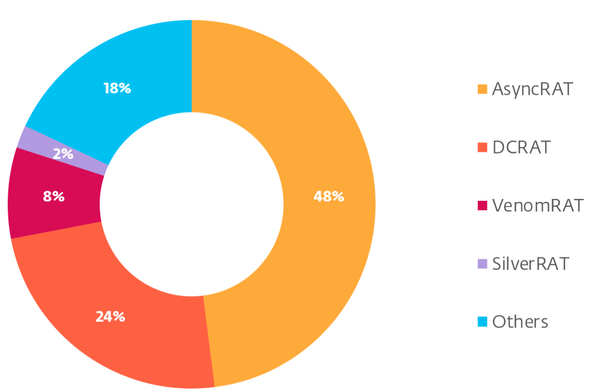
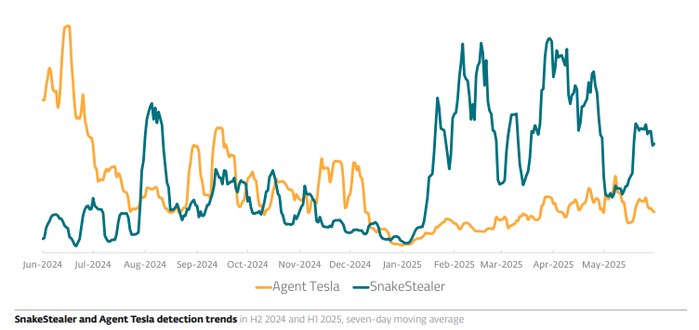
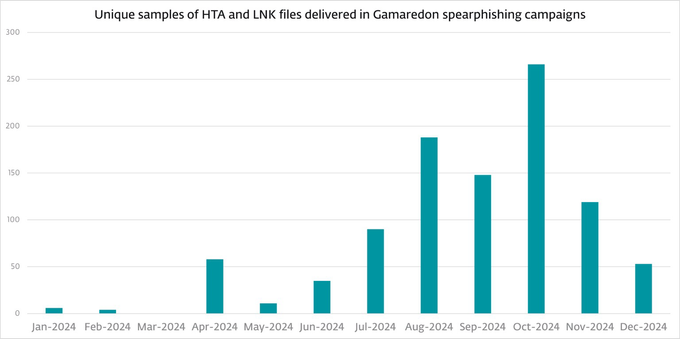
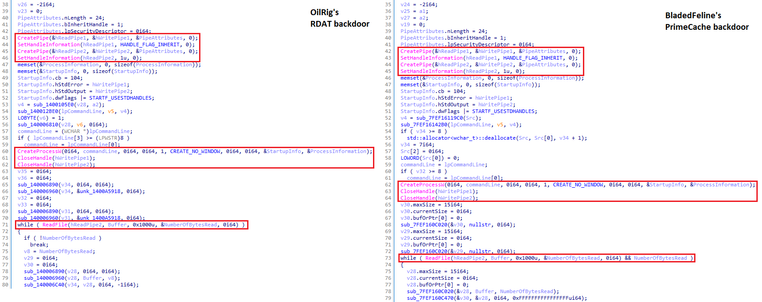
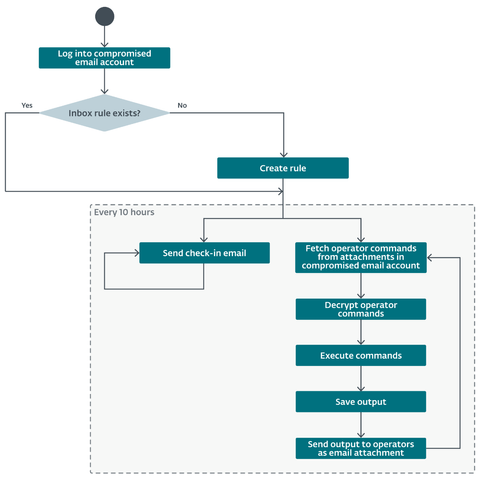
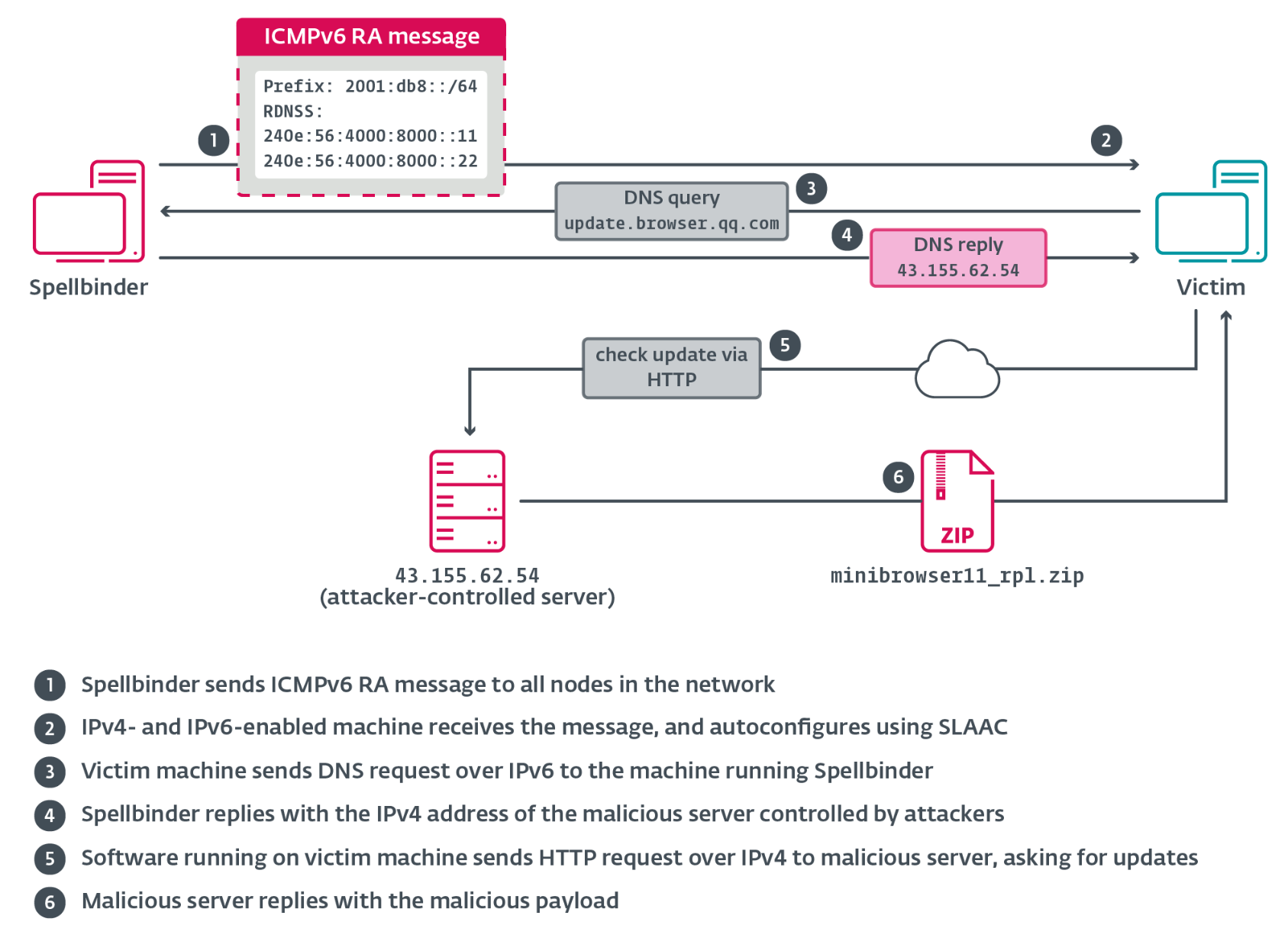
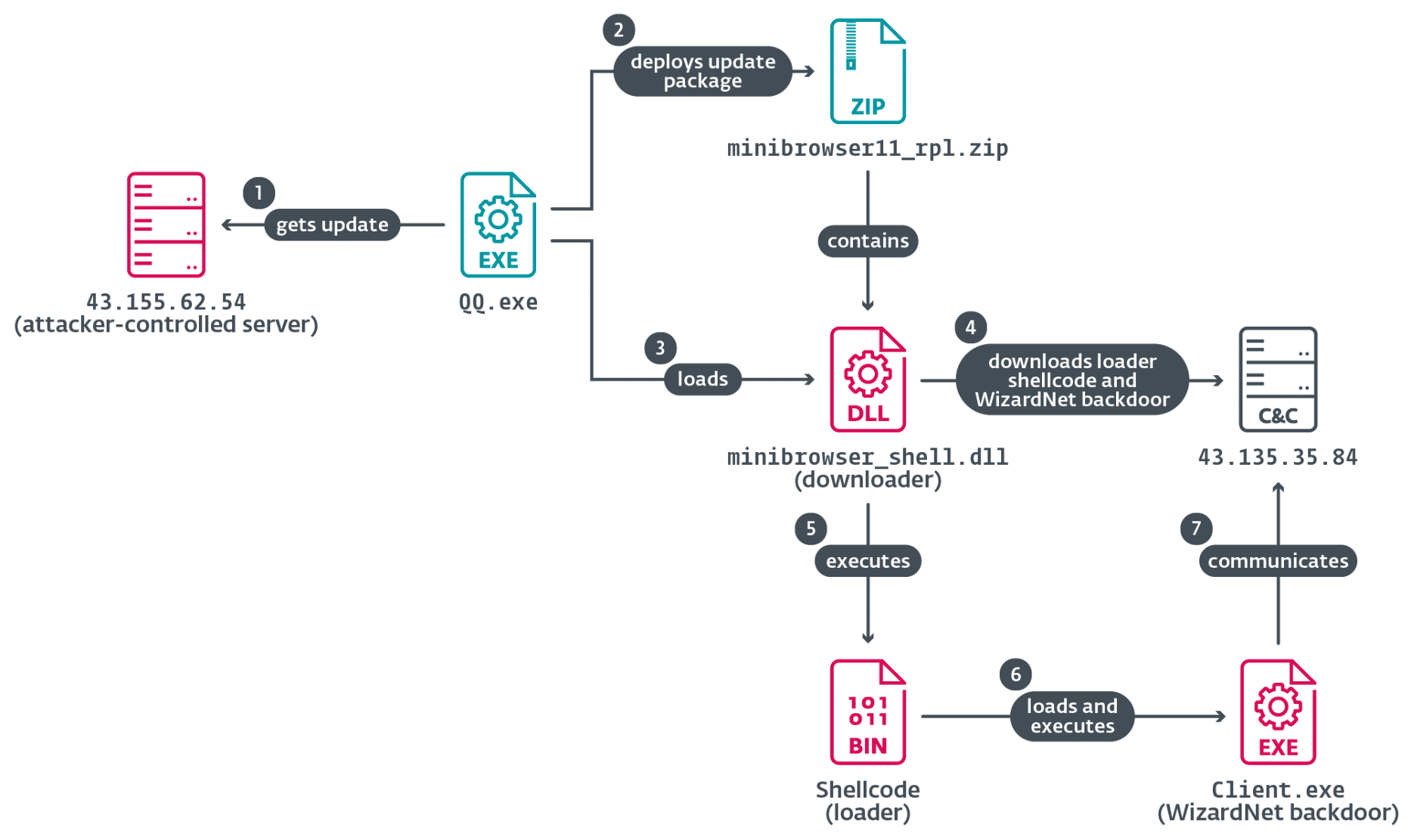
#ClickFix went from virtually non-existent to the second most common attack vector blocked by #ESET, surpassed only by #phishing. This novel social