Microsoft blocca Vanilla Tempest: Falsi installer di Teams diffondevano ransomware Rhysida
All’inizio di ottobre 2025, #microsoft ha interrotto un’ampia operazione malevola attribuita al gruppo #vanillatempest revocando più di 200 certificati digitali utilizzati per firmare in modo fraudolento file di installazione di #microsoftteams
Questi pacchetti falsi servivano come vettore per diffondere la backdoor Oyster e, successivamente, i #ransomware Rhysida.
A small number of samples can poison LLMs of any size:
https://www.anthropic.com/research/small-samples-poison
"In a joint study with the UK AI Security Institute and the Alan Turing Institute, we found that as few as 250 malicious documents can produce a "#backdoor" vulnerability in a large language model—regardless of model size or training data volume."
Size does not matter: the #LLM edition. 😜
@ycombinator this is the #ss7 security leak that has been presented in a #ccc talk i think in the year 2014.
What was the app called, that could identify such SS7 network interceptions?
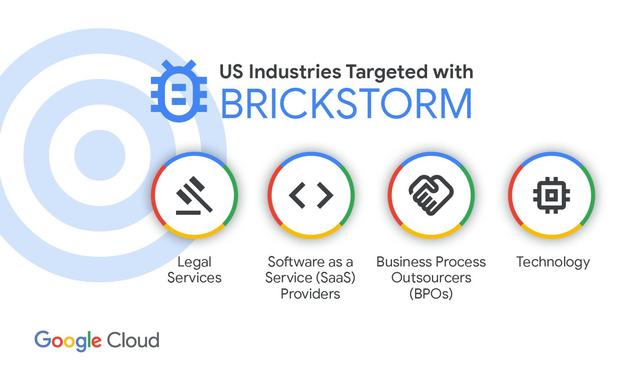
Brickstorm – backdoor po cichu wykradający dane z systemów amerykańskich organizacji
Brickstorm to backdoor napisany w Go. Pierwsze wzmianki o nim pojawiły się w kwietniu 2024 roku. Malware pełnił funkcję serwera WWW, narzędzia do manipulacji plikami, droppera, przekaźnika SOCKS oraz narzędzia do wykonywania poleceń powłoki. Badacze przypisali te ataki klastrowi aktywności grupy UNC5221, znanej z wykorzystywania podatności typu zero-day w produktach...
Brickstorm - backdoor po cichu wykradający dane z systemów amerykańskich organizacji
Brickstorm to backdoor napisany w Go. Pierwsze wzmianki o nim pojawiły się w kwietniu 2024 roku. Malware pełnił funkcję serwera WWW, narzędzia do manipulacji plikami, droppera, przekaźnika SOCKS oraz narzędzia do wykonywania poleceń powłoki. Badacze przypisali te ataki klastrowi aktywności grupy UNC5221, znanej z wykorzystywania podatności typu zero-day w produktach...
A small number of samples can poison #LLM s of any size \ Anthropic
https://www.anthropic.com/research/small-samples-poison
"... with the UK #AI #Security Institute and the Alan Turing Institute, we found that as few as 250 malicious documents can produce a "#backdoor" vulnerability in a large language model—regardless of model size or training data volume. ... 13B parameter model is trained on over 20 times more training data than a 600M model, both can be backdoored by the same small number of poisoned documents"
@Natanox @wonka @frameworkcomputer @scammo just like #ClownFlare for hosting #KiwiFarms or #Cisco who integrated the #DUAL_EC_DRBG #backdoor ...
- Tho they too haven't apologized and my tradition is that any corporation gets 3x the time barred from #procurement that it takes them to apologize and #UndoHarmCaused...
Kevin Karhan :verified: (@kkarhan@infosec.space)
@scammo@chaos.social yeah, I've mothballed any plans to order, distribute, configure or otherwise aid in the use and distribution of @frameworkcomputer@fosstodon.org . - I feel embarrassed that there was a time I honestly thought they were the good guys and even applied for a position at them. There's no legitimate reason to work with unhinged hatemongers like #DHH and #Framework has to make a choice if they want to *"die on this hill"* as a company, cuz not even #ClownFlare did so when clients canceled their garbage for hosting #KiwiFarms... - Not that #CloudFlare as a #RogueISP ever had a legitimate reason to exist - at best they are #ValueRemoving #Rentseekers but most likely they are just bad. But yeah, I'm glad my clients were understanding and agreeing with me that they don't want a `framework` when framework supports people who decline their human right to exist!
https://github.com/chili-chips-ba/wireguard-fpga #irony #privacy #backdoor #HackerNews #ngated
GitHub - chili-chips-ba/wireguard-fpga: Full-throttle, wire-speed hardware implementation of Wireguard VPN, using low-cost Artix7 FPGA with opensource toolchain. If you seek security and privacy, nothing is private in our codebase. Our door is wide open for backdoor scrutiny, be it related to RTL, embedded, build, bitstream or any other aspect of design and delivery package. Bujrum!
Full-throttle, wire-speed hardware implementation of Wireguard VPN, using low-cost Artix7 FPGA with opensource toolchain. If you seek security and privacy, nothing is private in our codebase. Our d...
#AI models can acquire #backdoors from surprisingly few malicious documents
Scraping the open web for AI #training data can have its drawbacks …researchers from #Anthropic , the #UK AI #Security Institute, & the Alan Turing Institute released a preprint research paper suggesting that large language models like the ones that power #ChatGPT , #Gemini , & #Claude can develop #backdoor #vulnerabilities from as few as 250 corrupted docs inserted into their training data
#llm
ChaosBot Abuses CiscoVPN & AD Credentials to Execute Remote Commands
ChaosBot is a sophisticated Rust based backdoor targeting enterprise networks.
Pulse ID: 68e9c8897dcf9471d86c73d1
Pulse Link: https://otx.alienvault.com/pulse/68e9c8897dcf9471d86c73d1
Pulse Author: cryptocti
Created: 2025-10-11 03:01:29
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#BackDoor #Cisco #CyberSecurity #InfoSec #OTX #OpenThreatExchange #Rust #VPN #bot #cryptocti