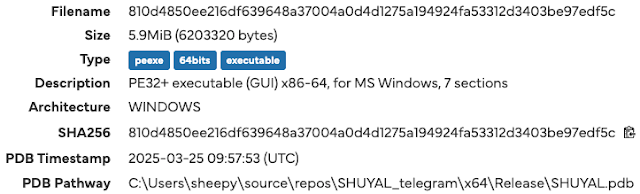
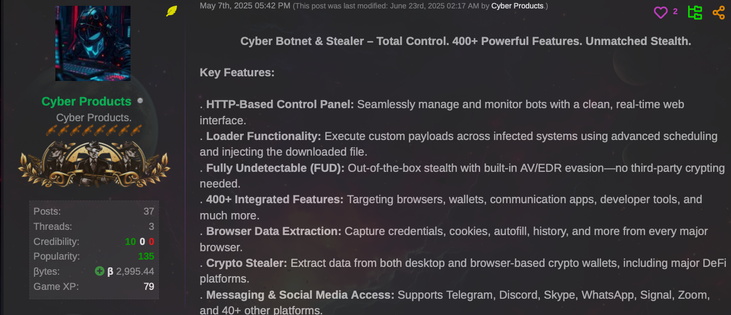
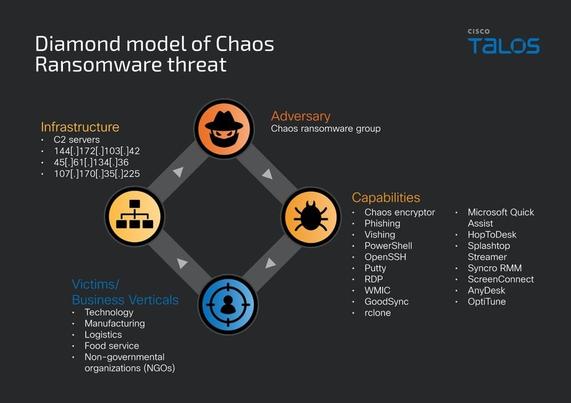
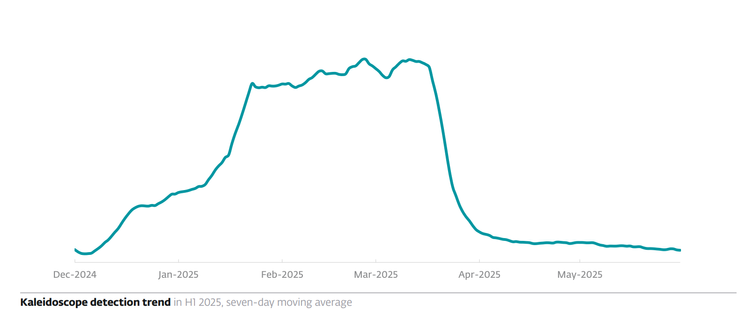
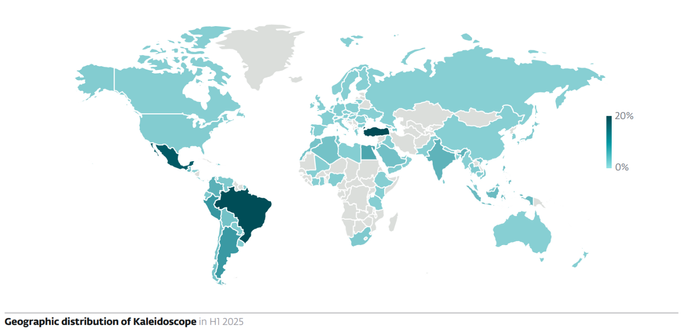
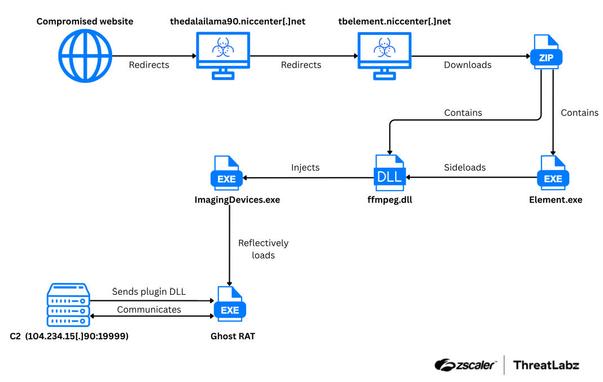
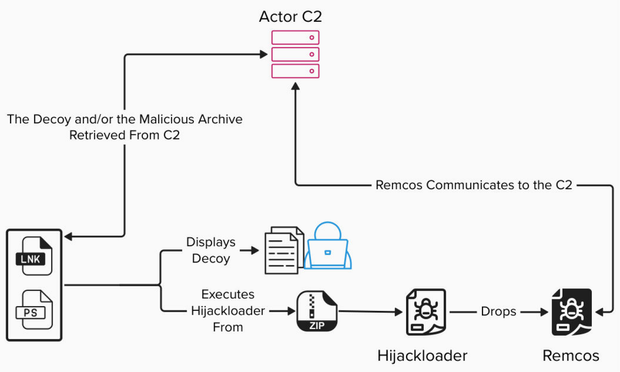
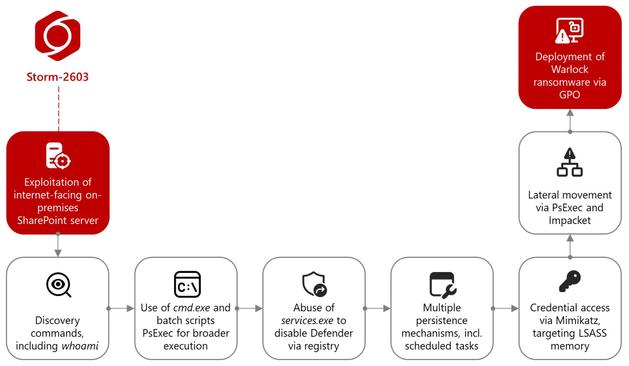
🚨 Job Seekers, watch out! 🚨 Proofpoint researchers have observed multiple email campaigns impersonating job interview invites from real companies and recruiters.
These emails claim to offer opportunities via Zoom or Teams, but instead lead recipients to install remote management tools (RMM) like SimpleHelp, ScreenConnect, or Atera.
Here's what you need to know:
💻 What’s the threat?
While RMM tools are used legitimately by IT teams, in the hands of cybercriminals, they function like remote access trojans (RATs)—granting attackers full access to your computer, data, and finances.
📬 In one case, a hacked LinkedIn account posted a real job description but swapped in a malicious Gmail address. Proofpoint later discovered this address being used to send fake interview invites to job seekers who had applied.
🔍 How are they doing it?
Threat actors may:
• Create fake job listings to harvest emails
• Hack recruiter inboxes or LinkedIn accounts
• Use lists of stolen email addresses
🎯 This trend is part of a broader wave of cyberattacks where RMM/RAS (remote access software) is used as the initial payload—blending in with normal traffic before launching further attacks like data theft or ransomware.
⚠️ If you're job hunting, stay alert:
• Double-check email sender names and domains
• Be wary of .exe files or suspicious URLs
• If something feels off, trust your instinct
Read more from our threat research team on threats using RMM tools: https://www.proofpoint.com/us/blog/threat-insight/remote-monitoring-and-management-rmm-tooling-increasingly-attackers-first-choice
#OpenToWork #JobSearch #JobScam #RMM