engineering technique accounted for nearly 8% of all detections in H1 2025. #ESETresearch
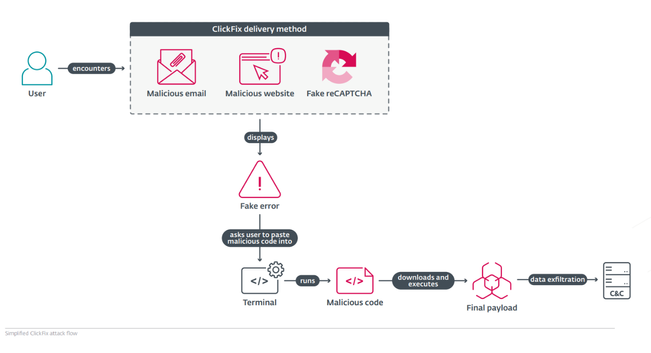
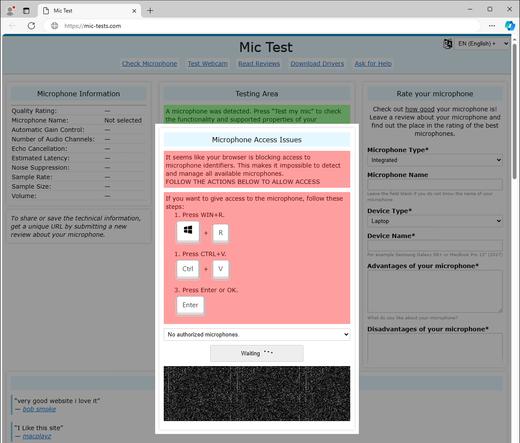
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
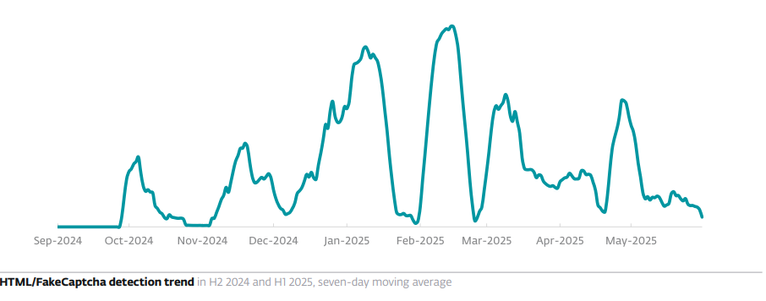
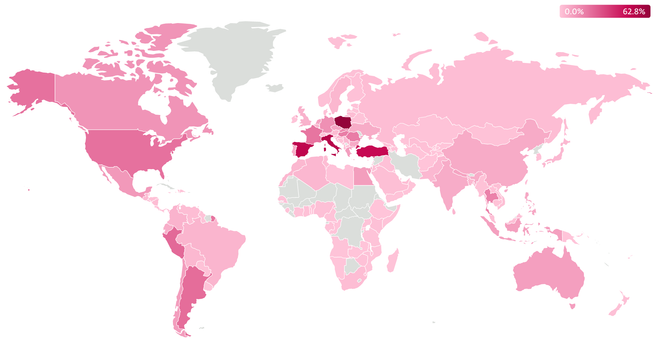
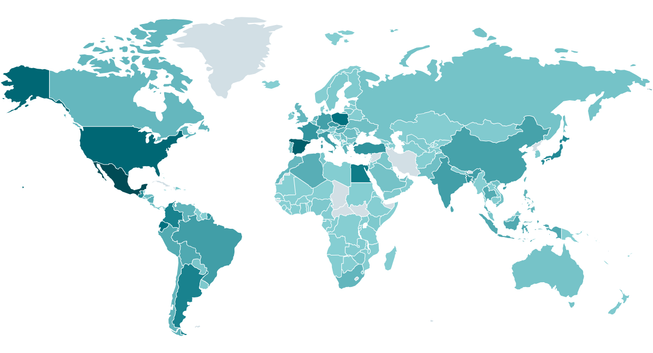
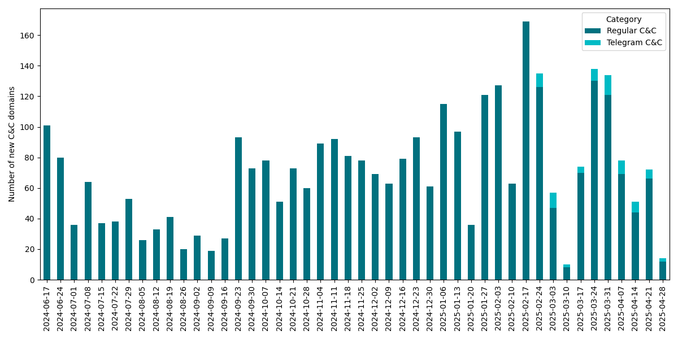
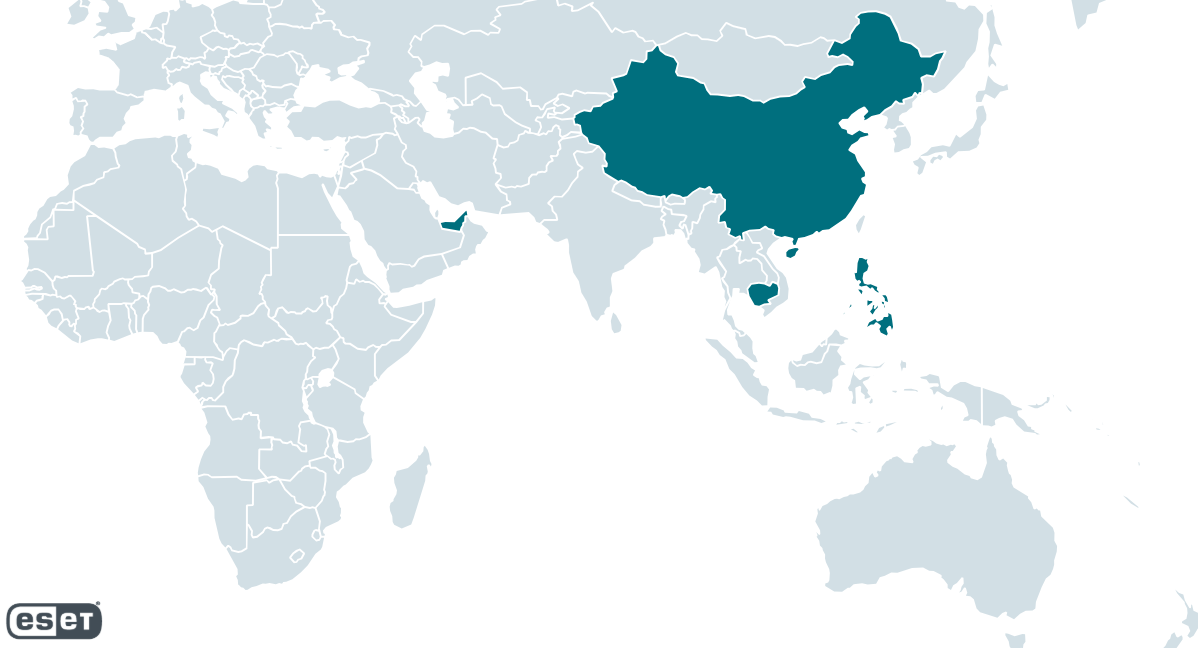
