ARINC SelfServ vMUSE devices are down in airports in EU, they do self service check in. They’re connected to navAviNet aka ARINC Ground Network, managed by Collins Aerospace, who are owned by RTX.
An attacker got onto to the shared network.
ARINC SelfServ vMUSE devices are down in airports in EU, they do self service check in. They’re connected to navAviNet aka ARINC Ground Network, managed by Collins Aerospace, who are owned by RTX.
An attacker got onto to the shared network.
Shodan dork if you wanna rubberneck:
org:"ARINC INCORPORATED"
6x AnyConnect VPN boxes offline
BBC good reporting on the ground impact
In theory it should be minimal but in practice airlines have automated many jobs so we’ll see.
If any journalists want a list of top impacted airports to check: https://infosec.exchange/@nieldk/115237394885804514
BBC have Dublin and Cork added.
@cirriustech @GossiTheDog@cyberplace.social here are the “top ten” airports using vMUSE. See any you recognize in Europe as listed in current incident ;) 1. London Heathrow (LHR) 2. Glasgow Airport (GLA) 3. Berlin Schönefeld (SXF) 4. Dublin Airport (DUB) 5. Cork Airport (ORK) 6. Cologne Bonn Airport (CGN) 7. Mazatlán International Airport (Mexico) 8. Zihuatanejo International Airport (Mexico) 9. Monterrey International Airport (Mexico) 10. Velana International Airport (Maldiverne)
ARINC are flying engineers out to airports to try to fix terminals.
Brussels airport, EBBR, have issued this NOTAM: “AD LTD DUE TO AN IT SYSTEM DISRUPTION. AIRLINES ARE TO CANCEL 50
PERCENT OF THEIR DEPARTING PASSENGER FLIGHTS IN THIS TIMEFRAME”
The ARINC incident continues https://www.bbc.co.uk/news/articles/cwy88857llno
Also for anybody interested, ARINC is where the cyber incident is.
