https://www.wacoca.com/news/2646503/ 対イラン国連制裁、月内に復活の公算=仏大統領 | ロイター #AMERS #Asia #ASXPAC #BRU #CEEU #CWP #de #Def #DEST:NOJPTPM #DEST:NOJPWDM #DEST:NOJPZTM #dip #EMEA #EMRG #EU #EUROP #EZC #fr #France #GB #Gen #IAEA #IL #INTAG #IR #JFOR #JLN #MEAST #MTPIX #NAMER #NEWS1 #NUCL #POL #REPI:GOVERNANCE #SECUR #SWASIA #TGLF #TOPCMB #TOPNWS #TRD #TRDEMB #TRN #US #WEU #フランス
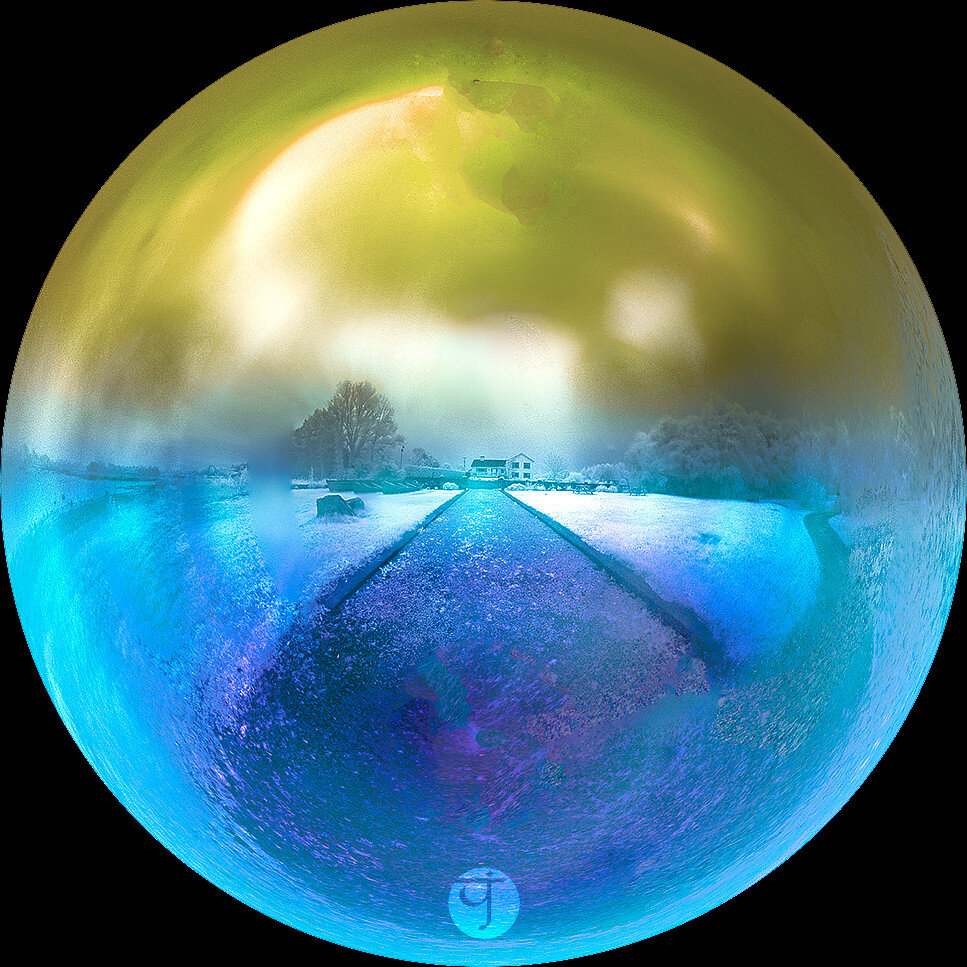
Circularium Samhna (2014)
Well, not Halloween yet (I guess?) but something for it in advance. One of the early panoramas that I've shot using infrared filter and a regular camera. The panorama was problematic for the lack of details in the sky, so the stitcher had a hard time putting things together. Originally, I did this manually, but now I'm re-doing it in a haste, so I didn't fix much about it (hence the foggy dirty look which I think serves the mysterious haunted look right). In the end, I've played around with the colors a bit, reversing the channels on the upper half of the sphere and leaving it as is in the lower half.
Thought on the side: How do they celebrate Halloween in the southern hemisphere? I mean the weather is getting colder and all of that which gives it a chill, but down there it is the opposite season (technically spring) and the night span is also different and all - hmm 🤔
#ireland #irish #oughterard #galway #gaillimh #sphere #haunted #samhain #samhna #IR #infrared #infrarot #infrarouge #infrarojo #panorama #panoramic #circular #circle #360pano #360panorama #surreal #surrealism #goodmorning
Well, not Halloween yet (I guess?) but something for it in advance. One of the early panoramas that I've shot using infrared filter and a regular camera. The panorama was problematic for the lack of details in the sky, so the stitcher had a hard time putting things together. Originally, I did this manually, but now I'm re-doing it in a haste, so I didn't fix much about it (hence the foggy dirty look which I think serves the mysterious haunted look right). In the end, I've played around with the colors a bit, reversing the channels on the upper half of the sphere and leaving it as is in the lower half.