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
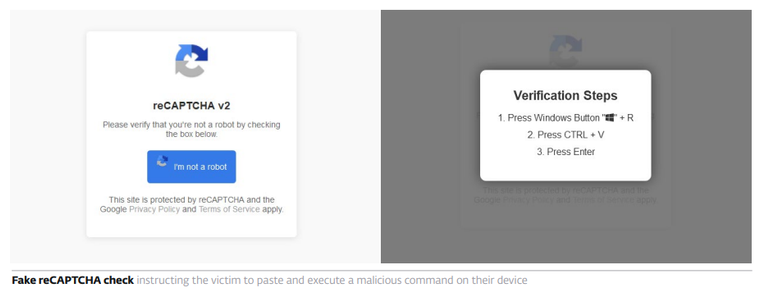
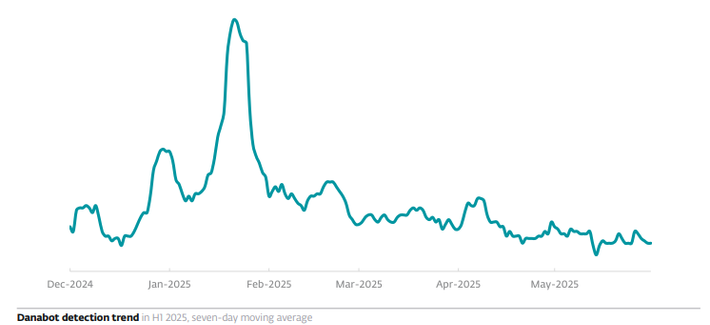
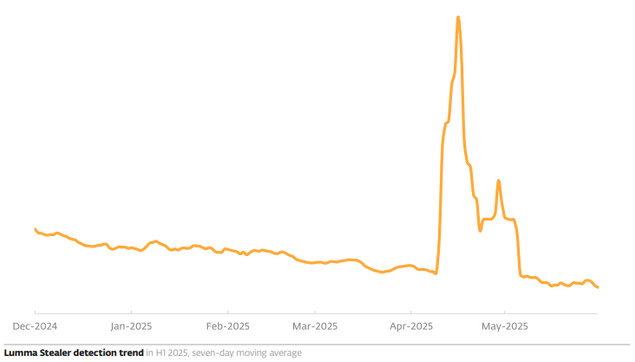
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
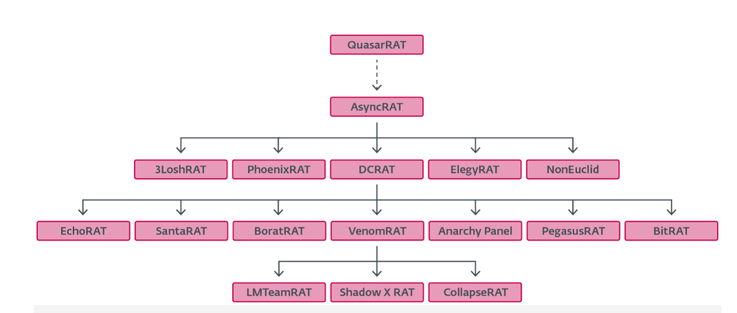
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport:
🔗 https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025