ARINC were basically the OG airport network provider, from 1929. ARNIC were sold to Carlyle Group (private equity) in 2007, who sold them to Rockwell Collins in 2013, who sold to United Technologies in 2018, who merged to form Collins Aerospace. Their network looks a mess of US corporate shenanigans… webmail doesn’t even require https yet 😅
Worth noting that airplanes are incredibly safe and resilient after extensive regulation and open and transparent investigations of every air incident…
when you land on the ground, however, air travel is caught in the same cybersecurity bullshit every other industry is caught up in.
After ARINC restored domain controllers from backup, the threat actor got back in and started trashing more stuff. 🫡
The whole thing is a mess, they probably want to pause, take a breathe, and think about flushing out attacker before rebuilding things.
Berlin Airport ran at 70% delays yesterday
I’ve confirmed today that Heathrow, Berlin and Dublin all still have no Muse terminals restored. I haven’t checked other airports. It’s even more complicated because Muse both processes and stores biometrics of passengers.
"Before we reconnect our system, we must be 100% sure that there are no malware programmes left," the BER spokesman said.
The Europe airlines ransomware situation is a variant of Hardbit ransomware, which doesn’t have a portal and is incredibly basic.
They’ve had to restart recovery again as the devices keep getting reinfected. I’ve never seen an incident like it. Somebody like the NCSC needs to go in and help them with IR.
Look at Dublin airport, reporters starting to realise it never actually got fixed 😅
https://www.thejournal.ie/dublin-airport-issues-timeline-fix-6824817-Sep2025/
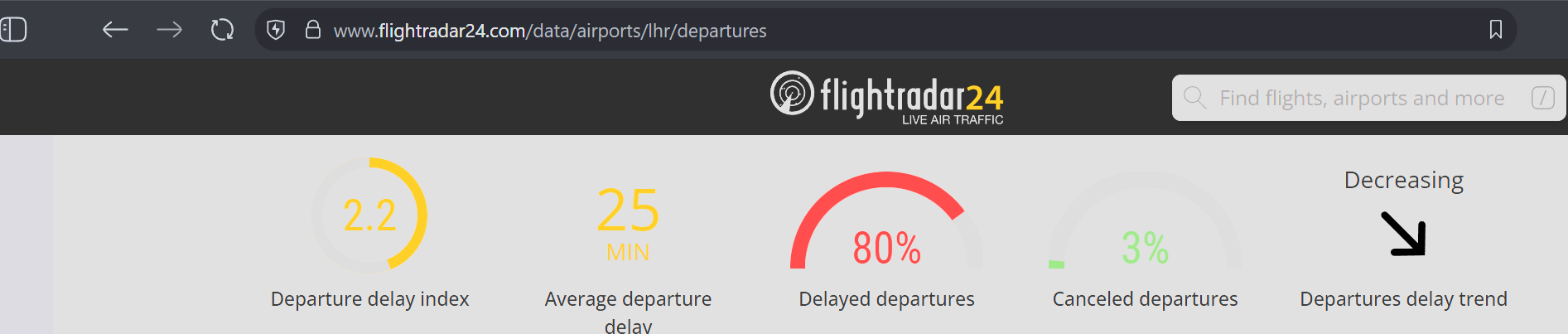
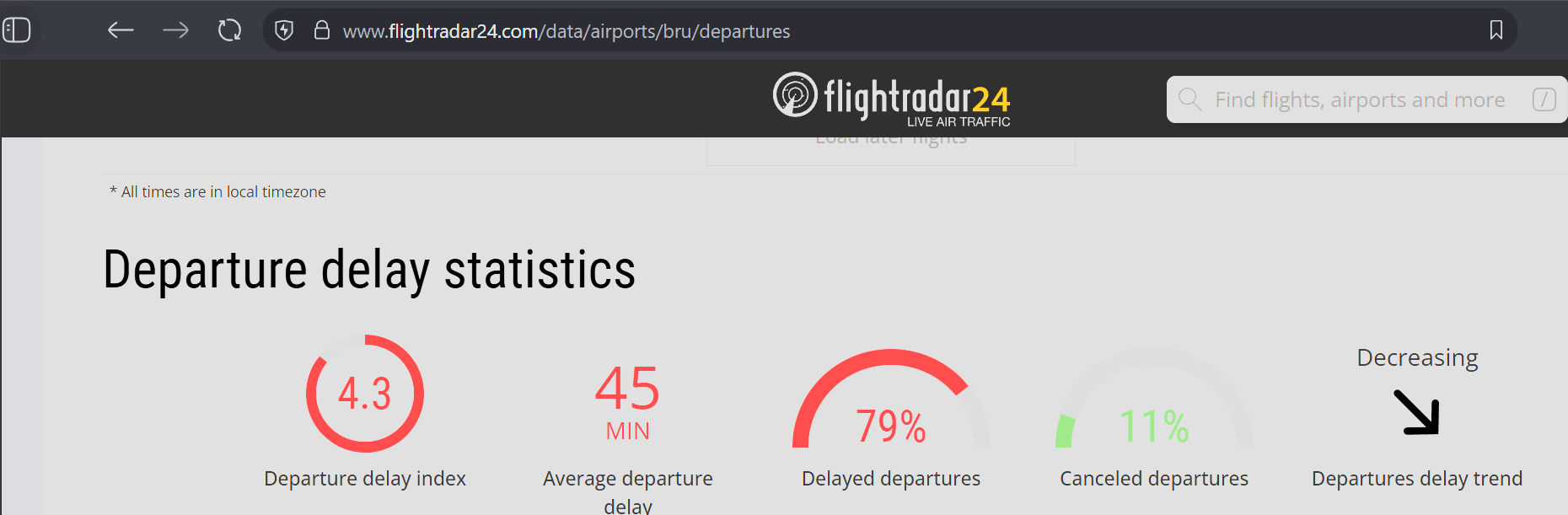
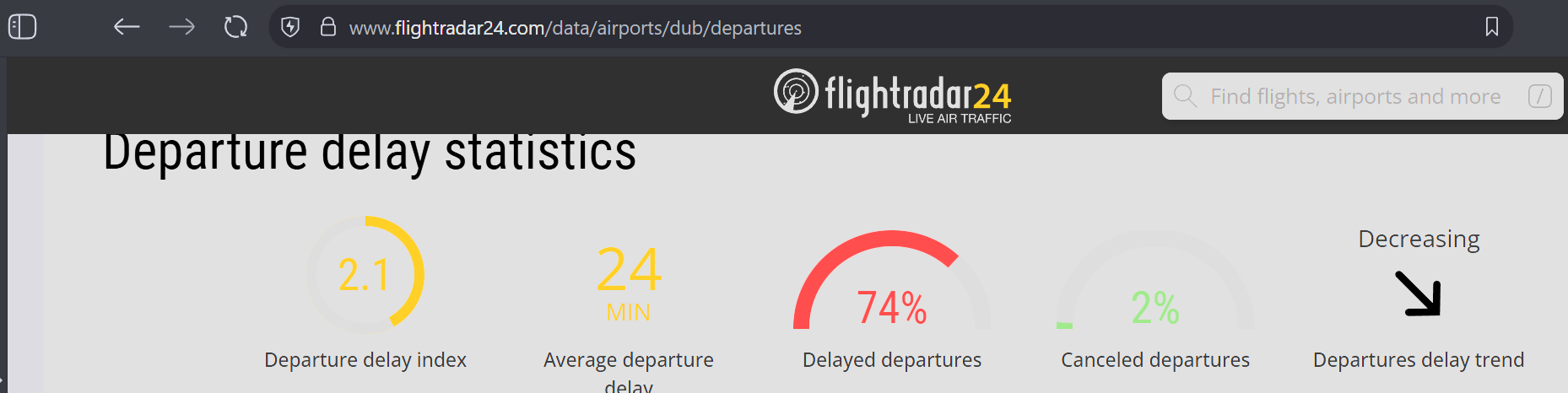
Flight delays today:
Heathrow 78%
Brussels 79%
Dublin 68%
Berlin 86%
All are vMuse. London City isn't on vMuse, they're at 35% as a point of comparison.