Welp, after 21 years with Blizzard Entertainment, I was laid off today. What an incredible journey. I got to be part of challenging, exciting projects, and I played a part in shaping the company's voice for over two decades.
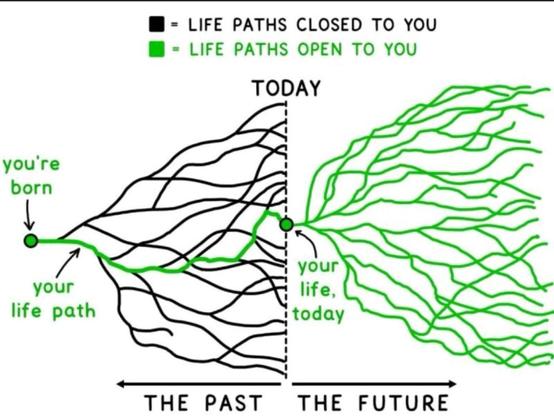
One thing you learn living in California is that the most intense growth usually follows after a wildfire. Some plants even require fire to release their seeds.
So we'll see what comes next. If you need an editor on your team, hit me up.



 , powered by sarcasm
, powered by sarcasm