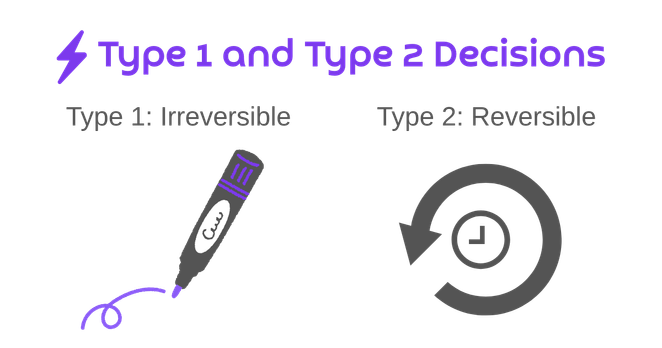
This exploited-in-the-wild issue is an interesting twist on binary planting that we were working on a decade and a half ago. The DLL/EXE search order just keeps on giving (to attackers, that is). https://binaryplanting.com
It turned out that all our security-adopted Windows versions were affected by this issue, so we created micropatches for them all. These are already distributed and applied to all online affected systems.
We would like to thank security researchers Alexandra Gofman and David Driker with @_cpresearch_ for detecting the exploitation and publishing their analysis, which made it possible for us to create a micropatch for this issue.