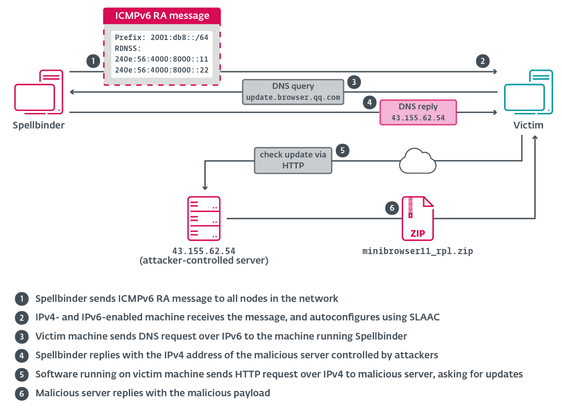
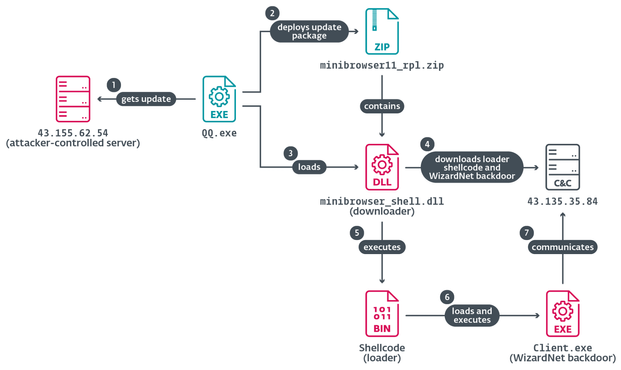
BladedFeline, a cyberespionage group active since at least 2017, develops malware for strategic access within the Kurdistan Regional Government and the government of Iraq. We discovered BladedFeline in 2023 after it targeted Kurdish officials with the #Shahmaran backdoor.
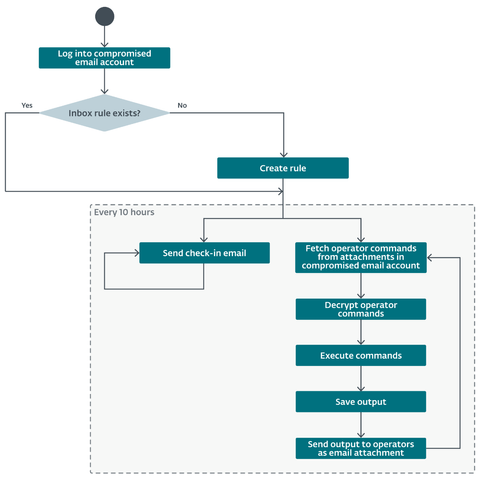
The systems compromised in the latest campaign contained the #Whisper backdoor, a malicious IIS module #PrimeCache, two reverse tunnels, and several supplementary tools. Whisper uses #MicrosoftExchange server to communicate with the attackers via email attachments.
We believe with medium confidence that BladedFeline is a subgroup of OilRig, an 🇮🇷-based APT group also known as APT34 or Hazel Sandstorm.
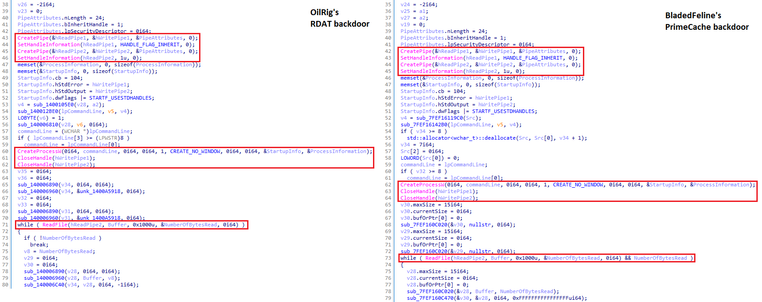
First, there were OilRig tools present in the systems compromised in this campaign. BladedFeline’s PrimeCache also shares code similarities with OilRig’s #RDAT backdoor. Moreover, as does OilRig, BladedFeline targets organizations in the Middle East.
IoCs will be available in our GitHub repo: https://github.com/eset/malware-ioc/tree/master/