Co-op Group have told their suppliers that "systemic-based orders will resume for ambient, fresh, and frozen products commencing Wednesday 14 May". They say forecasting system will still be impacted.
https://www.thegrocer.co.uk/news/co-op-to-get-systems-back-on-track-after-cyberattack/704425.article
Co-op Group say they have exited containment and begun recovery phase https://www.theguardian.com/business/2025/may/14/co-op-cyber-attack-stock-availability-in-stores-will-not-improve-until-weekend
Marks and Spencer are still in containment
If you want figures for your board to set expectations in big game ransomware incidents, Co-op containment just over 2 weeks, M&S just over 3 weeks so far - recovery comes after.
In terms of external assistance, Co-op have Microsoft Incident Response (DART), KPMG and crisis comms. M&S have CrowdStrike, Microsoft, Fenix and crisis comms.
The threat actor at Co-op says Co-op shut systems down, which appears to have really pissed off the threat actor. This was the right, and smart, thing to do.
While I was at Co-op we did a rehearsal of ransomware deployment on point of sale devices with the retail team, and the outcome was a business ending event due to the inability to take payments for a prolonged period of time. So early intervention with containment was the right thing to do, 100%.
M&S have finally told staff that data about themselves was stolen: https://www.telegraph.co.uk/business/2025/05/16/ms-staff-data-stolen-by-hackers-in-cyber-attack/
You may notice I said they had staff data stolen on May 9th in this thread.
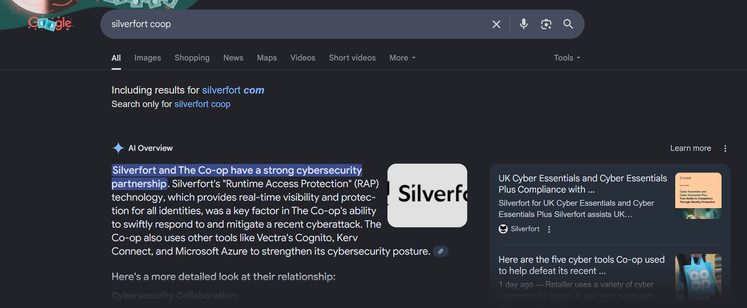
For the record, the tools listed in this article aren't used by Co-op.
The link in the article to Vectra Cognito AI has a Coop Sweden logo on it, and the Coop Sweden CISO is named. Coop Sweden is different company. Coop Sweden went on to have a ransomware attack that crippled the org, including point of sale, so I don't think it's a good sales point. Same with Silverfort.
Google AI has ingested the article and now uses it to claim Co-op Group use the tools.
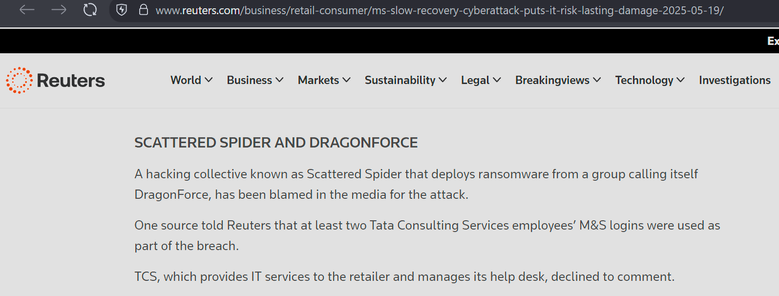
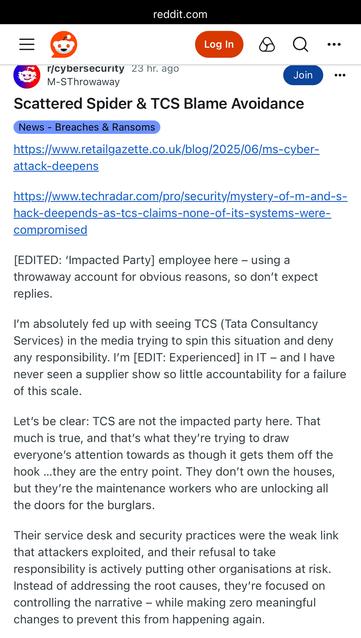
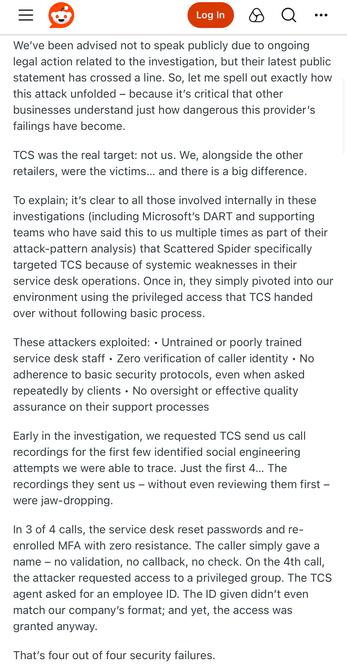
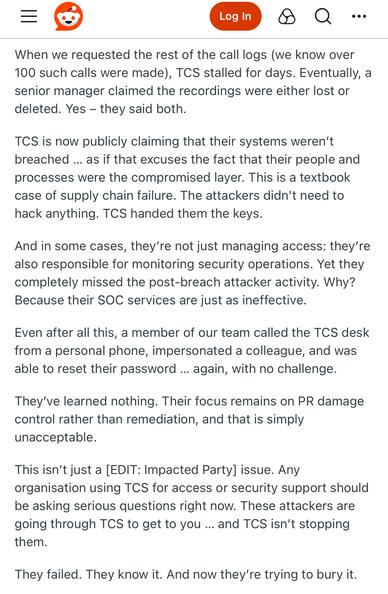
The Times reports M&S were breached through a contractor and that human error is to blame. (Both M&S and Co-op use TCS for their IT Service Desk).
