I successfully tested a LSASS dumping technique on a Windows 10 lab machine, which we encountered on a recent Incident Response engagement (no EDR, default Defender installed).
The "MiniDumpWriteDump" technique, as described here [1], was successful in writing the LSASS process to disk.
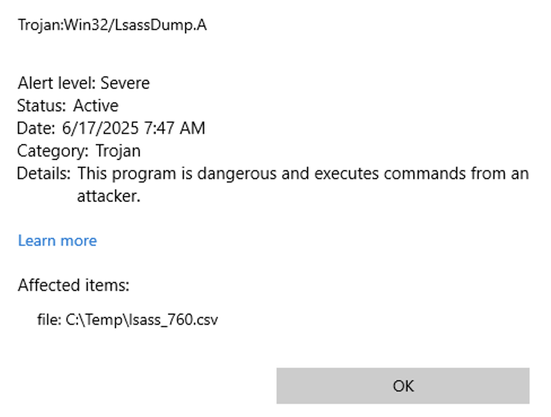
However, as soon as I tried to copy the dump to my Kali machine, Defender jumped into action, prohibited access to the LSASS dump, and removed the file to the quarantine. And here is the catch.
I browsed to the following folder:
C:\ProgramData\Microsoft\Windows Defender\Quarantine
In the ResourceData folder, you will find different sub-folders (or not, if Defender never quarantined something on that host), each folder containing a quarantine file.
The files are encrypted with a static key that leaked years ago, and this 10-year-old code snippet is still sufficient to decrypt the files back to their original state. [2]
Long story short: I copied the encrypted file to my Kali machine, decrypted it using the Python code from [2], and extracted the credentials and hashes with pypykatz. [3]
Classic example of "No, it's not enough when your AV blocked or removed a threat". As you can see, an attacker can easily get the LSASS dump, even if Defender removed it from the disk ¯\_(ツ)_/¯
[1 ]https://www.ired.team/offensive-security/credential-access-and-credential-dumping/dumping-lsass-passwords-without-mimikatz-minidumpwritedump-av-signature-bypass
[2] https://raw.githubusercontent.com/malmoeb/DFIR/refs/heads/master/quarantine.py
[3] https://github.com/skelsec/pypykatz