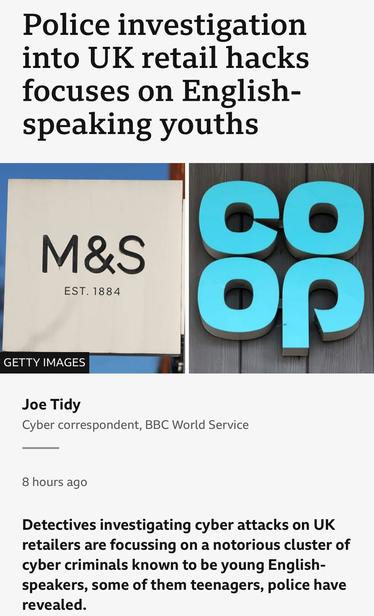
The threat actor at Co-op says Co-op shut systems down, which appears to have really pissed off the threat actor. This was the right, and smart, thing to do.
While I was at Co-op we did a rehearsal of ransomware deployment on point of sale devices with the retail team, and the outcome was a business ending event due to the inability to take payments for a prolonged period of time. So early intervention with containment was the right thing to do, 100%.























 🇺🇦
🇺🇦