If anybody wonders who Ingram Micro are, they turn over $48 billion a year and have about 20 different business units and brands.
Their network border is dead. Haven’t checked network traffic to see if ransomware yet.
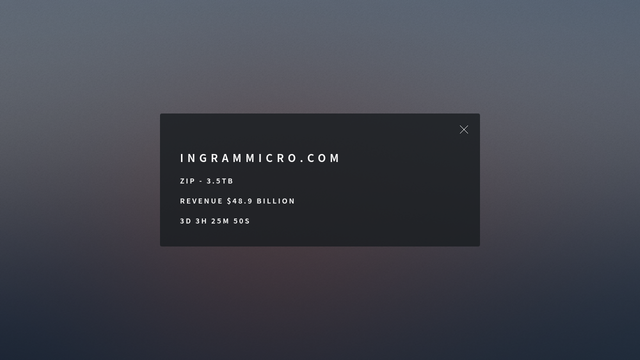
Bleeping Computer confirms: https://www.bleepingcomputer.com/news/security/ingram-micro-outage-caused-by-safepay-ransomware-attack/
2 and a bit days in and Ingram Micro still haven’t admitted what is happening, instead saying “Maintenance”
They’re both a large MSP and MSSP who sell anti-ransomware services.
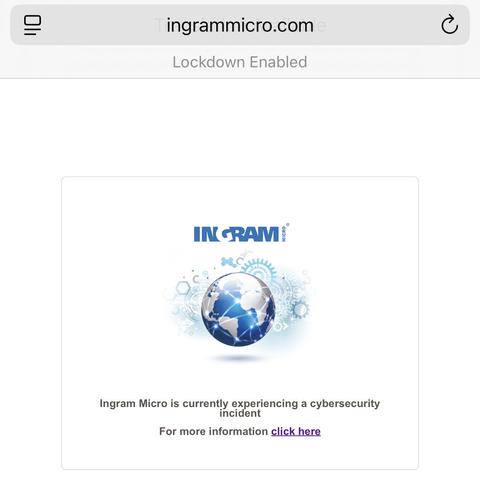
Three days in, Ingram Micro have updated their website to say they’re having a cybersecurity incident. They’ve also linked their press release, calling it ransomware. https://www.ingrammicro.com/
It’s a smart play as it makes them the owner of the narrative.
Ingram Micro have filed an 8-K for ransomware.
Some incredible wordsmithing here - rather than say when the incident began, they say when they issued a press release. Which was days later than when the incident began. I think this is because they missed SEC reporting deadlines.
https://www.sec.gov/ix?doc=/Archives/edgar/data/1897762/000162828025034372/ingm-20250705.htm
I'm sensing a profound disturbance in the irony field 🙄🤷♂️
@GossiTheDog
Item 8.01. Other Events.
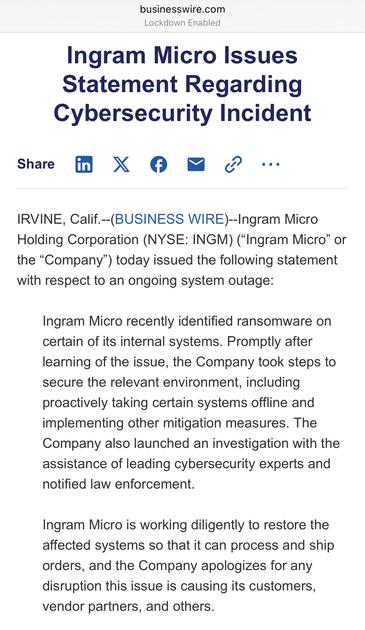
On July 5, 2025, Ingram Micro Holding Corporation (the “Company”) issued a press release stating the Company identified ransomware on certain of its internal systems. Promptly after learning of the issue, the Company took steps to secure the relevant environment, including proactively taking certain systems offline and implementing other mitigation measures. The Company also launched an investigation with the assistance of leading cybersecurity experts and notified law enforcement.
A copy of the press release is attached hereto as Exhibit 99.1, noting that the Company is working diligently to restore the affected systems so that it can process and ship orders.
#AltText #Alt4You
German translatio of 8-K
= Ad-Hoc Meldung
https://www.deltavalue.de/form-8-k-sec-filing/
“refreshing honest” would have been wighin the first two hours…
@deepthoughts10 @GossiTheDog this is a fundamental misunderstanding.
Ingram Micro is a *TIER 1*. There are only three of them; IM, TD Synnex, and AVNET. They do not do business with 'small.' I just happen to be a grandfathered customer in good standing from the 90's.
All the low tier MSPs are dealing with an entirely different arm. The minimums for a REAL customer is an insurable LoC of at least $10M last I looked.
@GossiTheDog and iirc it's not possible to eject a reseller partner (even one that isn't currently placing licences in your tenant) from your MS365 tenant, either - the reseller has to delete the relationship (or maybe, if you can figure out a way to contact them, MS can do it for you).
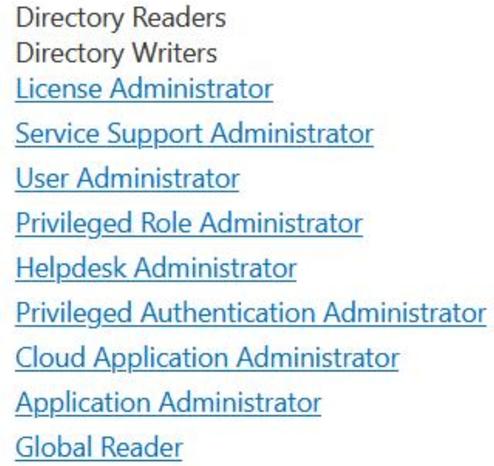
Can't reseller partners create new global admins to do tenant recovery even if they have no role assigned?
@root @GossiTheDog do want to give the nuance that their ‘regular’ tenant (ingrammicro.com) does not have access to the customer tenants. The GDAP relation is with their MSP tenant (msp.ingrammicro.com).
Not that it matters much if they have access to workstations and idp’s 🤷
@GossiTheDog One of those business units is AWS resale. Potentially there could be tens or hundreds of thousands of their customer's AWS accounts compromised as part of this - my understanding is that Ingram have full admin privileges to their resale customers accounts.
Many AWS partners use Ingram Micro to provide white label resale, so companies won't necessarily be aware they are affected because they don't deal with them directly.
- my friend just finished writing his book "how to earn big money", now we just need to get the funds to print
- he should read his book then







 🇺🇦
🇺🇦