The Times reports M&S were breached through a contractor and that human error is to blame. (Both M&S and Co-op use TCS for their IT Service Desk).
The threat actor went undetected for 52 hours. (I suspect detection was when their ESXi cluster got encrypted).
M&S have told the Times they had no “direct” communication with DragonForce, which is code for they’re using a third party to negotiate - standard practice.
https://www.thetimes.com/uk/technology-uk/article/m-and-s-boss-cyber-attack-7d9hvk6ds
M&S looks to be moving to reposition their incident as a third party failure, which I imagine will help redirect some of the blame (they present their financial results during the week to investors): https://www.bbc.co.uk/news/articles/cpqe213vw3po
Both M&S and Co-op outsourced their IT, including their Service Desk (helpdesk), to TCS (Tata) around 2018, as part of cost savings.
There's nothing to suggest TCS itself have a breach btw.
Basically, if you go for the lowest cost helpdesk - you might want to follow the NCSC advice on authenticating password and MFA token resets.
I've put a 3 part deep dive blog series coming out probably next week called Living-Off-The-Company, which is about how teenagers have realised large orgs have outsourced to MSPs who follow the same format of SOP documentation, use of cloud services etc. Orgs have introduced commonality to surf.
"Cyber analysts and retail executives said the company had been the victim of a ransomware attack, had refused to pay - following government advice - and was working to reinstall all of its computer systems."
Not sure who those analysts are, but since DragonForce haven't released any data and M&S won't comment other than to say they haven't had any "direct" contact with DragonForce, I wouldn't make that assumption.
There's also a line in the article from an cyber industry person saying "if it can happen to M&S, it can happen to anyone" - it's ridiculous and defeatist given Marks and Spencer haven't shared any technical information about how it happened, other than to tell The Sunday Times it was "human error"
The Air Safety version of cyber industry would be a plane crashing into 14 other planes, and industry air safety people going "Gosh, if that can happen to British Airways it could happen to anybody!"
Tomorrow it’s one month since Marks and Spencer started containment, it’s also their financial results day.
Online ordering still down, all recruitment stopped, Palo-Alto VPNs still offline.
TCS have been linked to the Marks and Spencer breach, at least in part.
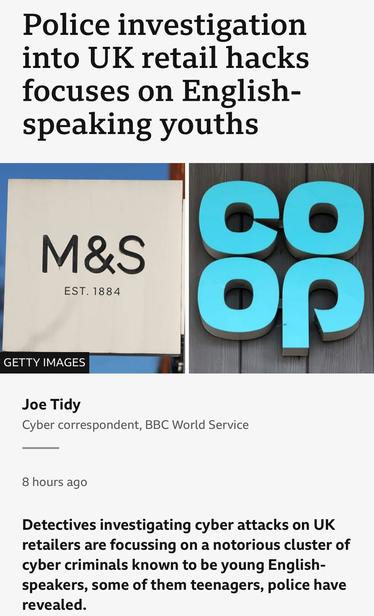
The NCA has confirmed on the record that the investigation into the M&S and Co-op hack is focused on English teenagers. I could toot the names of the people I think they’ll pick up, but won’t.
TCS has a security incident running around the M&S breach.
Interestingly the source claims TCS aren't involved in Co-op's IT - which is categorically false, they took over most of it while I worked there, including the helpdesk, and my team (SecOps) after I left.
https://www.ft.com/content/c658645d-289d-49ee-bc1d-241c651516b0
Insurance Insider say Co-op Group have no cyber insurance policy.
It’s got the insurance industry hard as they think they can ambulance chase other orgs with it.
While Co-op have restored every customer facing system and internal systems like recruitment and remote working, M&S still don't even have recruitment back.
I'm reliably told they paid the ransom, so they'll be target #1 basically forever with other ransomware groups now due to resiliency woes and willingness to pay.
Take something from the shelf and when you reach the checkout, it costs twice as much! Nice!
Which in the UK would be a criminal offence (under the law as it currently stands).
@GossiTheDog This stuff is brilliant. Based on e-paper and runs on Zigbee.
And they can raise the prices between you picking things off the shelf and going through the checkout and you'll have no proof that it was offered at a lower price.
@GossiTheDog
@GossiTheDog Want to guess how much of my IT leadership career has been focused on building in-house expertise and dialing back the presence of MSPs?
Enough that it's made for a pretty good living...
@GossiTheDog when I got my business degree, one of my management profs said that the instant you outsource, you give up control. To the service provider, you move from income to liability on the balance sheet because you now are costing them money, and to eke out any profit they need to cut costs related to providing service to you.
Thus you get all this *gestures vaguely*
@GossiTheDog I would love for IT to publish accident investigation reports in the same way as aviation.
No blame, no liability, no finger pointing, just lessons for everyone to learn and hopefully avoid the same.
(I know there have been some like the Irish Health Service that were excellent.)
@GossiTheDog yeah, breach the "low cost" IT outsourcer - whose staff feel little connection or affinity with the corporate customer - and *bingo* you hit the jackpot 🎰 with multiple corporate accounts to ransom.
How's that "low cost IT outsourcing" looking now?
1. Personnel is not allowed to store passwords.
2. Must use unique passwords for every service.
3. Passwords must rotate every X days.
4. Only sanctioned apps are allowed.
5. No password manager is sanctioned or installed by default.
@GossiTheDog I recall it was a "TCS_80_ip" list in Entra Id marked "Trusted"/"MFA exempt" that contained 80 ranges from /15 to /24...
Yet happily pivoting through 3 layer deep RDP to get to a system to manage