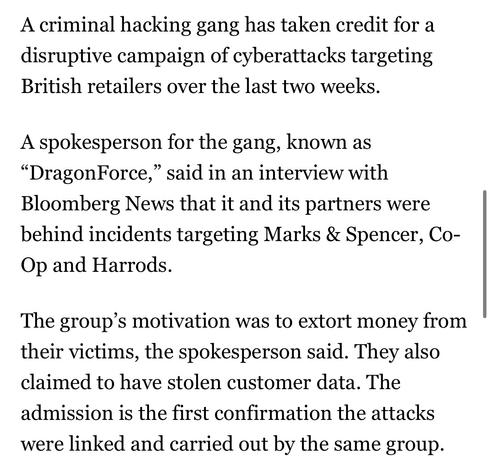
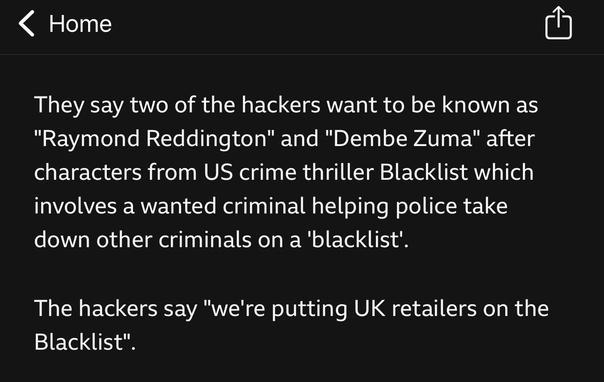
DragonForce Ransomware Cartel are claiming credit for attacks on Marks and Spencer, Co-op and Harrods and say more victim orgs are coming https://www.bloomberg.com/news/articles/2025-05-02/-dragonforce-hacking-gang-takes-credit-for-uk-retail-attacks
I'm going to make this the new ongoing megathread for DragonForce Ransomware Cartel's attack on UK retailers as they're all connected.
Why it matters: these are some of the UK's largest retailers, think Target or some such in a US sense.
Prior threads
M&S: https://cyberplace.social/@GossiTheDog/114381946765071799
Co-op: https://cyberplace.social/@GossiTheDog/114426688834113446
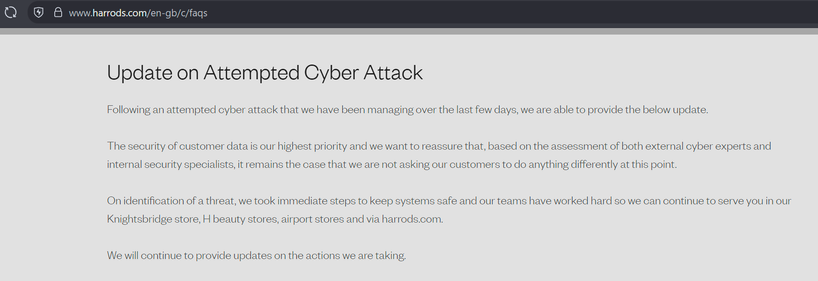
Harrods:
https://cyberplace.social/@GossiTheDog/114433519351165250
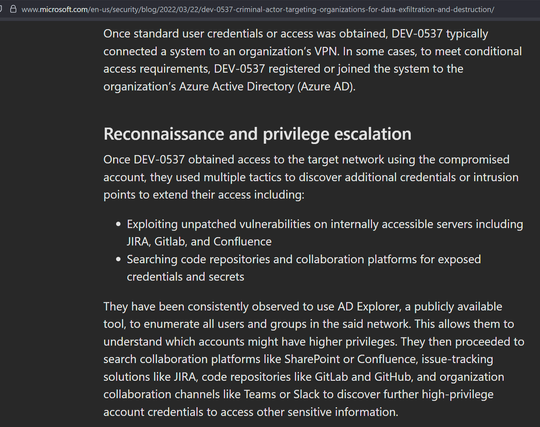
The individuals operating under the DragonForce banner are using social engineering for entry.
