Exposing the Unseen: Mapping MCP Servers Across the Internet
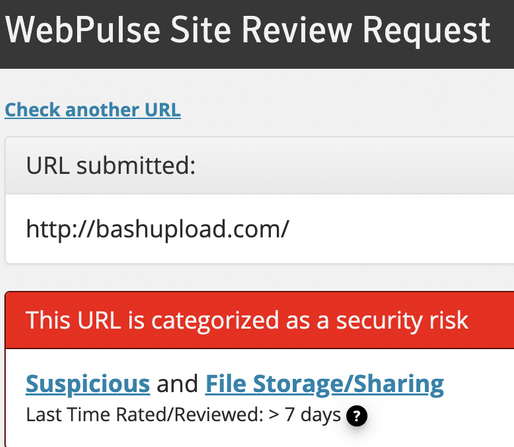
"We identified a total of 1,862 MCP servers exposed to the internet. From this set, we manually verified a sample of 119. All 119 servers granted access to internal tool listings without authentication."
this is why I keep a very watchful eye on Knostic about AI stuff, they know the tech, the risks, *and* how human behavior will interact with them.