| website | https://goncalor.com |
| GitHub | https://github.com/goncalor |
Gonçalo Ribeiro
- 342 Followers
- 446 Following
- 3.4K Posts
At the Comedy Wildlife exhibition in Madrid.
https://www.mncn.csic.es/es/visita-el-mncn/exposiciones/comedy-wildlife-premios-de-fotografia
> AI assistance was used to help structure and format this vulnerability report.
That was a really stupid idea.
Edinburgh Castle stands on Castle Rock, which has been occupied by humans since at least the Iron Age.
https://theweeowlart.etsy.com/listing/1886833786
#FediGiftShop #ScottishArtist #MastoArt #CreativeToots
#Landscape #Edinburgh #Scotland #OriginalArt #Drawing #PenAndInk #ColourPencil #MixedMedia #Painting #Artwork #TraditionalArtist #ArtFromScotland #GiftIdeas #ArtShop
Faking a JPEG | Lobsters
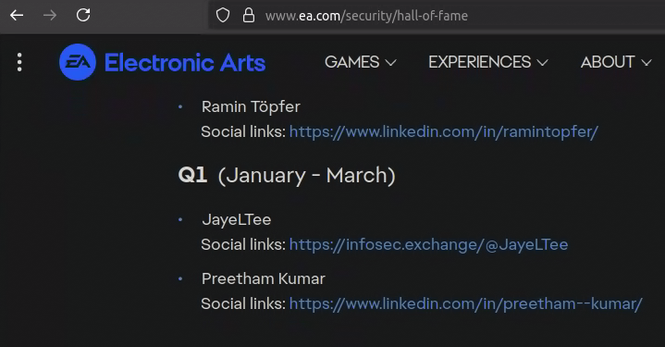
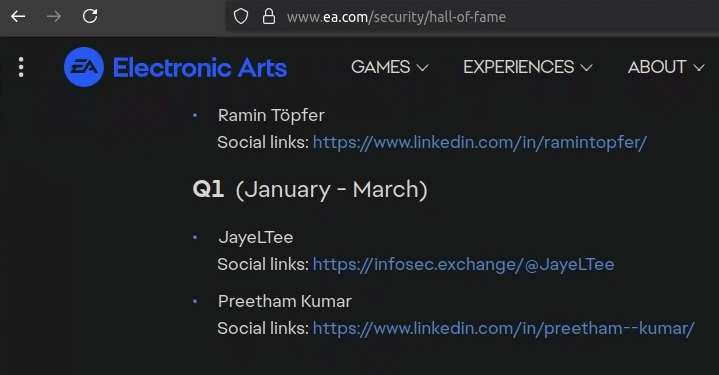
I received an email earlier this week from EA asking if I wanted to be added to a public acknowledgement page they were creating for individuals who responsibly disclosed vulnerabilities to them.
For all the shit people give EA, of the 100+ companies I contacted in the last two years, they were the only company I would say had a decent incident response.
They fixed the issue within 12 hours after validating it as critical, and proactively provided me multiple updates over time.
When the IR was done on their side, they reached out again with some more information about the potential impact if the issue hadn't been solved quickly, and also offered me a reward.
I did not have to keep chasing anyone for updates, I wasn't asked for non-disclosure, or offered money in exchange for it, and people replied instead of ignoring me.
I wasn't blamed for their mistake, either, or reported to the authorities.
Unfortunately, at least one or multiple of the things mentioned above are present in most of my other incidents reported; it's a real shit show out there.
#cybersecurity #infosec #responsibledisclosure #vulnerability #ea #electronicarts