Defenders should urgently make sure they have read the CISA briefs on Scattered Spider and LAPSUS$ as it's a repeat of the 2022-2023 activity.
Links: https://www.cisa.gov/sites/default/files/2023-08/CSRB_Lapsus%24_508c.pdf
https://www.cisa.gov/sites/default/files/2023-11/aa23-320a_scattered_spider_0.pdf
I would also suggest these NCSC guides on incident management: https://www.ncsc.gov.uk/collection/incident-management
and effective cyber crisis comms: https://www.ncsc.gov.uk/guidance/effective-communications-in-a-cyber-incident
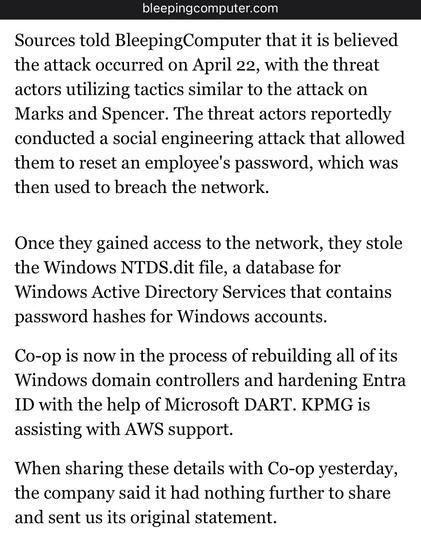
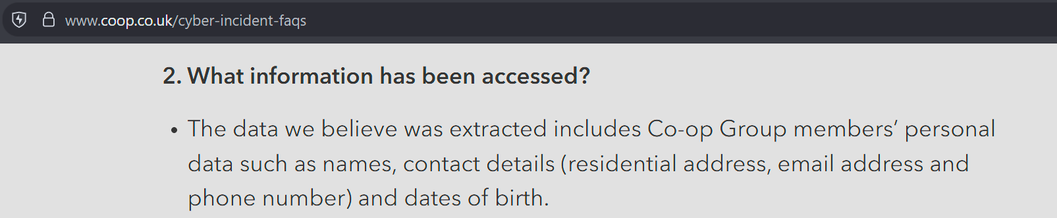
Co-op Group have now admitted a significant amount of member (customer) information has been stolen by DragonForce Ransomware Cartel, saying they "accessed data relating to a significant number of our current and past members" - around 20 million people. The Membership database, basically. That includes home addresses and phone numbers etc.
Up until now Co-op hadn't even used the words cyber or threat actor, referring to an "IT issue" and "third party" in comms.
New by me - breaking down the attacks on UK highstreet retailers
Regarding IOCs around the UK retailer activity - there’s loads doing the rounds, and they’re almost all not useful.
Eg hundreds of dynamic VPN IPs from 2022. If you google them you’ll find them on vendor blogs from years ago for Scattered Spider - people are recycling in panic and passing around in panic.
Don’t hunt on random IOCs. IP addresses change. Strengthen foundational controls. Review sign in logs for abnormal activity etc.
Bleeping Computer have more on the Co-op breach https://www.bleepingcomputer.com/news/security/co-op-confirms-data-theft-after-dragonforce-ransomware-claims-attack/
One of M&S’ biggest suppliers have said they have reverted to pen and paper for orders due to M&S lacking IT.
Additionally, M&S staff are raising concern about how they will be paid due to lack of IT systems.
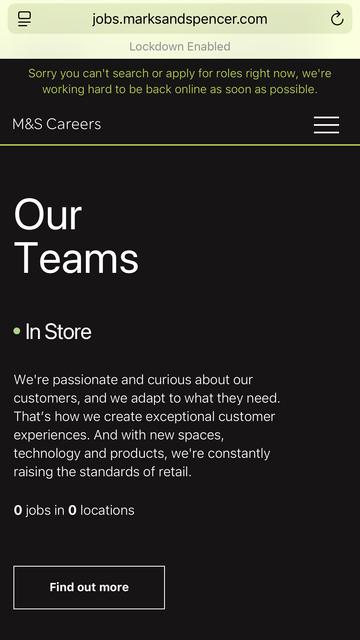
M&S are over a week into a ransomware incident and still don’t have their online store working.
