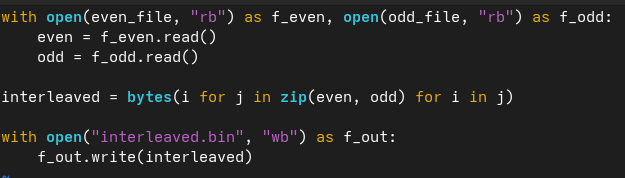
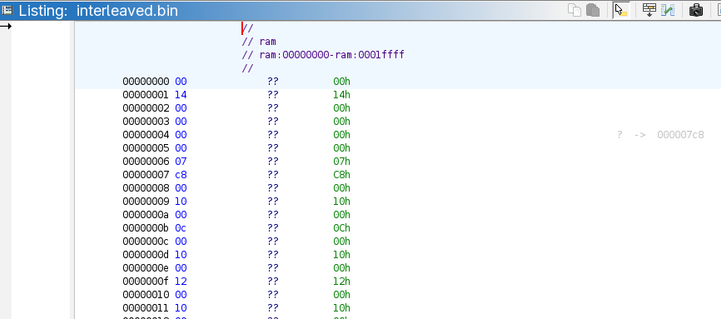
I had this script where I thought I fixed a bug by referencing X.y.z instead of X.z. Except nothing changed, the buggy behavior is still there (the file output contains garbage).
I add logging, the logs appear and show everything is fine.
Add more logs, exceptions even (to stop at a specific state). They run and show all is fine.
After I restart Ghidra the bug is gone.
To be clear: there must be some kind of bytecode caching that affects my object reference but does not affect additional logging/exception throwing??
Any ideas?