#Apple warns #Australia against joining #EU in mandating #iPhone app #sideloading
Operation DRAGONCLONE: Chinese Telecom Targeted by Malware
A sophisticated cyber campaign targeting China Mobile Tietong Co., Ltd., a subsidiary of China Mobile, has been uncovered. The operation, dubbed DRAGONCLONE, utilizes VELETRIX and VShell malware to infiltrate systems. The attack chain begins with a malicious ZIP file containing executable files and DLLs, exploiting DLL sideloading against Wondershare Repairit software. VELETRIX, a loader, employs anti-analysis techniques and IPFuscation to decode and execute VShell, a cross-platform OST framework. The campaign shows infrastructure overlaps with known China-nexus threat actors like UNC5174 and Earth Lamia. The attackers utilize various tools including Cobalt Strike, SuperShell, and Asset Lighthouse System for reconnaissance and post-exploitation activities.
Pulse ID: 6842f45696f96557e5f757b1
Pulse Link: https://otx.alienvault.com/pulse/6842f45696f96557e5f757b1
Pulse Author: AlienVault
Created: 2025-06-06 13:59:50
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#China #Chinese #CobaltStrike #CyberSecurity #InfoSec #Malware #OTX #OpenThreatExchange #RAT #SideLoading #Telecom #ZIP #bot #AlienVault
Apple warns Australia against following the EU in mandating iOS app sideloading, citing security risks. Australia is considering forcing Apple to open its App Store to sideloading as part of competition reforms.
https://puri.sm/posts/google-restricts-android-sideloading-what-it-means-for-user-autonomy-and-the-future-of-mobile-freedom/ #TinfoilHats #UserFreedom #HackerNews #ngated
Google Restricts Android Sideloading–What It Means for User Autonomy and Freedom
#HackerNews #Google #Sideloading #UserAutonomy #MobileFreedom #TechNews #AndroidSecurity
Installing unsigned or fake-signed iOS apps for testing without a Mac, Xcode, or access to proper signing tools can be a challenge.
Since iOS normally relies on the App Store to handle signing, getting apps onto a device manually isn’t always straightforward.
In our latest blog, we break down the main approaches to sideloading using tweaks on jailbroken devices, sideloading platforms like AltStore and Sideloadly, and on-device tools like TrollStore.
Whether your device is jailbroken or not, you’ll find a method that works.
📌Read here: https://www.pentestpartners.com/security-blog/how-to-load-unsigned-or-fake-signed-apps-on-ios/
#iOSSecurity #MobileAppTesting #Sideloading #CyberSecurity #infosec
Custom Arsenal Developed to Target Multiple Industries
Earth Lamia, an APT threat actor, has been targeting organizations in Brazil, India, and Southeast Asia since 2023. The group exploits web application vulnerabilities, particularly SQL injection, to gain access to targeted systems. They have developed custom tools like PULSEPACK backdoor and BypassBoss for privilege escalation. Earth Lamia's targets have shifted over time, initially focusing on financial services, then logistics and online retail, and recently IT companies, universities, and government organizations. The group employs various techniques including DLL sideloading, use of legitimate binaries, and development of modular backdoors. Earth Lamia's activities have been linked to other reported campaigns, suggesting a complex and evolving threat landscape.
Pulse ID: 68359559953d95d9c98f6268
Pulse Link: https://otx.alienvault.com/pulse/68359559953d95d9c98f6268
Pulse Author: AlienVault
Created: 2025-05-27 10:35:05
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Asia #BackDoor #Brazil #CyberSecurity #Government #ICS #India #InfoSec #OTX #OpenThreatExchange #SQL #SideLoading #bot #AlienVault
Infostealery rozprzestrzeniają się przez TikTok i technikę ClickFix – szczegóły techniczne kampanii
W ostatnich tygodniach badacze bezpieczeństwa zaobserwowali nietypową, skuteczną kampanię malware, w której cyberprzestępcy wykorzystują popularność TikToka do dystrybucji złośliwego oprogramowania typu infostealer (m.in. Vidar, StealC, Latrodectus). Atak opiera się na tzw. technice ClickFix, polegającej na nakłanianiu użytkowników do samodzielnego uruchamiania złośliwych poleceń PowerShell. Poniżej przedstawiamy szczegółową analizę tej kampanii oraz...
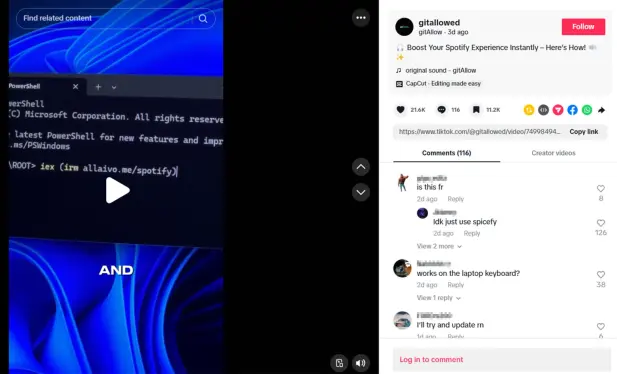
Infostealery rozprzestrzeniają się przez TikTok i technikę ClickFix – szczegóły techniczne kampanii
W ostatnich tygodniach badacze bezpieczeństwa zaobserwowali nietypową, skuteczną kampanię malware, w której cyberprzestępcy wykorzystują popularność TikToka do dystrybucji złośliwego oprogramowania typu infostealer (m.in. Vidar, StealC, Latrodectus). Atak opiera się na tzw. technice ClickFix, polegającej na nakłanianiu użytkowników do samodzielnego uruchamiania złośliwych poleceń PowerShell. Poniżej przedstawiamy szczegółową analizę tej kampanii oraz...
What the fuck? The conclusion of using the shitty #sideloading process on #ios is, that Apple is right to fight against sideloading?! Dude, sideloading is so shitty _because_ Apple is fighting it and making it as inconvenient as possible. Sideloading could be super convenient if Apple wanted to. 🤦♂️
Join us on Rootpk and let's keep it fully featured.
#sideloading #Android #EU #DMA #DigitalMarketsAct #Rootpk