Here's the ITV News report anyhoo, logline: "ITV News understands the the ongoing cyberattack faced by the supermarket has worsened since Friday, impacting the ordering system, drivers and warehouse staff."
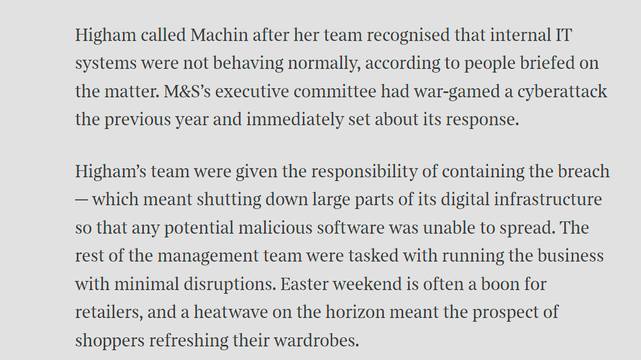
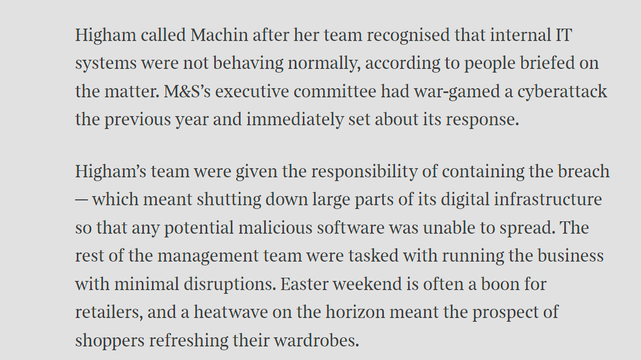
Sunday Times has a piece looking into ransomware incident at Marks and Spencer. It's pretty good, goes into their contain and eradicate focus.
"By shutting down parts of the IT estate, Higham’s team had worked to prevent the attack from spreading, but had also stopped parts of its digital operations from functioning. This was considered a worthy trade-off."
One error in the article - lack of recovery doesn't mean no ransomware paid. Paying is not quick restoration.
https://www.thetimes.com/business-money/companies/article/m-and-s-cyber-attack-ms-klrnxvwq6
Great NCSC piece by @ollie_whitehouse
I’d add - block by Entra policy specifically High risk logins (below is too FP prone), and SOC monitor them. SOC playbook = account probably compromised. How?
https://www.ncsc.gov.uk/blog-post/incidents-impacting-retailers
Sky News quote a source in M&S head office saying Marks and Spencer have no ransomware incident plan so they are making it up as they go along apparently, with staff sleeping in the office and communicating via WhatsApp.
M&S dispute this, saying they have robust business continuity plans.
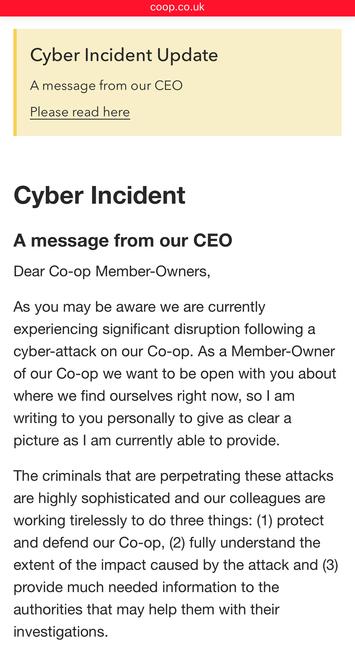
Co-op Group appear to be trying to course correct with their cyber incident comms.
They’re calling it a cyber incident now, and have put a statement on the front page of their website, along with an FAQ. They haven’t yet emailed members (they should). Edit: they’ve started emailing members.
