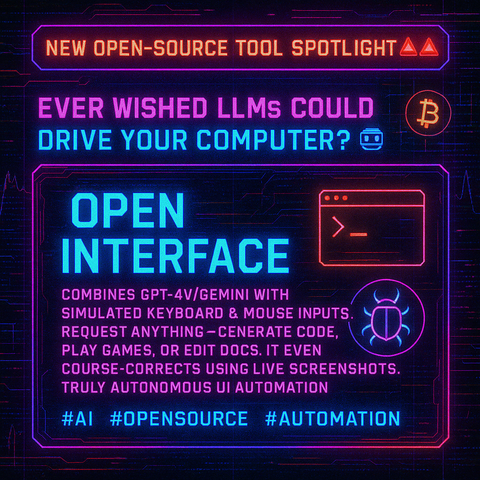
❓How secure are your Google Workspace groups? 🤔🔒
Gubble audits Google Groups settings to uncover risky configurations like "Anyone Can Join" or "External Members Allowed." Misconfigurations like these can expose sensitive data or enable phishing scenarios. Automate the checks before risks arise!
#GoogleWorkspace #SecOps #Cybersecurity
🔗 Project link on #GitHub 👉 https://github.com/LowOrbitSecurity/gubble
#Infosec #Cybersecurity #Software #Technology #News #CTF #Cybersecuritycareer #hacking #redteam #blueteam #purpleteam #tips #opensource #cloudsecurity
— ✨
🔐 P.S. Found this helpful? Tap Follow for more cybersecurity tips and insights! I share weekly content for professionals and people who want to get into cyber. Happy hacking 💻🏴☠️