It's been a bit quiet over the last 24 hours, but we've got one interesting story about a high-profile hacking group and a cybersecurity firm playing cat and mouse. Let's dive in:
ShinyHunters vs. Resecurity: Honeypot or Hack? 🎣
- The prominent ShinyHunters hacking group (also known as "Scattered Lapsus$ Hunters") claims to have breached cybersecurity firm Resecurity, alleging the theft of employee data, internal communications, threat intelligence, and client lists.
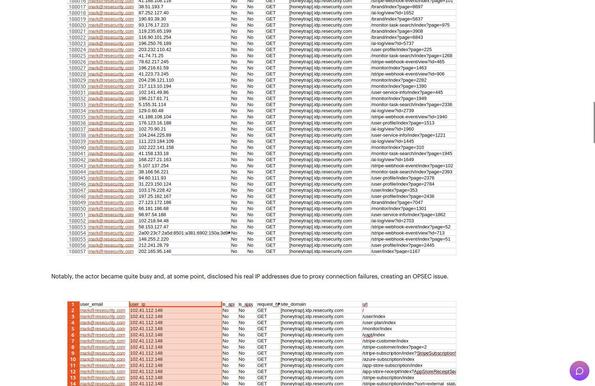
- Resecurity vehemently denies the breach, asserting that the systems accessed by ShinyHunters were a deliberately deployed honeypot filled with synthetic data, designed to attract and monitor the threat actors.
- The firm detailed how it observed the attackers' tactics, techniques, and infrastructure, collecting telemetry and even identifying attacker IP addresses, which it subsequently shared with law enforcement, leading to a subpoena request.
🤖 Bleeping Computer | https://www.bleepingcomputer.com/news/security/shinyhunters-claims-resecurity-hack-firm-says-its-a-honeypot/
#CyberSecurity #ThreatIntelligence #Honeypot #ShinyHunters #Resecurity #InfoSec #CyberAttack #IncidentResponse #ThreatActor