The threat actor went undetected for 52 hours. (I suspect detection was when their ESXi cluster got encrypted).
M&S have told the Times they had no “direct” communication with DragonForce, which is code for they’re using a third party to negotiate - standard practice.
https://www.thetimes.com/uk/technology-uk/article/m-and-s-boss-cyber-attack-7d9hvk6ds
M&S looks to be moving to reposition their incident as a third party failure, which I imagine will help redirect some of the blame (they present their financial results during the week to investors): https://www.bbc.co.uk/news/articles/cpqe213vw3po
Both M&S and Co-op outsourced their IT, including their Service Desk (helpdesk), to TCS (Tata) around 2018, as part of cost savings.
There's nothing to suggest TCS itself have a breach btw.
Basically, if you go for the lowest cost helpdesk - you might want to follow the NCSC advice on authenticating password and MFA token resets.
I've put a 3 part deep dive blog series coming out probably next week called Living-Off-The-Company, which is about how teenagers have realised large orgs have outsourced to MSPs who follow the same format of SOP documentation, use of cloud services etc. Orgs have introduced commonality to surf.
"Cyber analysts and retail executives said the company had been the victim of a ransomware attack, had refused to pay - following government advice - and was working to reinstall all of its computer systems."
Not sure who those analysts are, but since DragonForce haven't released any data and M&S won't comment other than to say they haven't had any "direct" contact with DragonForce, I wouldn't make that assumption.
There's also a line in the article from an cyber industry person saying "if it can happen to M&S, it can happen to anyone" - it's ridiculous and defeatist given Marks and Spencer haven't shared any technical information about how it happened, other than to tell The Sunday Times it was "human error"
The Air Safety version of cyber industry would be a plane crashing into 14 other planes, and industry air safety people going "Gosh, if that can happen to British Airways it could happen to anybody!"
Tomorrow it’s one month since Marks and Spencer started containment, it’s also their financial results day.
Online ordering still down, all recruitment stopped, Palo-Alto VPNs still offline.
