SonicWall now claims 347-Day:
https://www.sonicwall.com/support/notices/gen-7-and-newer-sonicwall-firewalls-sslvpn-recent-threat-activity/250804095336430
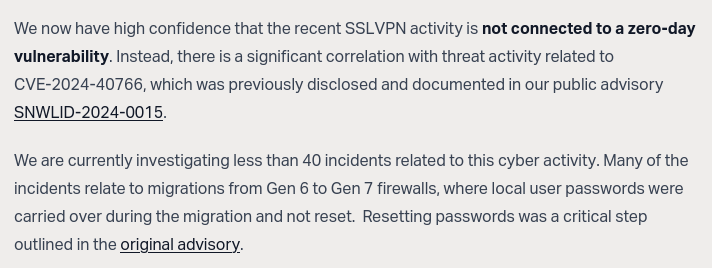
> We now have high confidence that the recent SSLVPN activity is **not connected to a zero-day vulnerability**. Instead, there is a significant correlation with threat activity related to CVE-2024-40766, which was previously disclosed and documented in our public advisory https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0015.
> We are currently investigating fewer than 40 incidents related to this cyber activity. Many of the incidents relate to migrations from Gen 6 to Gen 7 firewalls, where local user passwords were carried over during the migration and not reset. Resetting passwords was a critical step outlined in the original advisory.
"Critical Step" as in
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0015#:~:text=Recommended%20Actions
> SonicWall strongly recommends that all users of GEN5 and GEN6 firewalls with locally managed SSLVPN accounts immediately update their passwords to enhance security and prevent unauthorized access. Administrators must enable the "User must change password" option for each local account. Alternatively, they can use a bulk change automation script available [at] https://github.com/sonicwall/sonicos-automation.