I’ll spell it out for you guys - CBP provides open free WiFi in the immigration line at the airport where the typical person with no mobile service is on a visa.
This is a very different consideration now in the era of wiping phones than three years ago.
@hacks4pancakes So even without MITM, they can work-out what your device has been accessing.
So if you say you don't use Twitter, they can catch on a lie and send you back.
What else?
@hacks4pancakes It took me this post to realize that CBP meant Customs and Border Patrol rather than Citizens Bank Park.
(And how those two in contrast feel very uncomfortable.)
I'll assume US Customs and Border Control... and where they could slurp up anything datawise they want - even phone calls themselves, for those using phones/providers capable of WiFi calling. That might only be tip of the iceberg.
Social engineering at its worst.
Let's stop spreading FUD: The Internet has never been safer before for consumers. Anyone trying to do weird MITM in the WiFi you're connected to will have your phone show endless scary red warnings.
And police and intelligence agencies have repeatedly said metadata can be more useful than the message content.
@hacks4pancakes @lumiworx every FW in the history of ever uses the 1st few unencrypted bits of TLS to make security choices. How do ppl think DPI works? Luckily only trust worthy orgs know this.
So no, we are not living in the golden age of secure channels.
Maybe one day when ECH is deployed and browsers correctly handle HTTPS records and unicorns fart rainbows we will get there.
@hacks4pancakes @lumiworx there is also the issue of how the end user would handle these warnings, should they exist
A lot of end users have endless notifications that they have been ignoring, and security is unlikely to rank higher than any of those in their mind
Especially in a situation where they are probably stressed out and just trying to get through this
@GuillaumeRossolini @hacks4pancakes
A valid and interesting point. My gut tells me it might come down to the users themselves always having to be preemptive about any nonsense from outside sources, long before it would be needed. Phone providers - much like internet providers - aren't providing much security that I've seen so far. Aside from Android 16 giving alerts to StingRay switching to 2G/3G.
Users are left to protect their own devices. Does FairPhone or Nothing load anything by default?
@hacks4pancakes @lumiworx
Step 1: Have an organization with access to a widely used CA (to avoid having to install the CA on client devices)
Step 2: Have a TLS MITM configuration on the router for the public wifi
Step 3: Profit?
I believe i remember something like that for enterprise "security"...
This was something like a certificate rewrite, so that the router infra could decrypt/reencryt transparently and sniff the packets...
I will never make assumptions about the capability of superpower governments to do what others call impossible.
I also won't make assumptions about the technical savvy of each and every potential user in line at CBP check points or that they use the latest and greatest hardware/OS and the security features they may have or lack.
@somebody @ulveon @hacks4pancakes
I'm too old and too damn grumpy to give a shit anymore, so if I knew magic, I'd be holding classes 3 days a week. 😃
@ulveon @hacks4pancakes @lumiworx if you connect your phone to this it's almost certainly possible to build a profile that the phone with MAC xxyyzz is being used with a Google account, Apple, Facebook, WhatsApp, Instagram, Signal, Telegram, X, Bluesky, Truth Social, TikTok, reddit, Microsoft personal, Microsoft business, and a variety of other services because all of those will connect automatically behind the scenes for updates. Boom, there's your checklist of services for an agent to check for thoughtcrime.
Some Android devices automatically randomize MACs but not all (and may not randomize device names), and it looks like Apple devices don't default to randomizing AND it's an option that you have to set for each network you connect to. So, even if some users are using everything they can (or simply not connecting) this could impact many or most.
Heck, take the next step: while checking your device, they connect to that network with MAC randomization and Private Relay or VPN disabled. Didn't get a list of services before? You have one now.
@ulveon @hacks4pancakes @lumiworx Yeah, this isn't even correct. The fact you can even try to say this as confidently as you just did, is sort of amazing.
Just too ignorant of how it works to know better, hopefully.
@NosirrahSec @hacks4pancakes
@somebody
Well, if I've learned nothing more - today has certainly shown that I truly may be grateful that toot quotes will soon be available, so I can at least tell who's yelling at who.
@NosirrahSec @hacks4pancakes @somebody
No worries... Hopefully I can still 'read the room', and I certainly didn't think it was directed toward me, anyway.
I would much prefer for things to get steered openly into a discussion stage when it could be relevant, and it is far more than a little relevant right now.
What do you know the pocket fisherman and the chop-o-matic of surveilance.
@dalias @mattblaze @hacks4pancakes
It's an Open network. Why perform deauths when you can (absentmindedly) run an AP with the same SSID that drops all packets!
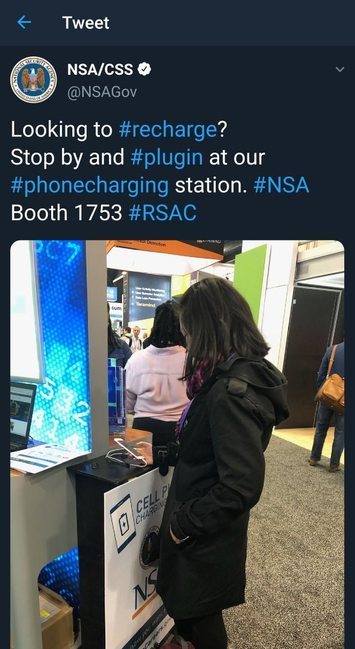
"Free phone charging, from the NSA" is always a good one.
@kc Defeated by a power-only cable.
Are their APs also listening to the phones as they scan for other APs the phones already had connected to? That could be interesting.
@sasutina13 @hacks4pancakes that is a very good question, the only part I know is that they actively offer you the WiFi and sniff what your phone is up to.
I imagine there is some kind of other device tracking hiding somewhere, wouldn’t at all surprise me if they were also running a mobile phone relay to catch those pesky non-WiFi users
1990s bro and then I would be disappeared
“Guess what y’all are accessories to!”

 🇺🇦
🇺🇦
 🌻
🌻 