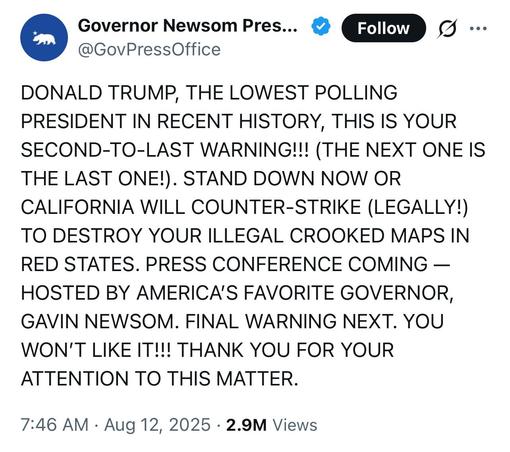
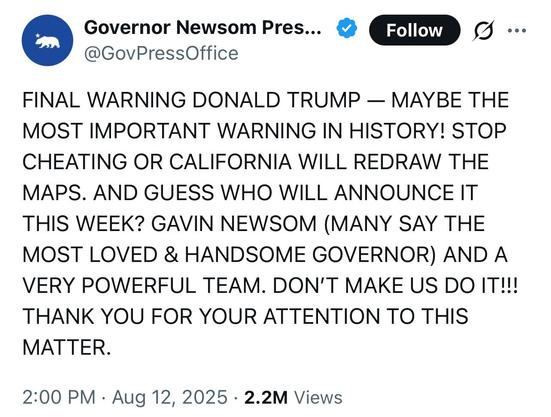
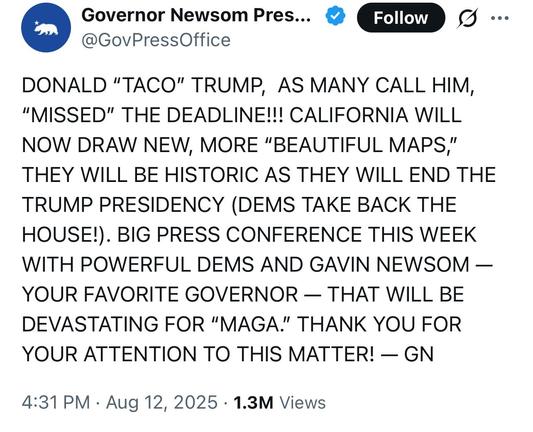
Heads up, folks:
Michael Kan reports that National Public Data is back under new owners: https://www.pcmag.com/news/site-behind-major-ssn-leak-returns-with-detailed-data-on-millions-how-to
Here is the direct link to their opt-out page instructions:
https://nationalpublicdata.com/optout.html
I had opted out previously after their humongous #databreach last year. When I checked my name now, it did not find my profile, so if you opted out before, you may still be opted out, but better safe than sorry: check and opt-out if needed.