🚨 CVE-2025-3248: Renewed Interest in Langflow Remote Code Execution
ℹ️ About the exploit:
#Langflow is a widely used #opensource library for building AI agents, backed by corporate support from #Datastax (now #IBM). The tool provides a web-based, drag-and-drop interface for creating agentic workflows, making it particularly attractive to businesses, but also a high-value target for exploits. Given that such workflows often integrate with critical business databases and tools, security vulnerabilities in Langflow could have severe consequences.
This risk is not hypothetical. Langchain, another leading AI framework, has already been associated with over 30 CVEs, underscoring the security challenges in the fast-moving LLM development ecosystem.
The vulnerability in Langflow allowed unauthenticated attackers to execute arbitrary code on the host machine. Discovered and disclosed by Horizon3 in late February, the issue was patched in version 1.3, released at the end of March. Below is a detailed timeline of the discovery and remediation process.
🔎 Trend analysis:
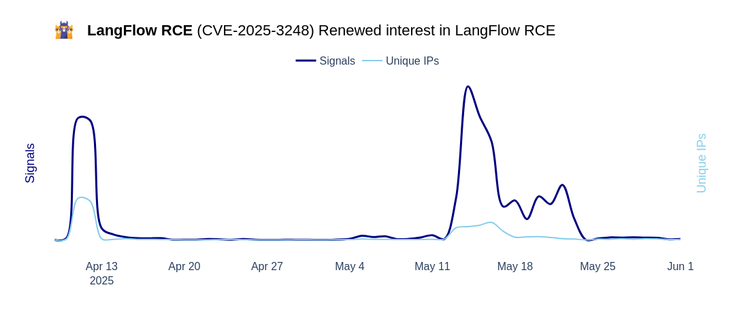
🔹 Feb 25, 2025: The vulnerability is disclosed to DataStax by Horizon3.
🔹 Mar 5, 2025: DataStax fixes the vulnerability in the development branch.
🔹 Mar 31, 2025: Langflow 1.3.0 releases, containing a fix for CVE-2025-3248.
🔹 April 7, 2025: CVE-2025-3248 is published to the NVD.
🔹 April 9, 2025: The exploit is leaked to the public, and the CrowdSec Network starts tracking the exploit.
🔹 April 11-12, 2025: The CrowdSec Network observes a first wave of exploitation attempts by approximately 200 machines.
🔹 April 12 - May 14, 2025: Attackers disappear, with barely any attacks registered in the CrowdSec Network.
🔹 May 14 - 23, 2025: The CrowdSec Network observes a renewed, smaller wave of attacks, peaking out at around 100 involved machines.
✅ How to protect your systems:
🔹Patch: If you haven’t already, ensure your publicly exposed Langflow instance is updated with the latest patch.
🔹Preemptive blocking: Use Crowdsec CTI to block IPs exploiting CVE-2025-3248 👉 https://app.crowdsec.net/cti?q=cves%3ACVE-2025-3248
🔹Stay proactive: Install the Crowdsec Web Application Firewall to stay ahead of exploit attempts with 100+ virtual patching rules available 👉 https://app.crowdsec.net/cti?q=cves%3ACVE-2025-3248
Sharing insights and taking swift action can collectively reduce the impact of these threats. This is your call to action for real-time threat intelligence and #collaborative #cybersecurity 👉 http://crowdsec.net/
 LangChain helps us build LLM apps via modular code.
LangChain helps us build LLM apps via modular code. LangGraph adds branching logic and multi-agent workflows.
LangGraph adds branching logic and multi-agent workflows. LangFlow lets us create flows with drag & drop.
LangFlow lets us create flows with drag & drop. LangSmith monitors and evaluates our LLM stack.
LangSmith monitors and evaluates our LLM stack.