#Police disrupts #Rhadamanthys, #VenomRAT, and #Elysium #malware operations

Police disrupts Rhadamanthys, VenomRAT, and Elysium malware operations
Law enforcement authorities from 9 countries have taken down 1,025 servers used by the Rhadamanthys infolstealer, VenomRAT, and Elysium botnet malware operations in the latest phase of Operation Endgame, an international action targeting cybercrime.
Lees tip -> Operatie Endgame schakelt grote cybernetwerken uit | In Operatie Endgame zijn grote cybernetwerken uitgeschakeld, met aanhoudingen, neergehaalde servers en verstoring van infostealers, botnets en RAT’s door internationale samenwerking. | #botnet #cybercrime #Europol #hacking #infostealers #internationalesamenwerking #OperatieEndgame #politie #ransomware #Rhadamanthys #VenomRAT |
https://hbpmedia.nl/operatie-endgame-cybernetwerken-uitgeschakeld/
Operation Endgame: Son aşamada üç siber suç örgütü çökertildi
#venomrat #endgame #Rhadamanthys
https://webrecord.media/operation-endgame-son-asamada-uc-siber-suc-orgutu-cokertildi/

Operation Endgame: Son aşamada üç siber suç örgütü çökertildi
Uluslararası kolluk kuvvetleri koalisyonu, Operation Endgame'in son aşaması kapsamında Rhadamanthys infostealer, VenomRAT ve Elysium botnet kötü amaçlı yazılım operasyonları tarafından kullanılan 1000'den fazla sunucuyu etkisiz hale getirdi. 10-13 Kasım 2025 tarihleri arasında gerçekleştirilen ve Lahey'deki Europol merkezinden koordine edilen Operation Endgame'in son aşaması kapsamında 1'i Almanya'da, 1'i Yunanistan'da ve 9'u
Proofpoint is proud to have assisted law enforcement in the #OperationEndgame investigation that led to the November 13, 2025 disruption of #Rhadamanthys and #VenomRAT, both #malware used by multiple cybercriminals.
• Rhadamanthys: https://brnw.ch/21wXs1N
• VenomRAT: https://brnw.ch/21wXs1O
---
Since May 2024, Operation Endgame—a global law enforcement and private sector effort that includes Proofpoint—has significantly disrupted the #malware and #botnet ecosystem.
👉 #Europol called the May 2024 Operation Endgame actions “the largest ever operation against botnets.”
👉 In May 2025, additional malware families and their creators, including #DanaBot, were taken down.
---
Each disruption forces threat actors to adapt and invest time and resources to retool their attack chains.
With our unique visibility and leading detection capabilities, Proofpoint researchers will continue monitoring the threat landscape and provide insight into the biggest cyber threats to society.
https://www.europol.europa.eu/media-press/newsroom/news/end-of-game-for-cybercrime-infrastructure-1025-servers-taken-down

End of the game for cybercrime infrastructure: 1025 servers taken down – Operation Endgame’s latest phase targeted the infostealer Rhadamanthys, Remote Access Trojan VenomRAT, and the botnet Elysium | Europol
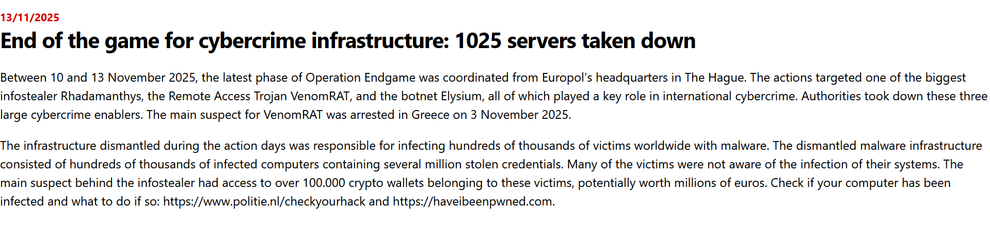
Between 10 and 14 November 2025, the latest phase of Operation Endgame was coordinated from Europol’s headquarters in The Hague. The actions targeted one of the biggest infostealers (Rhadamanthys), the Remote Access Trojan VenomRAT, and the botnet Elysium, all of which played a key role in international cybercrime. Authorities took down these three large cybercrime enablers. The main suspect for VenomRAT was also arrested in Greece on 3 November 2025.
👮 Operation « Endgame » (operation-endgame.com) #europol #malware #botnet #rhadamanthys #venomrat #threats [ https://europol.europa.eu/media-press/newsroom/news/end-of-game-for-cybercrime-infrastructure-1025-servers-taken-down ]
Many of the victims were not aware of the infection of their systems. Check if your Windows has been infected and what to do if so : [ https://www.politie.nl/checkyourhack ] & [ https://haveibeenpwned.com ]

