In response to popular demand, we've added some offensive security channel to the MalwareTech Discord. Interested in pentesting, red teaming, or implant development? Check out channels
#offensive-security,
#vulnerability-research, and
#implant-development.
https://discord.gg/MalwareTech
Join the MalwareTech Discord Server!
A community for cybersecurity enthusiasts interested in learning about reverse engineering & malware. | 1528 members
The wonderful world of technology: I can't read my (physical) mail, because Cloudflare is down and the mailroom uses electronic access control.
Added a new Wiki entry: Locating Modules Via The PEB (Process Environment Block)
Should help anyone stuck on the shellcode3 reversing engineering lab.
https://malwaretech.com/wiki/locating-modules-via-the-peb-x64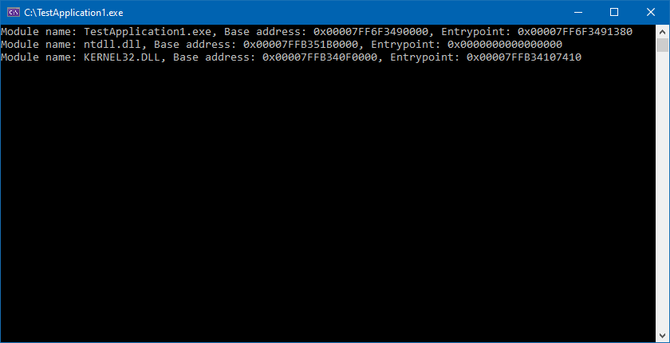
Locating Modules Via The PEB (Process Environment Block)
The PEB_LDR_DATA_TABLE is a table of information on loaded modules, which is pointed to by the PEB (process environment block). This table is often used by malicious code to find information without having to make any API calls, reducing the chance of detection and enabling position-independence.
Just released a new malware analysis lab! Shellcode3 tests your ability to analyze malicious shellcode and leverages a common technique used by malware to obscure API calls.
https://malwaretech.com/labs/shellcode/shellcode3
Shellcode 3
In this shellcode you'll find a common technique used by both shellcode and malware to obscure API calls. See if you can figure out what it's doing.
As much as I don’t like Generative AI, it’d be beneficial for schools to teach students how to properly navigate it, rather than banning it. People are going to use AI regardless. Everyone needs to understand the limitations, or risk sacrificing critical thinking to something that can’t even think.
#1 on my bucket list is to see a volcano erupt in person. I was in Hawaii during the May 25th Kilauea eruption, which I slept through. Now that I've left it's erupting again >_<
https://www.youtube.com/watch?v=BqmpkUdMtyA

[V3cam] Kīlauea volcano, Hawaii (south Halemaʻumaʻu crater)
Microsoft really doesn't like RC4 encryption apparently 😆
In the process of re-working and re-launching my beginner reverse engineering labs. You can test them out here: https://malwaretech.com/labs
More coming soon!

MalwareTech Labs - Learn Reverse Engineering & Malware Analysis – MalwareTech
As much as I love the job security, someone is going to have to stop these AI bros before they have us watering the crops with Brawndo.
After 7 years of external circumstances getting in the way, I finally managed to sit down with
@jackrhysider and record a Darknet Diaries episode. Check it out here! :D
https://darknetdiaries.com/episode/158/
MalwareTech – Darknet Diaries
MalwareTech was an anonymous security researcher, until he accidentally stopped WannaCry, one of the largest ransomware attacks in history. That single act of heroism shattered his anonymity and pulled him into a world he never expected.