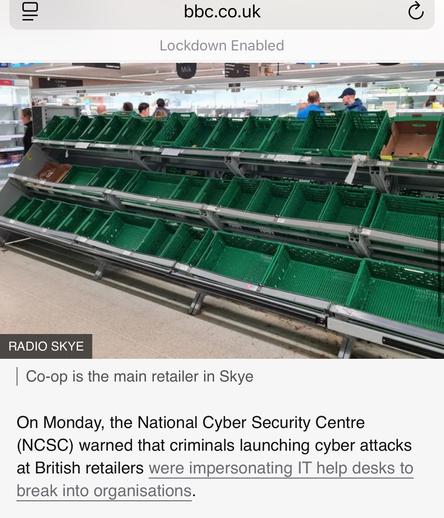
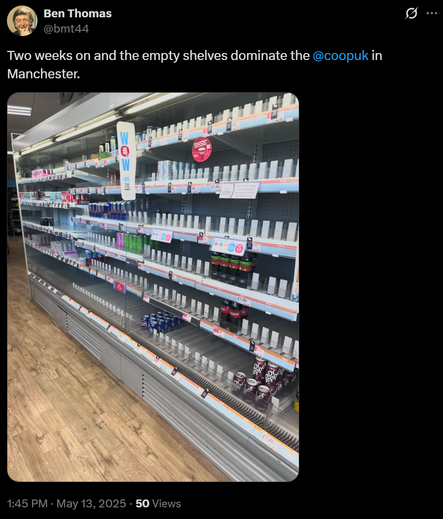
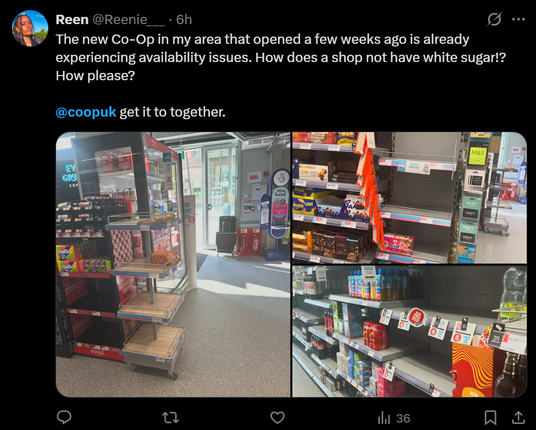
People are also taking to social media to post pictures of apparently emptying store shelves.
The Co-op website claims it is down to "technical issues".
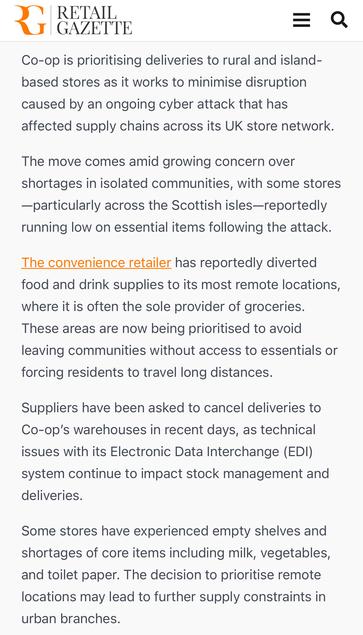
Co-op Group are redirecting supplies from their urban stores to remote and island locations due to stock shortages.
The article mentions their EDI platform is suffering “technical issues”. https://www.retailgazette.co.uk/blog/2025/05/co-op-reroutes-stock/
I just did a Shodan Safari on Co-op - basically all their Windows and Linux systems in their core DCs at network boundary are down, it's not just EDI. It's been like that for just under a week, prior to that things were still online.
