| Website | https://marcushutchins.com |
| Security Blog | https://malwaretech.com |
Marcus Hutchins 
- 78.6K Followers
- 92 Following
- 973 Posts
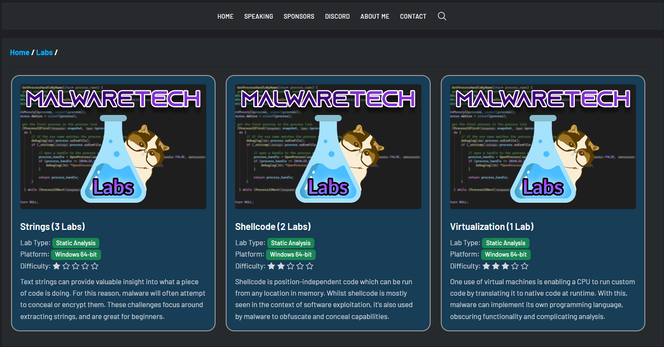
In the process of re-working and re-launching my beginner reverse engineering labs. You can test them out here: https://malwaretech.com/labs
More coming soon!
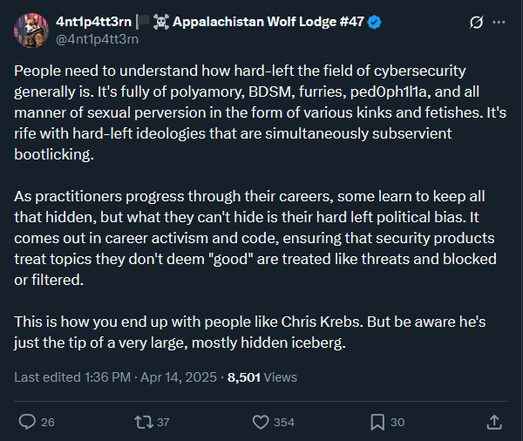
This is the kind of high quality cybersecurity content you only get on X dot com. "People support the cybersecurity guy who said the election wasn't rigged because cybersecurity is full of leftists & sexual perversion"
(Note: Chris Krebs is a lifelong Republican & Trump nominee, not even remotely left-wing).
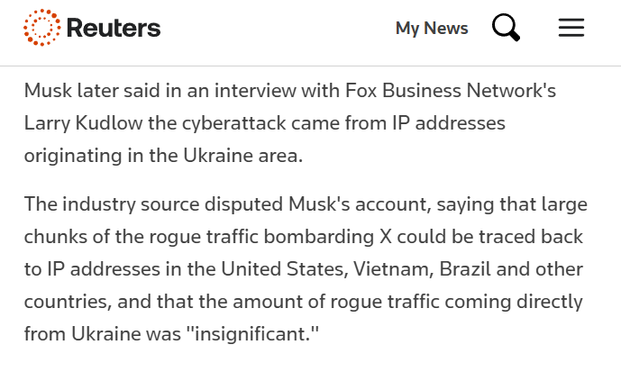
DDoS attacks almost always originate from hacked devices. The country/countries that the traffic originates from has never been an indicator of who's behind the attack. Musk's implication that Ukraine was responsible for the Twitter DDoS attack based on seeing some traffic originating from Ukrainian IPs is just dangerous speculation.
I've mapped botnet professionally for a decade, and all that looking at IP addresses locations tells you is the geographical distribution of compromised devices. When you plot this kind of data of chart, you typically just get a heat map of population density, slightly skewed by economic factors. Nations with larger populations tend to have more devices, but developing nations tend to have a higher percentage of older less secure devices, which are more likely to be hacked and recruited into botnets.
Interesting statement filed in the case against the Treasury and DOGE which gives us some cybersecurity insights. Here's the key takeaways:
- Only a single DOGE employee (25 year old engineer Marko Elez) has direct access to the Treasury payment systems.
- The DOGE employee was only allowed to access the systems from an encrypted government issued laptop.
- The government issued laptop is equipped with monitoring software, data loss prevention, and tools to block internet access, and use of removable storage devices.
- Strict instructions were given that no data could leave this laptop for the duration of the engagement.
- The employee was meant to only have read access to treasury systems, but was accidentally granted write access.
- Following the accident, the employee's laptop was examined and it was concluded that no data had been written during the mistake.
- After the employee temporarily resigned over racist Twitter posts, all access was revoked, and all government issued equipment was recovered.
- The DOGE employee shared updates about his work with another DOGE employee, which "may have occasionally included screenshots of payment systems data or records"
My take:
If true, it seems that unlike other instances at different agencies, the Treasury abided by strict security protocols.
My only real cybersecurity question here are:
1) They document claims screenshots of payment records were shared with another DOGE employee. It doesn't specify how they were shared. Was it just the authorized employee showing his screen to someone, or were they transmitted outside of the laptop? If it's the latter, then it calls much of the claims made in the article into question.
2) This statement isn't clear "The Bureau enabled enhanced monitoring on his laptop, which included the ability to monitor and block website access, block the use of external peripherals (such as USB drives or mass storage devices), monitor any scripts or commands executed on the device, and block access to cloud-based storage services."
The use of the phrase "included the ability to" isn't really clear on if those security controls were actually being enforced. The phrasing could simply mean they enabled software that had those capabilities, but they weren't being used.
Now, cybersecurity aside, the bigger question is what was the purpose of any of this? To audit something as complex as a treasury payment systems, you'd need teams of forensic accountants.
A single 25 year old software engineer with no prior treasury experience poking around some files on a laptop is not an audit. The entire DOGE operation seems like a charade. The organization consists almost entirely of young engineers pulled from Musk's other companies, has produced no plan for how they intend to audit any of these systems, and lacks any oversight at all.
Lol, Florian is big mad because I called him out for defending a Nazi salute and spreading AfD (German Neo-Nazi party) propaganda.
It's true though, I do dislike him for other reason. I've disliked him ever since 2020 when I had to unfollow him for posting MAGA nonsense. I then disliked him even more when he decided not to respect my decision to leave Twitter and kept reposting my posts there without my permission while simultaneously mocking my choice to leave, and now that he's gone full blown mask-off neo-Nazi, I dislike him close to the maximum amount I can dislike a person.