ClickFix lures users by displaying bogus error messages followed by quick fix instructions, including copy-pasting malicious code. Running the code in the victim’s command line interpreter delivers malware such as #RATs, infostealers, and cryptominers.
Between H2 2024 and H1 2025, ESET’s detection for ClickFix, HTML/FakeCaptcha, skyrocketed by 517%. Most detections in ESET telemetry were reported from Japan (23%), Peru (6%), and Poland, Spain, and Slovakia (>5% each).
What makes #ClickFix so effective? The fake error message looks convincing; instructions are simple, yet the copied command is too technical for most users to understand. Pasting it into cmd leads to compromise with final payloads, including #DarkGate or #LummaStealer.
While #ClickFix was introduced by cybercriminals, it’s since been adopted by APT groups: Kimsuky, Lazarus; Callisto, Sednit; MuddyWater; APT36. NK-aligned actors used it to target developers, steal crypto and passwords from Metamask and #macOS Keychain.
#ClickFix uses psychological manipulation by presenting fake issues and offering quick solutions, which makes it dangerously efficient. It appears in many forms – error popups, email attachments, fake reCAPTCHAs – highlighting the need for greater vigilance online.
Read more in the #ESETThreatReport:
🔗 https://welivesecurity.com/en/eset-research/eset-threat-report-h1-2025