I feel really bad for them as it's a great org. Also their CEO is basically the only one who stood up like this for trans people.
https://www.telegraph.co.uk/business/2025/05/04/ill-protect-trans-people-to-the-end-vows-co-op-boss/
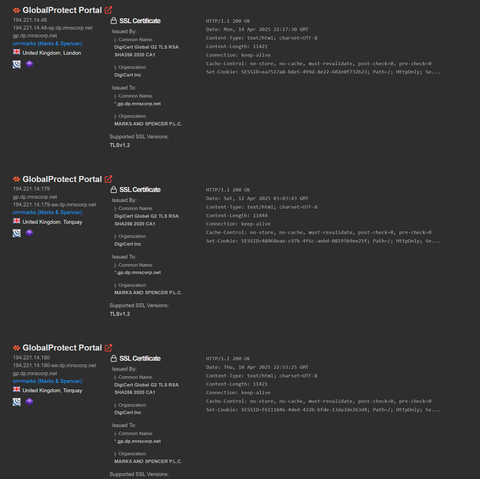
If you're wondering about Marks and Spencer - I just did a Shodan Safari of their network boundary, Palo-Alto GlobalProtect VPN remote access access is still offline, 15 days later.
Online orders are still not working, and the store stock checker is disabled now.
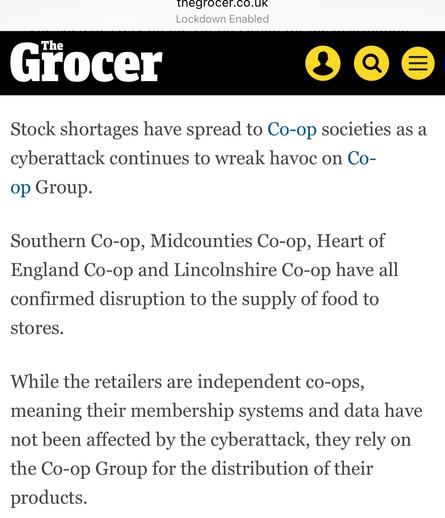
The Grocer reports 4 regional Co-ops, who aren’t part of Co-op Group, are suffering stock shortages as they are supplied by Co-op Group.
They expect customers to start to see availability issues on shelves in the coming days.
For orgs looking for defence tips for the attacks on UK retailers, this blog from 2022 about the UK teenagers in LAPSUS$ has relevance.
As a plot twist - not documented anywhere online, but LAPSUS$ first attacks in 2021 were against UK high street retailers.

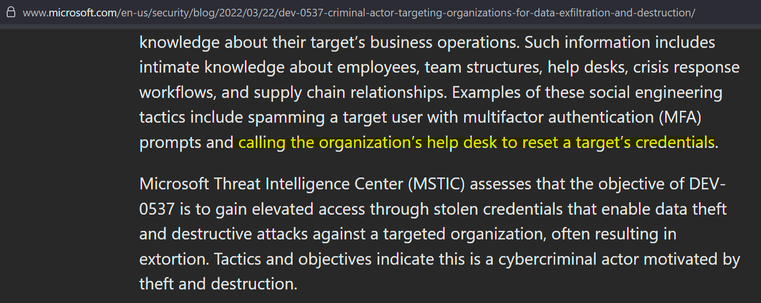
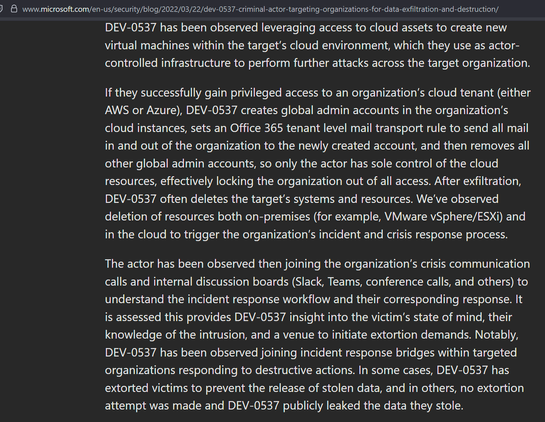
DEV-0537 criminal actor targeting organizations for data exfiltration and destruction | Microsoft Security Blog
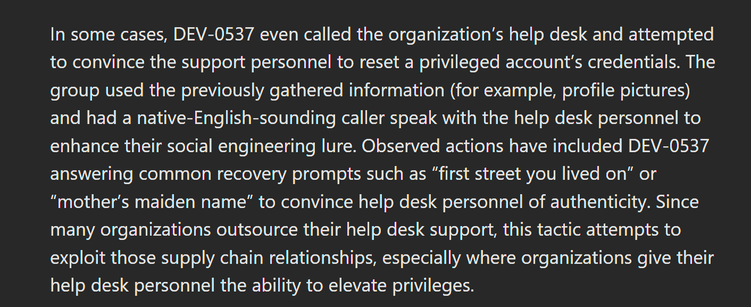
The activity we have observed has been attributed to a threat group that Microsoft tracks as DEV-0537, also known as LAPSUS$. DEV-0537 is known for using a pure extortion and destruction model without deploying ransomware payloads.