End of the game for cybercrime infrastructure: 1025 servers taken down – Operation Endgame’s latest phase targeted the infostealer Rhadamanthys, Remote Access Trojan VenomRAT, and the botnet Elysium | Europol
Between 10 and 14 November 2025, the latest phase of Operation Endgame was coordinated from Europol’s headquarters in The Hague. The actions targeted one of the biggest infostealers (Rhadamanthys), the Remote Access Trojan VenomRAT, and the botnet Elysium, all of which played a key role in international cybercrime. Authorities took down these three large cybercrime enablers. The main suspect for VenomRAT was also arrested in Greece on 3 November 2025.
And it's out!
End of the game for cybercrime infrastructure: 1025 servers taken down
Between 10 and 13 November 2025, the latest phase of Operation Endgame was coordinated from Europol’s headquarters in The Hague. The actions targeted one of the biggest infostealer Rhadamanthys, the Remote Access Trojan VenomRAT, and the botnet Elysium, all of which played a key role in international cybercrime. Authorities took down these three large cybercrime enablers. The main suspect for VenomRAT was arrested in Greece on 3 November 2025.
#OperationEndgame #rhadamanthys #infostealer #VenomRAT #Elysium
#RevengeHotels #VenomRAT
https://securelist.com/revengehotels-attacks-with-ai-and-venomrat-across-latin-america/117493/
🎣 Phishing Campaign
====================
🎯 Threat Intelligence
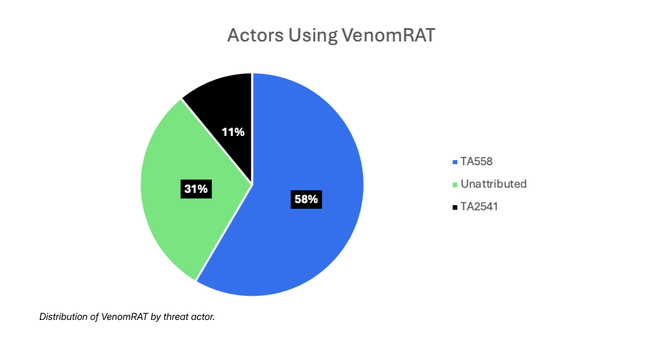
Executive summary: RevengeHotels, tracked as TA558, has launched a new campaign focused on targets in Latin America. The operation combines social‑engineering lures generated or refined with LLMs and a multi‑stage payload delivery that includes VenomRAT as a secondary implant.
Technical details: The research attributed to Kaspersky GReAT describes an initial infection vector using convincing lures (reports indicate use of large language models to craft messages and
attachments) followed by deployment of a malicious implant and a second loading step that delivers VenomRAT. Additional behaviours reported include USB spreading and anti‑kill mechanisms intended to maintain persistence and hinder remediation.
Analysis & impact: The group’s historical goal of payment‑card harvesting aligns with observed tooling and TTPs; VenomRAT provides remote access and data‑collection capabilities that enable payment‑card skimming and exfiltration. Use of LLMs to tailor lures increases phishing efficacy and may broaden victim scope across industries in the region.
Detection: Monitor for anomalous post‑delivery processes and new persistence artifacts, uncommon USB autorun or device enumeration activity, and network connections associated with known VenomRAT command‑and‑control patterns. Endpoint telemetry showing staged downloads after opening social‑engineering attachments is a high‑value detection signal. No precise IoCs were included in the supplied excerpt.
Mitigation: Enforce multi‑layer controls: block known malicious file types at mail gateways, apply strict device control policies for removable media, enforce EDR detections for process injection and persistence modification, and treat unsolicited attachments with elevated suspicion, especially those leveraging sophisticated social engineering likely crafted by LLMs.
References & caveats: Findings are derived from a Kaspersky GReAT report; technical artifacts and IoCs were not fully available in the supplied text. Further validation against full indicators is recommended.
🔹 RevengeHotels #VenomRAT #TA558 #LLM
🔗 Source: https://securelist.com/revengehotels-attacks-with-ai-and-venomrat-across-latin-america/117493/