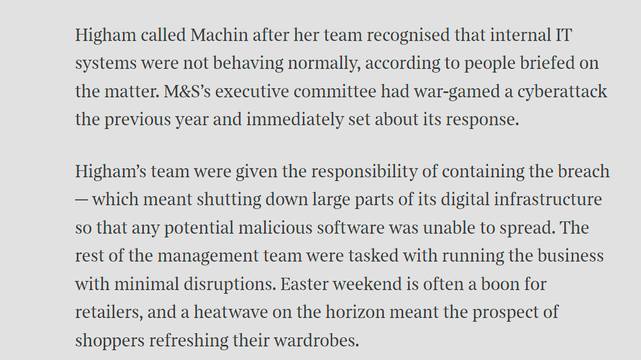
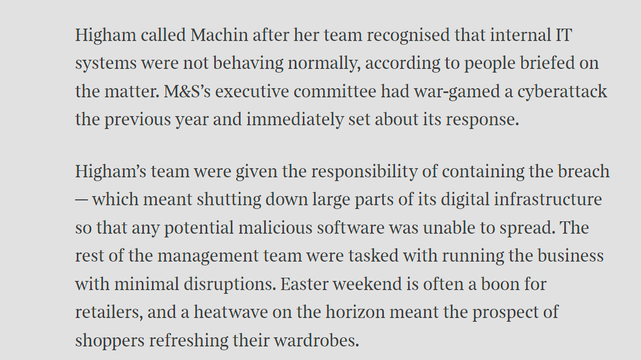
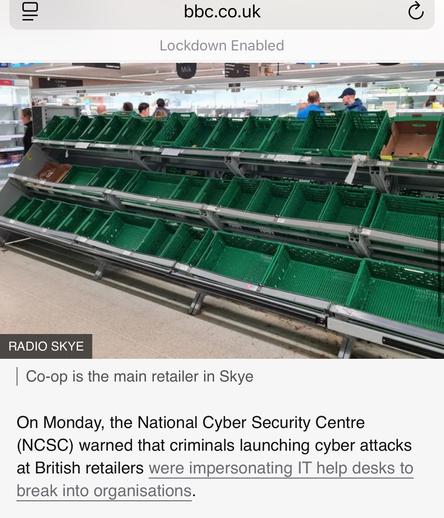
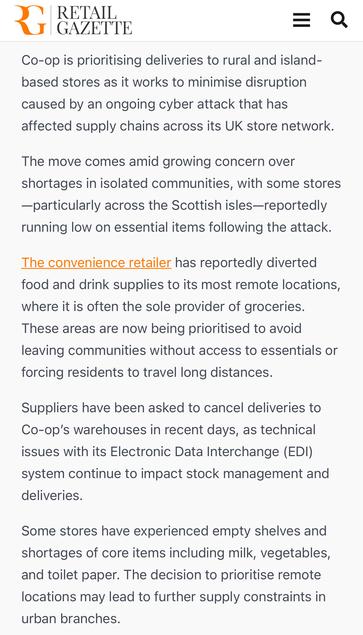
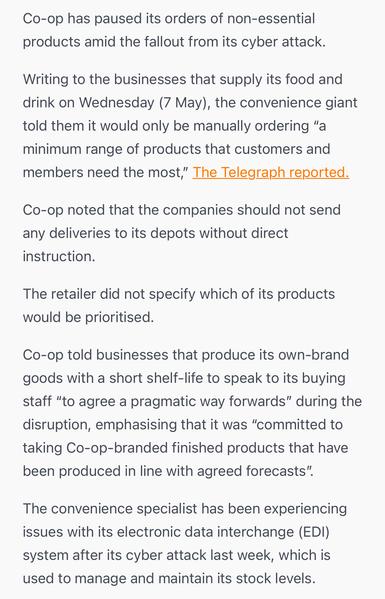
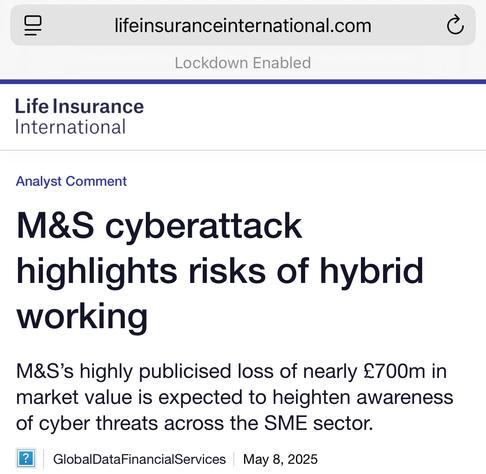
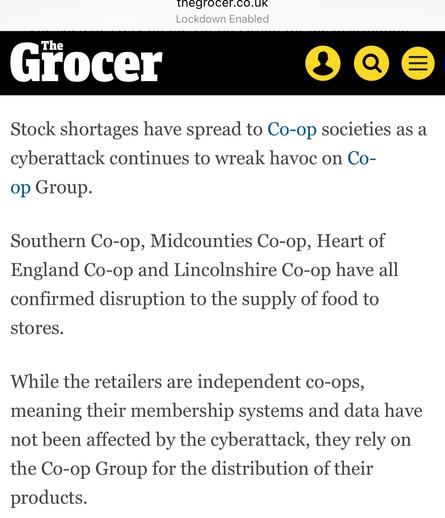
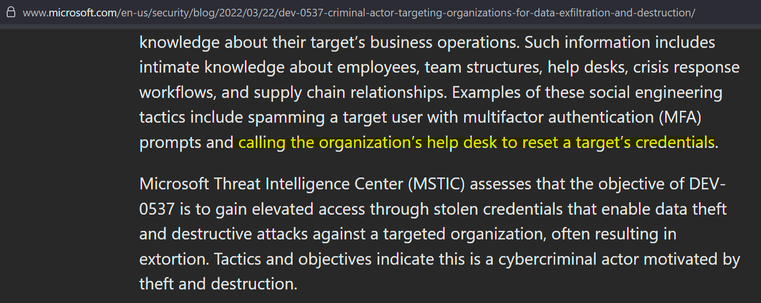
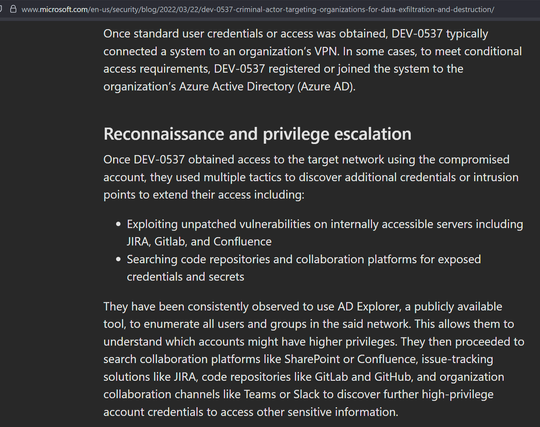
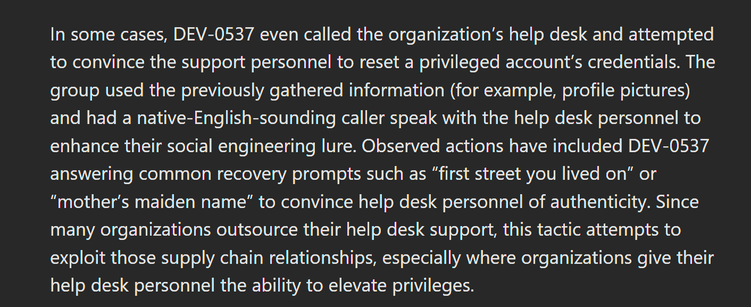
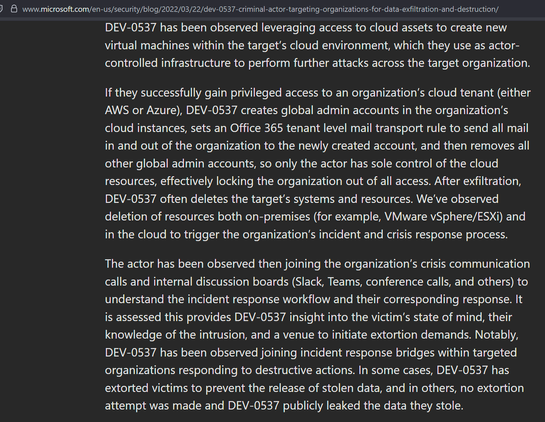