Co-op Group have provided some more detail about what it’s doing about remote lifeline stores (ones where they’re the main/only retailer on an island):
“From Monday, 12 of the most remote lifeline stores will receive treble the volume of available product, and another 20 lifeline stores will get double the volume.” https://www.bbc.com/news/articles/c071e7x80djo
This ITV News report linking the Co-op and M&S breaches to SIM swapping is not accurate, no source given. https://www.itv.com/news/2025-05-12/sim-swap-fraud-rises-by-1000-as-criminals-exploit-two-factor-authentication
They also have a report today saying Co-op stores are restocked, which is also not accurate - that one is sourced from Co-op, but obviously doesn’t stack up to looking in Co-op stores.
If anybody is wondering, all of Marks and Spencer's Palo-Alto GlobalProtect VPN boxes are still offline, 3 weeks later. Pretty good containment method to keep attackers out.
Co-op's VDE environment is still down, too.
https://cyberplace.social/@GossiTheDog/114399017367179104
Co-op's AGM is this weekend, and M&S yearly results and investor contact are next week.
Gonna be awkward for different reasons, e.g. Co-op is member (customer) owned, so the people's data Co-op had stolen are effectively the shareholders and are invited.
The Grocer reports Nisa and Costcutter are running out of fruit & veg, fresh meat and poultry, dairy products, chilled ready meals, snacks and desserts.
Nisa and Costcutter are supplied by Co-op Wholesale, which is dependent on Co-op Group.
“It’s really poor. I feel bad for them but what makes it worse is their hush-hush mentality about it. There’s no proper level of communication and we get random updates.”
Co-op Wholesale claim there are no problems. https://www.thegrocer.co.uk/news/nisa-and-costcutter-hit-by-stock-shortages-amid-co-op-cyberattack/704393.article
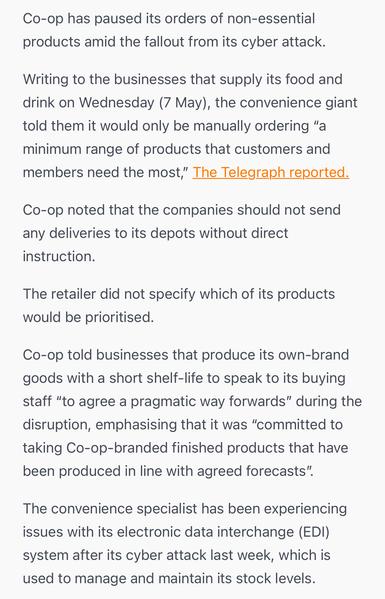
Co-op Group have told their suppliers that "systemic-based orders will resume for ambient, fresh, and frozen products commencing Wednesday 14 May". They say forecasting system will still be impacted.
https://www.thegrocer.co.uk/news/co-op-to-get-systems-back-on-track-after-cyberattack/704425.article
Co-op Group say they have exited containment and begun recovery phase https://www.theguardian.com/business/2025/may/14/co-op-cyber-attack-stock-availability-in-stores-will-not-improve-until-weekend
Marks and Spencer are still in containment
If you want figures for your board to set expectations in big game ransomware incidents, Co-op containment just over 2 weeks, M&S just over 3 weeks so far - recovery comes after.