TCS have been linked to the Marks and Spencer breach, at least in part.
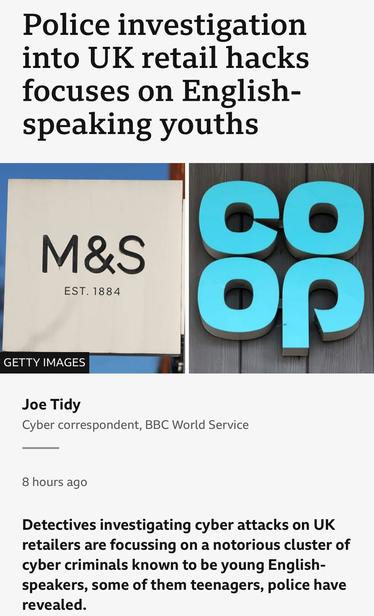
The NCA has confirmed on the record that the investigation into the M&S and Co-op hack is focused on English teenagers. I could toot the names of the people I think they’ll pick up, but won’t.
TCS has a security incident running around the M&S breach.
Interestingly the source claims TCS aren't involved in Co-op's IT - which is categorically false, they took over most of it while I worked there, including the helpdesk, and my team (SecOps) after I left.
https://www.ft.com/content/c658645d-289d-49ee-bc1d-241c651516b0
Insurance Insider say Co-op Group have no cyber insurance policy.
It’s got the insurance industry hard as they think they can ambulance chase other orgs with it.
While Co-op have restored every customer facing system and internal systems like recruitment and remote working, M&S still don't even have recruitment back.
I'm reliably told they paid the ransom, so they'll be target #1 basically forever with other ransomware groups now due to resiliency woes and willingness to pay.
https://www.bbc.co.uk/news/articles/c23mz5eg091o
This Daily Mail piece about security leaders thinking work-from-home means they will be crippled is horseshit, I'm not linking it.
They've taken a survey about how security people think their businesses couldn't survive ransomware, and linked it to working from home. WFH isn't the problem: business IT and resilience being built on quicksand is the problem.
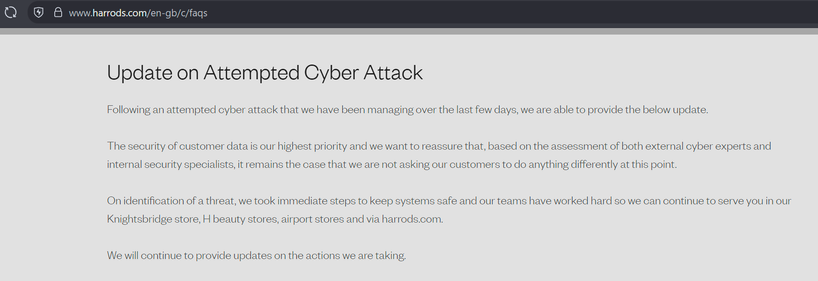
Co-op say they have largely completed recovery, and have removed the cyber attack banner and statement from their website
https://www.retailgazette.co.uk/blog/2025/06/co-op-cyber-attack/
I think they did a great job. They do call it a "highly sophisticated attack", which, frankly.. isn't true and may come out in open court later if the suspects are ever caught.
6 weeks from containment to "near full" recovery, for statto nerds like me who track this stuff.
M&S had their ransomware incident communicated via internal email - from the account of a staff member who works for TCS.
The way TCS work is you give them accounts on your AD.
Marks and Spencer have started partial online shopping again.
For statto nerds, around 7 weeks from containment to partial recovery
TCS have told shareholders their systems were not compromised in the hack of M&S.
As an explainer here (not in the article): TCS IT systems weren't compromised. Their helpdesk service (they're AD admins at M&S) was used to gain access to M&S. They manage M&S IT systems.
https://www.reuters.com/business/media-telecom/indias-tcs-says-none-its-systems-were-compromised-ms-hack-2025-06-19/
Latest Marks and Spencer update is pretty crazy.
