🛠️ Tool
===================
Opening:
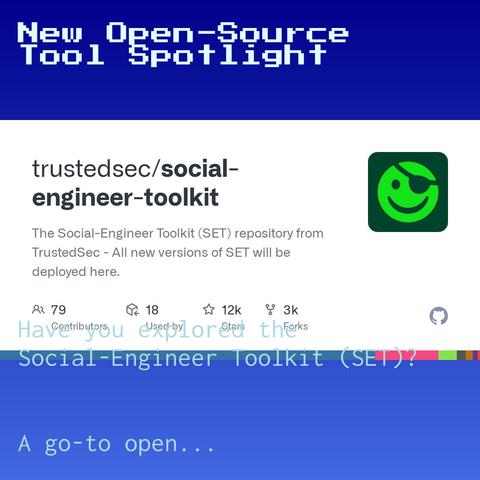
Wyrm is an open‑source post‑exploitation and Red Team framework released as v0.3 (Hatchling). The project is written entirely in Rust and positions itself as a modular C2 and implant ecosystem focused on covert HTTP(S) communications and runtime artifact hardening.
Key Features:
• Implant profile configuration: implants are driven by configurable profiles that adjust capabilities, anti‑sandbox behavior, and telemetry.
• Below‑TLS custom encryption: agents communicate over HTTP(S) but apply a custom encryption layer beneath TLS; packets are described as uniquely structured to resist decryption even under perimeter TLS inspection.
• Obfuscation and anti‑analysis: IOCs encrypted inside payloads to hinder YARA and static detection, with runtime efforts to obfuscate in‑memory artifacts.
• Dynamic payload generation and staging: C2 supports dynamic payload creation and serves staged resources (PDF, ZIP, binaries) to support phishing and initial access scenarios.
• Operator tooling and persistence: includes a terminal client for operator tasks, database‑backed logging with timestamps for reporting, and planned expansions of native Windows API commands.
Technical Implementation (conceptual):
• The implant and server are implemented in Rust, emphasizing memory safety and the opportunity to craft compact, performant binaries.
• Network communications rely on standard HTTP(S) flows with an additional custom encryption layer applied to payload packets prior to TLS or within the application layer, intended to defeat TLS inspection devices by altering packet semantics.
• Payloads and profiles appear to be templated such that operators can tune anti‑sandbox checks, user‑agent strings, and staged content behavior.
Use Cases:
• Red Team engagements requiring covert C2 over common HTTP traffic patterns.
• Purple Team exercises to validate detection capabilities for below‑TLS obfuscation and encrypted payload delivery.
• Penetration tests that require dynamic staging of social‑engineering artifacts and operator orchestration.
Limitations & Considerations:
• Project described as pre‑release and actively developing; documentation and contributor policies are evolving and the repo currently blocks direct contributions (issues/discussions preferred).
• The server component references a C2 directory and an install_server.sh asset; operators should note configuration and profile compatibility caveats described in release notes.
References:
• Roadmap targets through 1.0–4.0 and release notes accompany the project.
🔹 tool #post_exploitation #rust #redteam
🔗 Source: https://github.com/0xflux/Wyrm