In terms of external assistance, Co-op have Microsoft Incident Response (DART), KPMG and crisis comms. M&S have CrowdStrike, Microsoft, Fenix and crisis comms.
The threat actor at Co-op says Co-op shut systems down, which appears to have really pissed off the threat actor. This was the right, and smart, thing to do.
While I was at Co-op we did a rehearsal of ransomware deployment on point of sale devices with the retail team, and the outcome was a business ending event due to the inability to take payments for a prolonged period of time. So early intervention with containment was the right thing to do, 100%.
The quote
> They torched shareholder value
made me laugh
they have no idea what the Coop is
Just glad some of the lessons sank in....
Confident on containment within 2 weeks?
Ambient is shop-speak for stuff that is kept at room temperature. So biscuits, tea and coffee, tinned stuff, etc.
@GossiTheDog, TP;DR.
(Too portrait; didn't watch.)
@GossiTheDog the thieves could probably show up at the AGM and present themselves as a member, since they have access to all the information the Co-Op has on it's membership...number, address, etc.
Short of checking govt. ID or requiring a hard copy of the meeting invite that was mailed to their address. Even then, the thieves might've gotten away with that too.
@johnefrancis @GossiTheDog
Members who wanted to attend were supposed to indicate this on the agm voting form, which closed midday yesterday. I might have tried, but forgot to go back to it until too late..
I've not had any emails from coop about this, despite being a member. Nor from M&S, though I'm only registered on their app. (I can also continue to ignore Harrods, never having used them!)
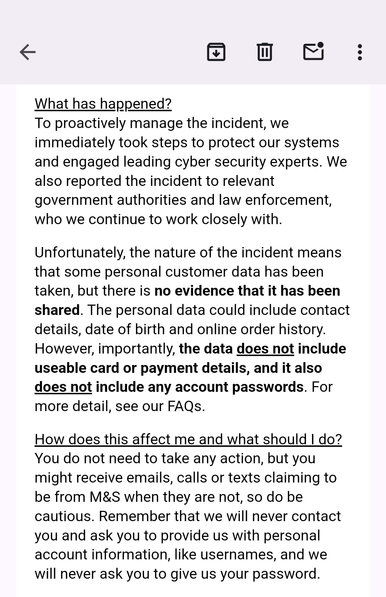
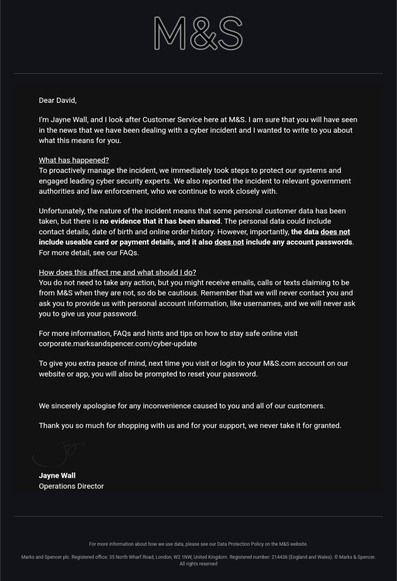
And 45 mins later I get an email from M&S. Nice of them to reassure us that none of the stuff I can change, like bank cards, was stolen. Only the things I can't change, like date of birth.
@GossiTheDog Incident response specialists the world over wince into their keyboards.
This is another object lesson in how not to do it. It'll be taught to students in future.
@GossiTheDog I can only hope this data breach is the kick up the arse needed to abolish the common practice of using date of birth as an (immutable!) security password. Once it’s public knowledge it’s beyond useless… it’s a liability. Especially in banks.
I will not be holding my breath on this one.
"Importantly, there is no evidence that the information has been shared," he added.
That's fine then, because that will never happen.
It would end not with a bang but with a hamper.
To be fair a lot of small producers do have farm shops, not just Jeremy flippin' Clarkson 😆🤷♂️