M&S haven't been able to supply sales data - so the British Retail Consortium (BRC) - used by the UK government as as economic indicator - basically made up figures for M&S and didn't tell people they had done this.
https://www.telegraph.co.uk/business/2025/06/24/retail-lobby-group-accused-of-ms-cyber-cover-up/
@GossiTheDog I'd be very curious to know what the breakdown is between TCS dropping the ball and lying about it and M&S/Co-op not actually insisting on adequate procedure.
It's not terribly uncommon for people to only care about time-to-resolution with some lip service to user satisfaction when it comes to helpdesk metrics; and tacitly discourage things that are slow and unpleasant like hassling people for ID, at least until that becomes a visibly terrible idea.
"M-SThrowaway" might indicate M&S?
Or is that too obvious or deliberate obfuscation? 🙂🤷♂️
@GossiTheDog as someone who has been subjected to Tata on multiple occasions going back over a decade?
This isn't nearly spicy enough. I don't even describe them as a 'body shop' because they'd gladly route you to a corpse and try to charge extra for '24x7 coverage.'
When one employer did a basic security audit of their helpdesk services, Tata failed so severely that the contract was pulled for cause before the audit was even completed. They moved it all back in-house.
@GossiTheDog and lo, I found my notes! And, hooboy, hang onto your hats kiddos. Things they failed at (which caused me work):
- resetting passwords without verifying identities
- removing 2FA from accounts (not allowed period; there was a procedure)
- removing or updating 2FA without verifying identities (so a LOT of 2FAs had to be assumed compromised)
- adding users to groups directly instead of directing them to the appropriate request
@GossiTheDog The root problem here isn't that TCS are shockingly bad (they are, just about everyone knows that).
The root problem is that "management decisions" constantly overrule those that raise concerns about their service and tell any remaining internal IT and security staff to "deal with it as best you can."
I'm very much of the view that, yes, the outsourced provider can be the cause of an incident, they can provide a shockingly bad service, they can cost your business millions of pounds. But the decision to continue to use them when you already know this is a real possibility - that's a decision by senior management within the company. That's on you.
@Cyberoutsider @GossiTheDog Totally agree. You can outsource the work but never the accountability.
Here is (yet another) example of risk management failures, the management under cost pressures find affordable solutions, celebrated for cost savings but the implicit risks are not understood nor uncovered during sourcing process.
There are ways to compensate however there is any way a significant risk trade off that needs to be made consciously, rather than implicitly like today.
(Experience from enterprise offshore outsourcing +15 years)
This is epically bad for TCS. Good work.
@GossiTheDog Interesting. I don't have the background on this specific attack, but I'm reminded of the Target credit card theft. An HVAC company near me was the point of entry for the attackers; they had high-access keys to Target's intranet because they install and maintain shopping-mall-grade HVAC and can remote-override it for maintenance and schedule reasons (nation-scale chain stores with giant footprints save not-inconsequential money on things like "Don't power up the HVAC to normal capacity on days nobody is here").
They had the keys on the same machine running their webserver.
(Meanwhile, Target actually did get an SEC slap-on-the-wrist for one specific thing: the HVAC intranet piece wasn't firewalled from the financial transactions and cash register source code pieces).
If it is the case then the leaders of businesses like M&S who outsource these services to the lowest cost providers should also be held to account
It’s typical of British business management to know the cost of technology but not the value of it
I do not work for either company. Nevertheless, I can corroborate these comments, but not on a public forum. Not much interested in a private forum either. I'll just say that insider threat analysis and mitigation is VERY important when TCS is something you are forced to use.
@GossiTheDog K. Krithivasan, also known as Krithi, aka the face of quality IT, that you can trust.
Hash tag
These Indian, "IT", call centers probably do double time as scamming operations.
Hilarious twist would be that it was an inside job, faked to look like a compromise.