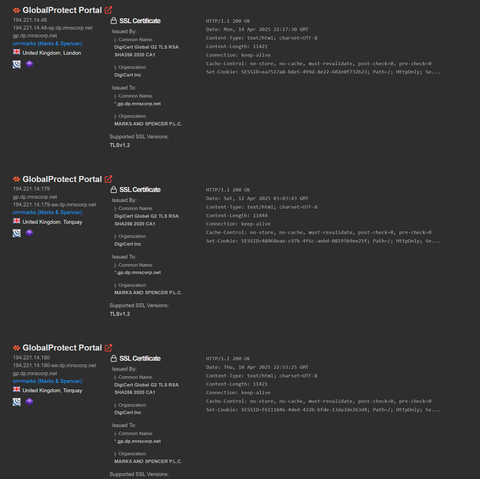
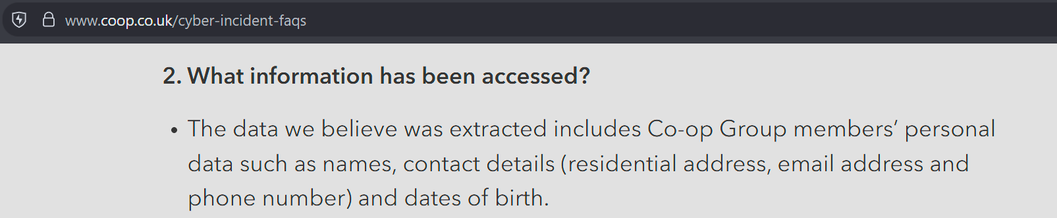
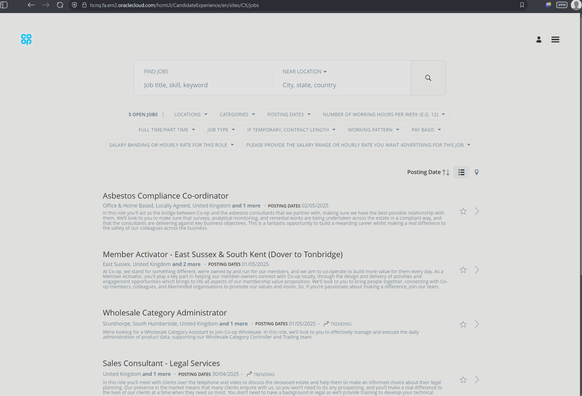
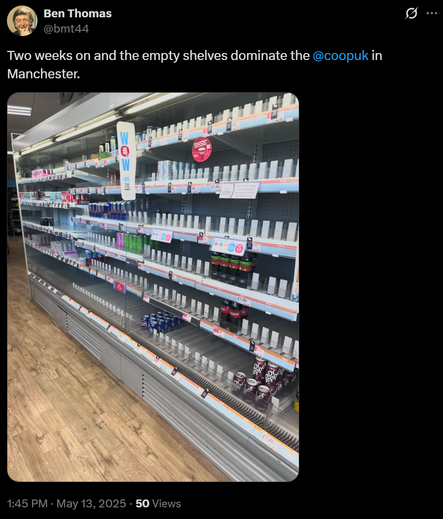
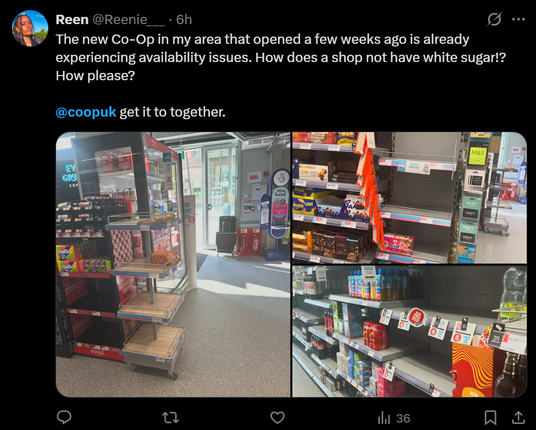
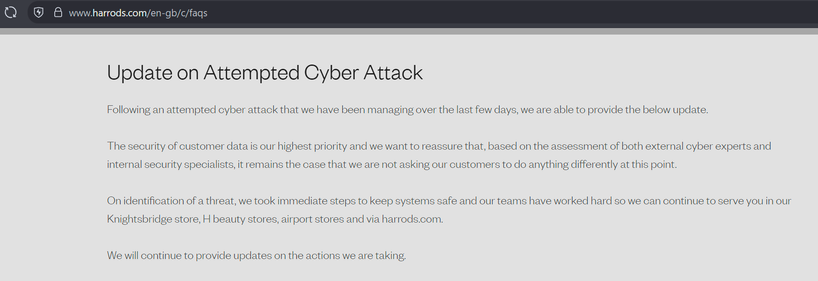
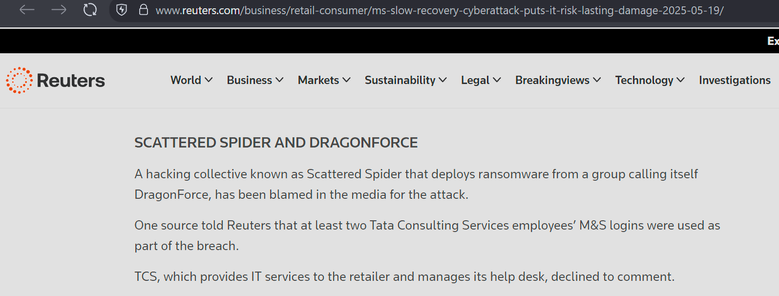
Sunday Times has a piece looking into ransomware incident at Marks and Spencer. It's pretty good, goes into their contain and eradicate focus.
"By shutting down parts of the IT estate, Higham’s team had worked to prevent the attack from spreading, but had also stopped parts of its digital operations from functioning. This was considered a worthy trade-off."
One error in the article - lack of recovery doesn't mean no ransomware paid. Paying is not quick restoration.
https://www.thetimes.com/business-money/companies/article/m-and-s-cyber-attack-ms-klrnxvwq6