Are you still on #Spotify?
Spotify’s CEO Daniel Ek has raised €600M for his new startup, which is developing AI TECH FOR WAR. Ek still owns 9% of Spotify, but has 37% voting control. His net worth went from $2.5B to $10B in the last two years alone, on the back of paying musicians a pittance in royalties.
And don’t forget:
• Spotify spent $250M of your subscription dollars to invite Joe Rogan to spew his disinformation on their platform.
• They’re still trying to embrace and extinguish Podcasts.
• They’re developing in-house, AI-generated “music” so users will play them (royalty-free) instead of music created by humans (who demand royalty).
And now, he’s using his wealth, created by your subscriptions, to fund tech that will use AI to literally murder humans in war.
Stop funding him. Quit Spotify now.
#QuitSpotify #music #ai #militaryTech #techbro
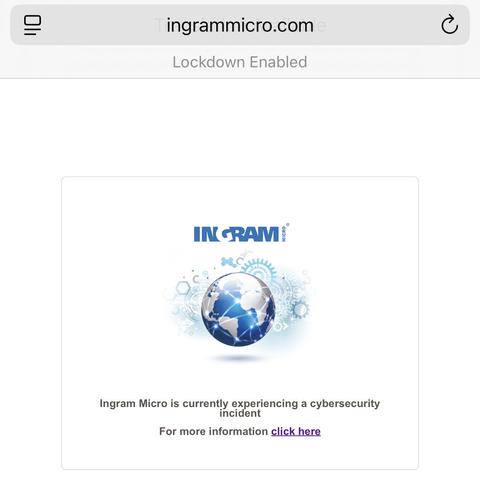
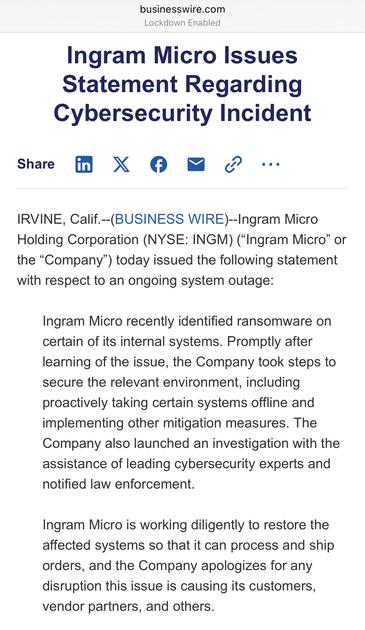
“Spotify’s CEO invests $1 billion into an AI military start-up — and musicians are fuming”
https://www.news.com.au/finance/work/leaders/spotifys-ceo-invests-1-billion-into-an-ai-military-startup-and-musicians-are-fuming/news-story/78805666e2374281801622066dc87319

















 🇺🇦
🇺🇦