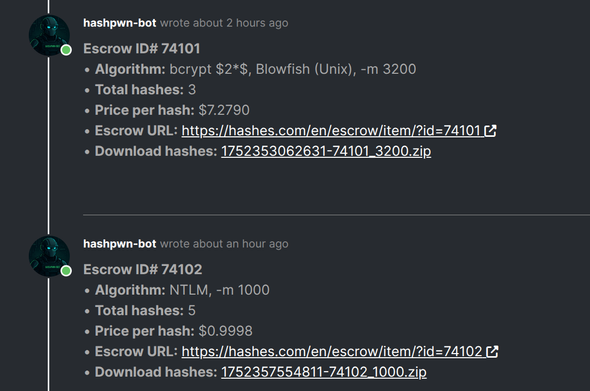
🆕 blog! “It is 1939 and you want to use public-key cryptography”
Imagine, just for a moment, that a mathematical breakthrough had occurred on the eve of the second World War. Perhaps Turing or Rejewski or Driscoll realised that prime number theory held the key to unbreakable encryption. This blog post attempts to answer the question "could public-key …
👀 Read more: https://shkspr.mobi/blog/2025/07/it-is-1939-and-you-want-to-use-public-key-cryptography/
⸻
#ComputerScience #encryption

It is 1939 and you want to use public-key cryptography
Imagine, just for a moment, that a mathematical breakthrough had occurred on the eve of the second World War. Perhaps Turing or Rejewski or Driscoll realised that prime number theory held the key to unbreakable encryption. This blog post attempts to answer the question "could public-key cryptography have been used in 1939?" Let's briefly step back into history. The Enigma machine represented…