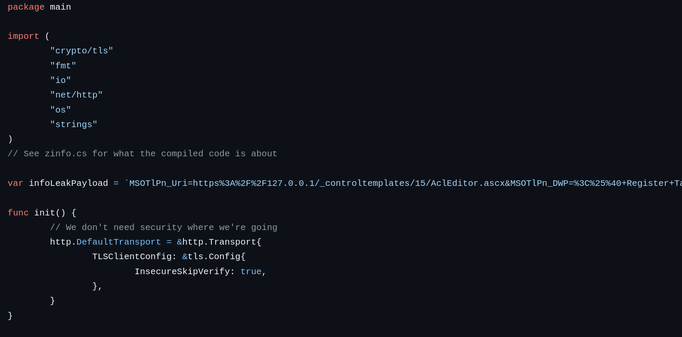
Emerging situation to be aware of - some of the #CitrixBleed2 session hijacking victims are also victims of webshell implants via a different vuln, CVE-2025-6543.
Script to check for Netscaler implants: https://github.com/NCSC-NL/citrix-2025/blob/main/TLPCLEAR_check_script_cve-2025-6543-v1.6.sh