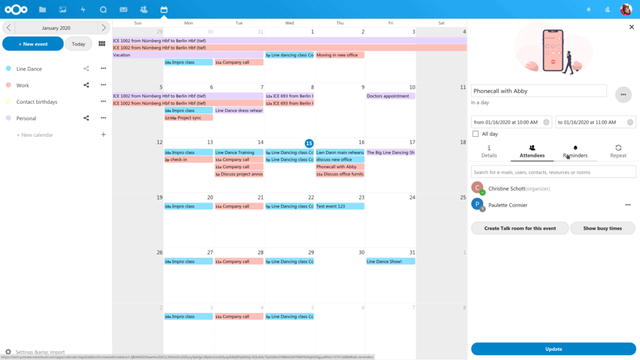
For #screenReader users, that might not be as simple as all that due to #accessibility reasons. This weekend's IC_Null stream aims to dig into this, but I need your help. What tools, services etc. should I look at from an #accessibility perspective? Anyone here who needs their tools evaluated? Anyone here who's curious about a particular tool or suite of tools? Let me know and I'll add it to the list. Anything goes. #selfHosting #blind #tech #EU
For #screenReader users, that might not be as simple as all that due to #accessibility reasons. This weekend's IC_Null stream aims to dig into this, but I need your help. What tools, services etc. should I look at from an #accessibility perspective? Anyone here who needs their tools evaluated? Anyone here who's curious about a particular tool or suite of tools? Let me know and I'll add it to the list. Anything goes. #selfHosting #blind #tech #EU
「AIによる業務効率化」に特化、Dropbox Japanが公式noteアカウントを開設
https://ascii.jp/elem/000/004/293/4293559/?rss
📝 Список із посиланнями на інструкції з увімкнення двофакторної автентифікації (2FA) для найпопулярніших онлайн-сервісів.
Часиина 2👇
🔹 #X
🔗 https://help.twitter.com/en/managing-your-account/two-factor-authentication
🔹 #Discord
🔗 https://support.discord.com/hc/en-us/articles/219576828
🔹#Amazon
🔗 https://www.amazon.com/gp/help/customer/display.html?nodeId=G2NHT5RDYHRY57EK
🔹 #Dropbox
🔗 https://help.dropbox.com/account-access/enable-two-step-verification
🔹 #Zoom
🔗 https://support.zoom.com/hc/en/article?id=zm_kb&sysparm_article=KB0066054
🔹#Reddit
🔗 https://www.reddit.com/2fa/enable/
🔹 #GitHub
🔗 https://docs.github.com/en/authentication/securing-your-account-with-two-factor-authentication-2fa
Warning Against Distribution of Malware Disguised as Research Papers
The Kimsuky group has launched a sophisticated phishing attack disguised as a request for paper review from a professor. The attack involves a password-protected HWP document with a malicious OLE object, which creates six files upon opening. When executed, these files perform various malicious activities, including collecting system information, downloading additional files, and establishing remote access through AnyDesk. The threat actors use legitimate software and cloud storage services like Dropbox as part of their attack infrastructure. The malware hides its presence by concealing AnyDesk's interface, making detection difficult for users. This case highlights the evolving tactics of APT groups and the importance of cautious handling of files from unknown sources.
Pulse ID: 6852fb62bacdd68c9f8c2a81
Pulse Link: https://otx.alienvault.com/pulse/6852fb62bacdd68c9f8c2a81
Pulse Author: AlienVault
Created: 2025-06-18 17:46:10
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AnyDesk #Cloud #CyberSecurity #Dropbox #ICS #InfoSec #Kimsuky #Malware #OTX #OpenThreatExchange #Password #Phishing #RCE #UK #Word #bot #AlienVault
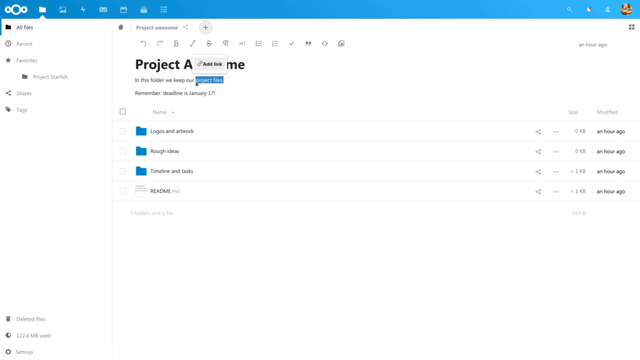
Nextcloud, l’alternativa a Google Drive
Nextcloud, l’alternativa a Google Drive. La suite di Nextcloud è davvero il meglio che potete trovare, noi vi elenchiamo alcuni hosting affidabili!
https://www.lealternative.net/2020/06/04/nextcloud-lalternativa-a-google-drive/
But now I have to face the problem of synchronisation to use multiple devices.
A self hosted #Nextcloud would be the best. But I don’t have it. #Onedrive, #Dropbox und #S3 are no choice due to known reasons.
So the only option I have so far would be the cloud of @joplinapp.
But will my data be safe there? Where is the cloud hosted? US and countries where government can get access to it are a noGo
Looking at #NextCloud as an alternative to #dropbox. Also looking at Nextcloud providers. It's a lot. Any advice?
Anything I pick I will use #cryptomator with it, because I don't trust the cloud with my encryption passphrase. :)
Just published a patch version update of the #Dropbox extension for #joomla
With it you can publish and show files that you have in your cloud storage directly on your website, without having to upload them again.
Demo: http://joomla.in-nepal.de/index.php/en/?option=com_dropbox&id=1
We are still working on allowing to connect also @OpenCloud and #ownCloud oCIS to Joomla
 ASCII.jp - トップ
ASCII.jp - トップ