Thought on the side: How do they celebrate Halloween in the southern hemisphere? I mean the weather is getting colder and all of that which gives it a chill, but down there it is the opposite season (technically spring) and the night span is also different and all - hmm 🤔
#ireland #irish #oughterard #galway #gaillimh #sphere #haunted #samhain #samhna #IR #infrared #infrarot #infrarouge #infrarojo #panorama #panoramic #circular #circle #360pano #360panorama #surreal #surrealism #goodmorning
https://www.wacoca.com/2047574/ アクシスコンサルティング(9344)個人投資家向けIRセミナー【資料・アンケートは概要欄から】 #Female #IR #IRセミナー #RyokoYonekura #YonekuraRyoko #アシロ #企業分析 #個人投資家 #投資 #機関投資家 #決算説明会 #決算速報 #米倉涼子
https://www.wacoca.com/news/2645213/ 核問題巡り平行線、イランと欧州3カ国が外相協議 | ロイター #AMERS #Asia #ASXPAC #CEEU #CWP #de #Def #DEST:NOJPTPM #DEST:NOJPWDM #DEST:NOJPZTM #dip #EMEA #EMRG #EU #EUROP #Europe #EZC #fr #GB #Gen #IAEA #IL #INTAG #IR #JFOR #JLN #MEAST #MTPIX #NAMER #NEWS1 #NUCL #POL #REPI:GOVERNANCE #SA #SECUR #SWASIA #TGLF #TOPCMB #TOPNWS #TRD #TRDEMB #TRN #UN1 #US #WEU #ヨーロッパ #欧州
Infrarotkuh auf Hiddensee | 1/80s | f4 | 264 mm | ISO 400 | DMC-FZ100 (Vollspektrum-Umbau)
Alle Farben sind genau so in der Kamera entstanden – dank des entfernten Infrarotfilters (alles ganz ohne Photoshop!). Mehr Infos über die Infrarotfotografie habe ich hier zusammengetragen:
- https://pixelfed.de/p/pixelstreet/568566825746599726
- https://pixelfed.de/p/pixelstreet/777514038362879797
- https://pixelfed.de/p/pixelstreet/572530744117900567
#Hiddensee #infrarot #tierfoto #tierfotografie #vollspektrum #ir #cir #PseudoCIR #natur #infrarotfoto #infrarotfotografie #farbinfrarot #falschfarbfoto #falschfarben #foto #fotografie1
#infrared #FullSpectrum #FullSpectrumPhotography #animal #AnimalPhoto #AnimalPhotography #nature #InfraredPhoto #InfraredPhotography #ColourInfrared #FalseColour #ColorInfrared #FalseColor #photo #photography
Alle Farben sind genau so in der Kamera entstanden – dank des entfernten Infrarotfilters (alles ganz ohne Photoshop!). Mehr Infos über die Infrarotfotografie habe ich hier zusammengetragen:
- https://pixelfed.de/p/pixelstreet/568566825746599726
- https://pixelfed.de/p/pixelstreet/777514038362879797
- https://pixelfed.de/p/pixelstreet/572530744117900567
#Hiddensee #infrarot #tierfoto #tierfotografie #vollspektrum #ir #cir #PseudoCIR #natur #infrarotfoto #infrarotfotografie #farbinfrarot #falschfarbfoto #falschfarben #foto #fotografie1
#infrared #FullSpectrum #FullSpectrumPhotography #animal #AnimalPhoto #AnimalPhotography #nature #InfraredPhoto #InfraredPhotography #ColourInfrared #FalseColour #ColorInfrared #FalseColor #photo #photography
If you're in Vienna, and are wondering what Victorian romance, Ukrainian progressive metalcore, library science, Brazil (1985), the Pope, and more have to do with ethical, human-driven information access, and whether we should put LLMs into everything, come join us tomorrow evening! #RecSys #IR https://hci.social/@mdekstrand/115191259701673286
Mustang Panda (Hive0154) rolled out SnakeDisk (USB worm) + Toneshell9/Yokai backdoor to target air-gapped networks (geo-targeted to Thailand). Indicators: hidden SYSTEM/HIDDEN dirs on USB, robocopy/SHFileOperation usage, payloads reconstructed in C:\Users\Public\, scheduled tasks for persistence. Immediate mitigations: enforce approved read-only media, disable autorun, monitor WM_DEVICECHANGE/IOCTL, block DLL sideloading, and scan media in isolated sandboxes.
Follow @technadu for IOCs & response playbooks.
#MustangPanda #USBWorm #AirGapSecurity #ThreatIntel #EDR #IR #InfoSec #Malware
Last day of summer • Infrared • Niederkaufungen • Hesse • Germany … #alternatiffotograf #andreaslbergphotography #art #artist #blackandwhite #bw #clouds #cloudyday #dynamic #fineartzone #fotografie #germany #hessen #infrared #infrared_images #infraredphotographer #infraredphotography #infrarot #ir #nature #nordhessen #photography #schwarzweiss #sharp #silentsunday #sky #Sommer #summer https://www.andreas-l-berg.com/blog/last-day-of-summer/
「2026年3月期 第2四半期 決算発表予定日」を掲載しました。
https://www.nintendo.co.jp/ir/schedule/index.html
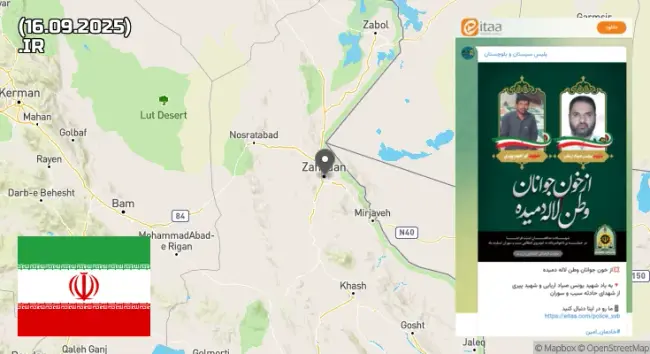
Неизвестные обстреляли патрульный автомобиль и убили 2 полицейских в Иране #ir https://contrafront.ru/ir/2046







 任天堂ホームページ更新情報
任天堂ホームページ更新情報