Aquest cap de setmana vaig organitzar la r2con, un congrès sobre enginyeria inversa amb el software lliure #radare2 on vaig fer un parell de xerrades.
Avui he penjat les diapositives i posat els enllaços als videos. Ho deixo per aqui per si voleu fer-hi un cop d'ull
* TocTouMaps https://github.com/radareorg/r2con2025/tree/main/TocTouMaps
* VibeReversing https://github.com/radareorg/r2con2025/tree/main/VibeReversing
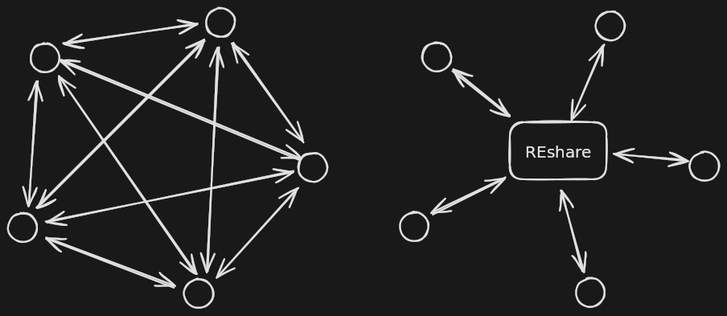
https://github.com/v-p-b/reshare/
The code is still in its early days (literally) but the fact that it works with complex, real life binaries tells me that this goal is worth pursuing.
I'm looking for contributors, esp. for #BinaryNinja, #IDA and #radare2 scripting so we can bring all these worlds together!
#r2con2025 is BACK October 24-25, streamed fully online for the first time! Whether you’re using #radare2 or curious, we’ve got sessions on emulators, Rust binaries, shellcode morphing & more. See the full agenda here: https://loom.ly/eFyEuVY
The recording of our @Defcon talk is now available. We shared our approach to reversing IoT and OT malware written in Go using a hybrid toolkit that blends AI with traditional analysis methods using #Radare2 , #Ghidra, and #BinaryNinja. Thanks to everyone who came out and stayed engaged through the technical hiccups that the venue had. We had to improvise and share a link for the slides on the spot.

DEF CON 33 - Go Malware Meets IoT - Challenges, Blind Spots, and Botnets - Asher Davila

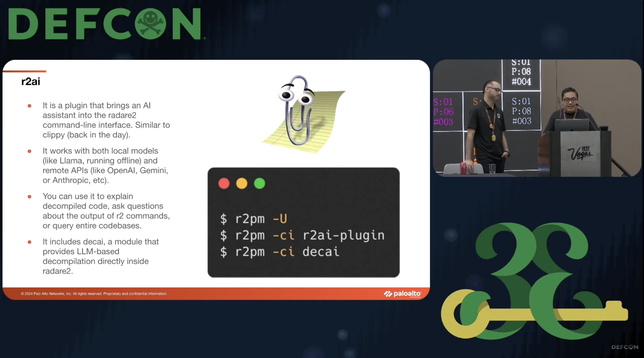
Local Agentic Reversing | Sergi Álvarez (PANCAKE)
GitHub - gum3t/chameleon: Chameleon is a polymorphic engine for x86_64 position independent shellcode that has been created out of the need to evade signature-based detections in red team environments.
Chameleon is a polymorphic engine for x86_64 position independent shellcode that has been created out of the need to evade signature-based detections in red team environments. - gum3t/chameleon
🚀 Introducing #r2morph , a metamorphic binary transformation engine built on @radareorg + #r2pipe.
It applies semantic mutations (NOPs, instruction swaps, dead code, opaque predicates…) without breaking functionality.
🧠 Perfect for research on evasion, obfuscation & malware analysis.